Category: Uncategorized
-
Kali vs. ParrotOS: Security-focused Linux distros compared
Network security doesn’t always require expensive software. Two Linux distributions — Kali Linux and ParrotOS — can help enterprises fill in their security gaps.Read More
-

Silver Fox APT Targets Taiwan with Complex Gh0stCringe and HoldingHands RAT Malware [email protected] (The Hacker News)
Cybersecurity researchers are warning of a new phishing campaign that’s targeting users in Taiwan with malware families such as HoldingHands RAT and Gh0stCringe. The activity is part of a broader campaign that delivered the Winos 4.0 malware framework earlier this January by sending phishing messages impersonating Taiwan’s National Taxation Bureau, Fortinet FortiGuard Labs said in…
-

Google Warns of Scattered Spider Attacks Targeting IT Support Teams at U.S. Insurance Firms [email protected] (The Hacker News)
The notorious cybercrime group known as Scattered Spider (aka UNC3944) that recently targeted various U.K. and U.S. retailers has begun to target major insurance companies, according to Google Threat Intelligence Group (GTIG). “Google Threat Intelligence Group is now aware of multiple intrusions in the U.S. which bear all the hallmarks of Scattered Spider activity,” John…
-
How to set up Windows Hello for Business step by step
Licensing for Windows Hello for Business is a simple process, but the setup involves making several decisions, including how to host the service, authentication types and more.Read More
-

Are Forgotten AD Service Accounts Leaving You at Risk? [email protected] (The Hacker News)
For many organizations, Active Directory (AD) service accounts are quiet afterthoughts, persisting in the background long after their original purpose has been forgotten. To make matters worse, these orphaned service accounts (created for legacy applications, scheduled tasks, automation scripts, or test environments) are often left active with non-expiring or stale passwords. It’s no surpriseRead More
-
Hard-Coded ‘b’ Password in Sitecore XP Sparks Major RCE Risk in Enterprise Deployments [email protected] (The Hacker News)
Cybersecurity researchers have disclosed three security flaws in the popular Sitecore Experience Platform (XP) that could be chained to achieve pre-authenticated remote code execution. Sitecore Experience Platform is an enterprise-oriented software that provides users with tools for content management, digital marketing, and analytics and reports. The list of vulnerabilities, which are yet to beRead More
-

Backups Are Under Attack: How to Protect Your Backups [email protected] (The Hacker News)
Ransomware has become a highly coordinated and pervasive threat, and traditional defenses are increasingly struggling to neutralize it. Today’s ransomware attacks initially target your last line of defense — your backup infrastructure. Before locking up your production environment, cybercriminals go after your backups to cripple your ability to recover, increasing the odds of a ransom…
-
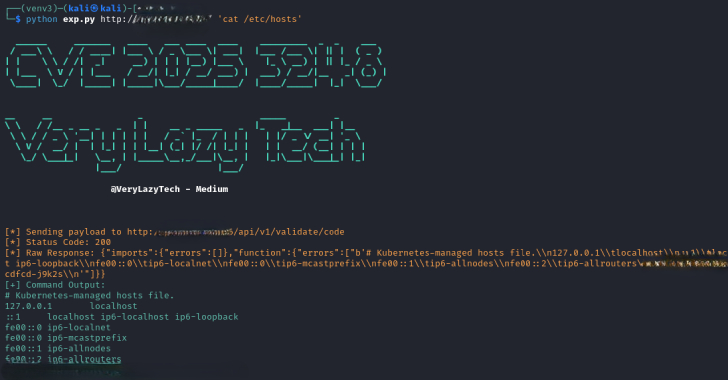
New Flodrix Botnet Variant Exploits Langflow AI Server RCE Bug to Launch DDoS Attacks [email protected] (The Hacker News)
Cybersecurity researchers have called attention to a new campaign that’s actively exploiting a recently disclosed critical security flaw in Langflow to deliver the Flodrix botnet malware. “Attackers use the vulnerability to execute downloader scripts on compromised Langflow servers, which in turn fetch and install the Flodrix malware,” Trend Micro researchers Aliakbar Zahravi, Ahmed MohamedRead More
-

TP-Link Router Flaw CVE-2023-33538 Under Active Exploit, CISA Issues Immediate Alert [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a high-severity security flaw in TP-Link wireless routers to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability in question is CVE-2023-33538 (CVSS score: 8.8), a command injection bug that could result in the execution of arbitrary system commands whenRead…
-

Meta Starts Showing Ads on WhatsApp After 6-Year Delay From 2018 Announcement [email protected] (The Hacker News)
Meta Platforms on Monday announced that it’s bringing advertising to WhatsApp, but emphasized that the ads are “built with privacy in mind.” The ads are expected to be displayed on the Updates tab through its Stories-like Status feature, which allows ephemeral sharing of photos, videos, voice notes, and text for 24 hours. These efforts are…
