Category: Uncategorized
-
News brief: Gartner Security and Risk Management Summit recap
Check out the latest security news from the Informa TechTarget team.Read More
-
Over 269,000 Websites Infected with JSFireTruck JavaScript Malware in One Month [email protected] (The Hacker News)
Cybersecurity researchers are calling attention to a “large-scale campaign” that has been observed compromising legitimate websites with malicious JavaScript injections. According to Palo Alto Networks Unit 42, these malicious injects are obfuscated using JSFuck, which refers to an “esoteric and educational programming style” that uses only a limited set of characters to write and execute…
-

Over 269,000 Websites Infected with JSFireTruck JavaScript Malware in One Month [email protected] (The Hacker News)
Cybersecurity researchers are calling attention to a “large-scale campaign” that has been observed compromising legitimate websites with malicious JavaScript injections. According to Palo Alto Networks Unit 42, these malicious injects are obfuscated using JSFuck, which refers to an “esoteric and educational programming style” that uses only a limited set of characters to write and execute…
-

Ransomware Gangs Exploit Unpatched SimpleHelp Flaws to Target Victims with Double Extortion [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday disclosed that ransomware actors are targeting unpatched SimpleHelp Remote Monitoring and Management (RMM) instances to compromise customers of an unnamed utility billing software provider. “This incident reflects a broader pattern of ransomware actors targeting organizations through unpatched versions of SimpleHelpRead More
-

CTEM is the New SOC: Shifting from Monitoring Alerts to Measuring Risk [email protected] (The Hacker News)
Introduction: Security at a Tipping Point Security Operations Centers (SOCs) were built for a different era, one defined by perimeter-based thinking, known threats, and manageable alert volumes. But today’s threat landscape doesn’t play by those rules. The sheer volume of telemetry, overlapping tools, and automated alerts has pushed traditional SOCs to the edge. Security teams…
-
How to write a risk appetite statement: Template, examples
A risk appetite statement defines acceptable risk levels for an organization. Here’s what it includes and how to create one, with examples and a downloadable template.Read More
-
How to deploy Windows LAPS for tighter security
Microsoft improved the feature that automates local administrator password management in Windows Server and the client OS. This tutorial explains the updates and how to set it up.Read More
-
CISO’s guide to building a strong cyber-resilience strategy
Cyber-resilience strategies that integrate BCDR, incident response and cybersecurity enable CISOs to build frameworks that help their organizations effectively handle cyberattacks.Read More
-

Apple Zero-Click Flaw in Messages Exploited to Spy on Journalists Using Paragon Spyware [email protected] (The Hacker News)
Apple has disclosed that a now-patched security flaw present in its Messages app was actively exploited in the wild to target civil society members in sophisticated cyber attacks. The vulnerability, tracked as CVE-2025-43200, was addressed on February 10, 2025, as part of iOS 18.3.1, iPadOS 18.3.1, iPadOS 17.7.5, macOS Sequoia 15.3.1, macOS Sonoma 14.7.4, macOS…
-
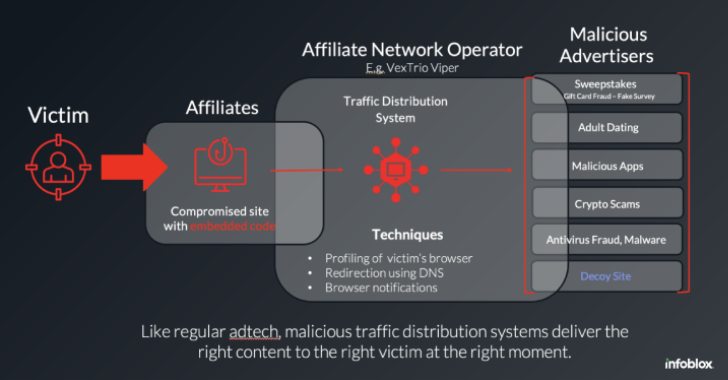
WordPress Sites Turned Weapon: How VexTrio and Affiliates Run a Global Scam Network [email protected] (The Hacker News)
The threat actors behind the VexTrio Viper Traffic Distribution Service (TDS) have been linked to other TDS services like Help TDS and Disposable TDS, indicating that the sophisticated cybercriminal operation is a sprawling enterprise of its own that’s designed to distribute malicious content. “VexTrio is a group of malicious adtech companies that distribute scams and…
