Category: Uncategorized
-
Datadog AI agent observability, security seek to boost trust
As AI agents mature, new tools aim to bolster their reliability and security with fresh visibility into automation workflows and more detailed troubleshooting.Read More
-
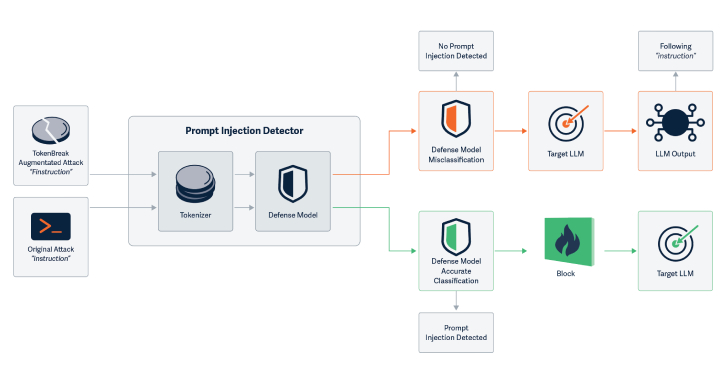
New TokenBreak Attack Bypasses AI Moderation with Single-Character Text Changes [email protected] (The Hacker News)
Cybersecurity researchers have discovered a novel attack technique called TokenBreak that can be used to bypass a large language model’s (LLM) safety and content moderation guardrails with just a single character change. “The TokenBreak attack targets a text classification model’s tokenization strategy to induce false negatives, leaving end targets vulnerable to attacks that the implementedRead…
-

AI Agents Run on Secret Accounts — Learn How to Secure Them in This Webinar [email protected] (The Hacker News)
AI is changing everything — from how we code, to how we sell, to how we secure. But while most conversations focus on what AI can do, this one focuses on what AI can break — if you’re not paying attention. Behind every AI agent, chatbot, or automation script lies a growing number of non-human…
-
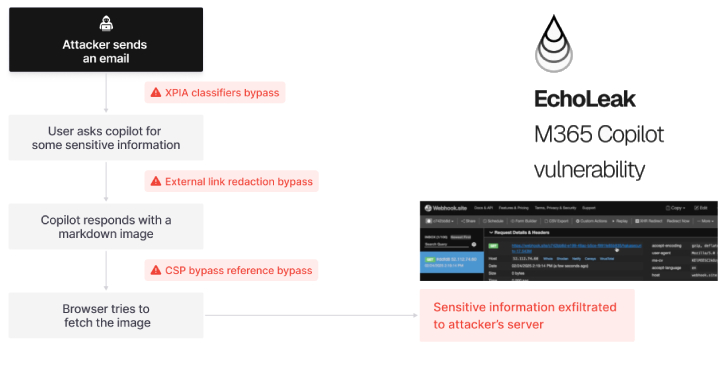
Zero-Click AI Vulnerability Exposes Microsoft 365 Copilot Data Without User Interaction [email protected] (The Hacker News)
A novel attack technique named EchoLeak has been characterized as a “zero-click” artificial intelligence (AI) vulnerability that allows bad actors to exfiltrate sensitive data from Microsoft 365 Copilot’s context sans any user interaction. The critical-rated vulnerability has been assigned the CVE identifier CVE-2025-32711 (CVSS score: 9.3). It requires no customer action and has been alreadyRead…
-

Non-Human Identities: How to Address the Expanding Security Risk [email protected] (The Hacker News)
Human identities management and control is pretty well done with its set of dedicated tools, frameworks, and best practices. This is a very different world when it comes to Non-human identities also referred to as machine identities. GitGuardian’s end-to-end NHI security platform is here to close the gap. Enterprises are Losing Track of Their Machine…
-

ConnectWise to Rotate ScreenConnect Code Signing Certificates Due to Security Risks [email protected] (The Hacker News)
ConnectWise has disclosed that it’s planning to rotate the digital code signing certificates used to sign ScreenConnect, ConnectWise Automate, and ConnectWise remote monitoring and management (RMM) executables due to security concerns. The company said it’s doing so “due to concerns raised by a third-party researcher about how ScreenConnect handled certain configuration data in earlier versions.Read…
-

Over 80,000 Microsoft Entra ID Accounts Targeted Using Open-Source TeamFiltration Tool [email protected] (The Hacker News)
Cybersecurity researchers have uncovered a new account takeover (ATO) campaign that leverages an open-source penetration testing framework called TeamFiltration to breach Microsoft Entra ID (formerly Azure Active Directory) user accounts. The activity, codenamed UNK_SneakyStrike by Proofpoint, has affected over 80,000 targeted user accounts across hundreds of organizations’ cloud tenants since aRead More
-
How to craft an effective AI security policy for enterprises
Enterprises unable to manage AI risks face data breaches, algorithmic bias and adversarial attacks, among other risks. Learn how to implement a comprehensive AI security policy.Read More
-

Former Black Basta Members Use Microsoft Teams and Python Scripts in 2025 Attacks [email protected] (The Hacker News)
Former members tied to the Black Basta ransomware operation have been observed sticking to their tried-and-tested approach of email bombing and Microsoft Teams phishing to establish persistent access to target networks. “Recently, attackers have introduced Python script execution alongside these techniques, using cURL requests to fetch and deploy malicious payloads,” ReliaQuest said in a reportRead…
-
Cisco Isovalent Load Balancer takes aim at Broadcom’s VMware
The new product promises to simplify disparate network traffic across cloud, hybrid and on-premises workloads.Read More
