Category: Uncategorized
-
Update Kali Linux to the latest software repository key
Kali Linux users might encounter errors when they update or download new software, exposing systems to security threats. A new repository key will eliminate those problems.Read More
-
What is a SYN flood DoS attack?
A SYN flood attack is a type of denial-of-service (DoS) attack on a computer server. This exploit is also known as a ‘half-open attack.’Read More
-

Scattered Spider Behind Cyberattacks on M&S and Co-op, Causing Up to $592M in Damages [email protected] (The Hacker News)
The April 2025 cyber attacks targeting U.K. retailers Marks & Spencer and Co-op have been classified as a “single combined cyber event.” That’s according to an assessment from the Cyber Monitoring Centre (CMC), a U.K.-based independent, non-profit body set up by the insurance industry to categorize major cyber events. “Given that one threat actor claimed…
-
Teleport Remote Authentication Bypass
What is the Vulnerability?Teleport security engineers have discovered a critical vulnerability affecting Teleport versions earlier than 17.5.2. This flaw allows remote attackers to bypass SSH authentication on servers running Teleport SSH agents, OpenSSH-integrated deployments, and Teleport Git proxy setups. Exploiting this vulnerability could enable unauthorized access to Teleport-managed systems by circumventing standard authentication controls. View…
-
Qilin Ransomware Adds “Call Lawyer” Feature to Pressure Victims for Larger Ransoms [email protected] (The Hacker News)
The threat actors behind the Qilin ransomware-as-a-service (RaaS) scheme are now offering legal counsel for affiliates to put more pressure on victims to pay up, as the cybercrime group intensifies its activity and tries to fill the void left by its rivals. The new feature takes the form of a “Call Lawyer” feature on the…
-
News brief: LOTL attacks, spoofed sites, malicious repositories
Check out the latest security news from the Informa TechTarget team.Read More
-

Iran’s State TV Hijacked Mid-Broadcast Amid Geopolitical Tensions; $90M Stolen in Crypto Heist [email protected] (The Hacker News)
Iran’s state-owned TV broadcaster was hacked Wednesday night to interrupt regular programming and air videos calling for street protests against the Iranian government, according to multiple reports. It’s currently not known who is behind the attack, although Iran pointed fingers at Israel, per Iran International. “If you experience disruptions or irrelevant messages while watching various…
-

6 Steps to 24/7 In-House SOC Success [email protected] (The Hacker News)
Hackers never sleep, so why should enterprise defenses? Threat actors prefer to target businesses during off-hours. That’s when they can count on fewer security personnel monitoring systems, delaying response and remediation. When retail giant Marks & Spencer experienced a security event over Easter weekend, they were forced to shut down their online operations, which account…
-
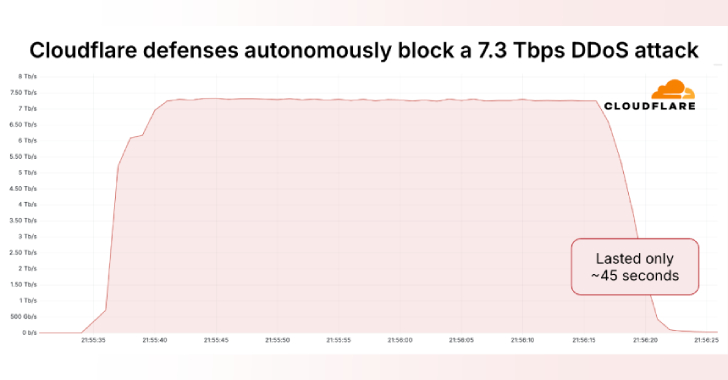
Massive 7.3 Tbps DDoS Attack Delivers 37.4 TB in 45 Seconds, Targeting Hosting Provider [email protected] (The Hacker News)
Cloudflare on Thursday said it autonomously blocked the largest ever distributed denial-of-service (DDoS) attack ever recorded, which hit a peak of 7.3 terabits per second (Tbps). The attack, which was detected in mid-May 2025, targeted an unnamed hosting provider. “Hosting providers and critical Internet infrastructure have increasingly become targets of DDoS attacks,” Cloudflare’s OmerRead More
-

67 Trojanized GitHub Repositories Found in Campaign Targeting Gamers and Developers [email protected] (The Hacker News)
Cybersecurity researchers have uncovered a new campaign in which the threat actors have published more than 67 GitHub repositories that claim to offer Python-based hacking tools, but deliver trojanized payloads instead. The activity, codenamed Banana Squad by ReversingLabs, is assessed to be a continuation of a rogue Python campaign that was identified in 2023 as…
