Category: Uncategorized
-
Fix Active Directory account lockouts with PowerShell
Entering the wrong credentials so many times can block users from logging in. This tutorial explains how to find and correct these issues and other lockout events.Read More
-

OpenAI Bans ChatGPT Accounts Used by Russian, Iranian and Chinese Hacker Groups [email protected] (The Hacker News)
OpenAI has revealed that it banned a set of ChatGPT accounts that were likely operated by Russian-speaking threat actors and two Chinese nation-state hacking groups to assist with malware development, social media automation, and research about U.S. satellite communications technologies, among other things. “The [Russian-speaking] actor used our models to assist with developing and refiningRead…
-

New Supply Chain Malware Operation Hits npm and PyPI Ecosystems, Targeting Millions Globally [email protected] (The Hacker News)
Cybersecurity researchers have flagged a supply chain attack targeting over a dozen packages associated with GlueStack to deliver malware. The malware, introduced via a change to “lib/commonjs/index.js,” allows an attacker to run shell commands, take screenshots, and upload files to infected machines, Aikido Security told The Hacker News, stating these packages collectively account for nearly…
-
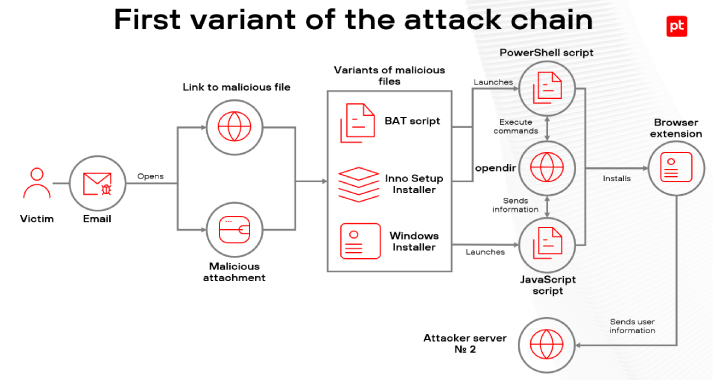
Malicious Browser Extensions Infect 722 Users Across Latin America Since Early 2025 [email protected] (The Hacker News)
Cybersecurity researchers have shed light on a new campaign targeting Brazilian users since the start of 2025 to infect users with a malicious extension for Chromium-based web browsers and siphon user authentication data. “Some of the phishing emails were sent from the servers of compromised companies, increasing the chances of a successful attack,” Positive Technologies…
-

New Atomic macOS Stealer Campaign Exploits ClickFix to Target Apple Users [email protected] (The Hacker News)
Cybersecurity researchers are alerting to a new malware campaign that employs the ClickFix social engineering tactic to trick users into downloading an information stealer malware known as Atomic macOS Stealer (AMOS) on Apple macOS systems. The campaign, according to CloudSEK, has been found to leverage typosquat domains mimicking U.S.-based telecom provider Spectrum. “macOS users are…
-
News brief: CISA and partners face budget overhauls, cuts
Check out the latest security news from the Informa TechTarget team.Read More
-
How to choose and set up a mobile VPN for an Android phone
A tailored approach to network security is crucial when managing smartphones in the enterprise. IT teams should consider Android VPN options for their organization.Read More
-

Empower Users and Protect Against GenAI Data Loss [email protected] (The Hacker News)
When generative AI tools became widely available in late 2022, it wasn’t just technologists who paid attention. Employees across all industries immediately recognized the potential of generative AI to boost productivity, streamline communication and accelerate work. Like so many waves of consumer-first IT innovation before it—file sharing, cloud storage and collaboration platforms—AI landed inRead More
-

Microsoft Helps CBI Dismantle Indian Call Centers Behind Japanese Tech Support Scam [email protected] (The Hacker News)
India’s Central Bureau of Investigation (CBI) has revealed that it has arrested four individuals and dismantled two illegal call centers that were found to be engaging in a sophisticated transnational tech support scam targeting Japanese citizens. The law enforcement agency said it conducted coordinated searches at 19 locations across Delhi, Haryana, and Uttar Pradesh on…
-

Inside the Mind of the Adversary: Why More Security Leaders Are Selecting AEV [email protected] (The Hacker News)
Cybersecurity involves both playing the good guy and the bad guy. Diving deep into advanced technologies and yet also going rogue in the Dark Web. Defining technical policies and also profiling attacker behavior. Security teams cannot be focused on just ticking boxes, they need to inhabit the attacker’s mindset. This is where AEV comes in.…
