Category: Uncategorized
-

FIN6 Uses AWS-Hosted Fake Resumes on LinkedIn to Deliver More_eggs Malware [email protected] (The Hacker News)
The financially motivated threat actor known as FIN6 has been observed leveraging fake resumes hosted on Amazon Web Services (AWS) infrastructure to deliver a malware family called More_eggs. “By posing as job seekers and initiating conversations through platforms like LinkedIn and Indeed, the group builds rapport with recruiters before delivering phishing messages that lead to…
-

Rust-based Myth Stealer Malware Spread via Fake Gaming Sites Targets Chrome, Firefox Users [email protected] (The Hacker News)
Cybersecurity researchers have shed light on a previously undocumented Rust-based information stealer called Myth Stealer that’s being propagated via fraudulent gaming websites. “Upon execution, the malware displays a fake window to appear legitimate while simultaneously decrypting and executing malicious code in the background,” Trellix security researchers Niranjan Hegde, Vasantha LakshmananRead More
-
How to implement effective app and API security controls
Security leaders must implement multilayered strategies combining threat modeling, balanced controls, cloud-first approaches and more to protect apps and APIs from evolving threats.Read More
-
Enumeration attacks: What they are and how to prevent them
User and network enumeration attacks help adversaries plan strong attack campaigns. Prevent them with MFA, rate limiting, CAPTCHA, secure code and more.Read More
-
How to calculate Windows Hello for Business cost
Just how much does Windows Hello for Business cost? It’s not exactly a simple answer, but the good news is that there are lots of ways to attain a license.Read More
-
How to choose coding standards: Development best practices
Learn how coding standards enhance quality and efficiency in software projects. Follow coding conventions and standards to achieve the five pillars of code quality.Read More
-

The Hidden Threat in Your Stack: Why Non-Human Identity Management is the Next Cybersecurity Frontier [email protected] (The Hacker News)
Modern enterprise networks are highly complex environments that rely on hundreds of apps and infrastructure services. These systems need to interact securely and efficiently without constant human oversight, which is where non-human identities (NHIs) come in. NHIs — including application secrets, API keys, service accounts, and OAuth tokens — have exploded in recent years, thanks…
-
12 common types of malware attacks and how to prevent them
More than one billion active malware programs exist worldwide. Is your organization prepared to prevent these 12 types of malware attacks?Read More
-
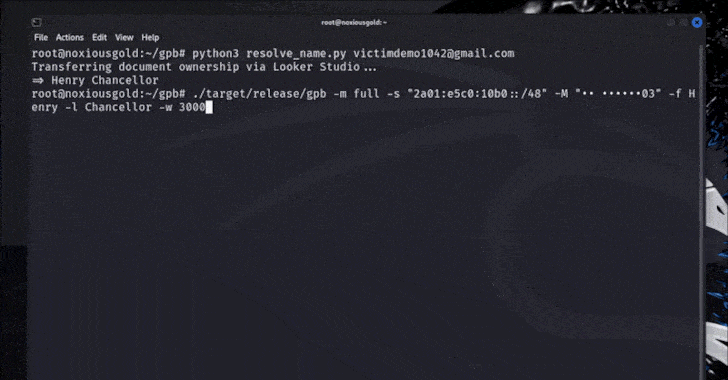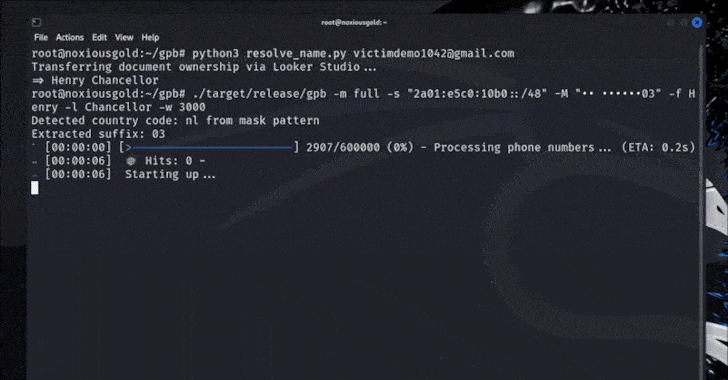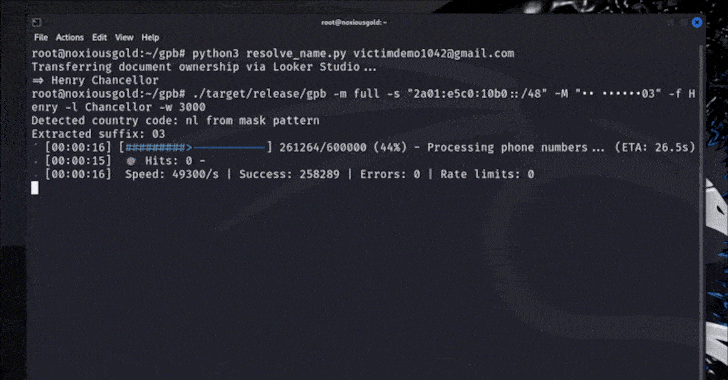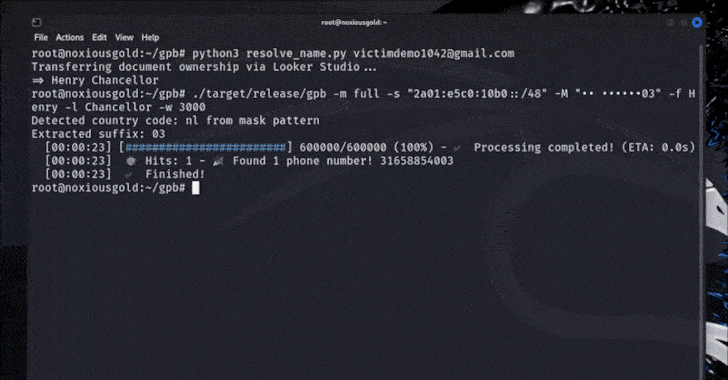
Researcher Found Flaw to Discover Phone Numbers Linked to Any Google Account [email protected] (The Hacker News)
Google has stepped in to address a security flaw that could have made it possible to brute-force an account’s recovery phone number, potentially exposing them to privacy and security risks. The issue, according to Singaporean security researcher “brutecat,” leverages an issue in the company’s account recovery feature. That said, exploiting the vulnerability hinges on several…
-
Symmetric vs. asymmetric encryption: Understand key differences
Explore the differences between symmetric vs. asymmetric encryption, including how they work and common algorithms, as well as their pros and cons.Read More
