Category: Uncategorized
-
What is continuous monitoring?
Post ContentRead More
-
3 types of deepfake detection technology and how they work
Post ContentRead More
-

How to Protect Your Business from Cyber Threats: Mastering the Shared Responsibility Model [email protected] (The Hacker News)
Cybersecurity isn’t just another checkbox on your business agenda. It’s a fundamental pillar of survival. As organizations increasingly migrate their operations to the cloud, understanding how to protect your digital assets becomes crucial. The shared responsibility model, exemplified through Microsoft 365’s approach, offers a framework for comprehending and implementing effective cybersecurityRead More
-

Six Governments Likely Use Israeli Paragon Spyware to Hack IM Apps and Harvest Data [email protected] (The Hacker News)
The governments of Australia, Canada, Cyprus, Denmark, Israel, and Singapore are likely customers of spyware developed by Israeli company Paragon Solutions, according to a new report from The Citizen Lab. Paragon, founded in 2019 by Ehud Barak and Ehud Schneorson, is the maker of a surveillance tool called Graphite that’s capable of harvesting sensitive data…
-

Why Continuous Compliance Monitoring Is Essential For IT Managed Service Providers [email protected] (The Hacker News)
Regulatory compliance is no longer just a concern for large enterprises. Small and mid-sized businesses (SMBs) are increasingly subject to strict data protection and security regulations, such as HIPAA, PCI-DSS, CMMC, GDPR, and the FTC Safeguards Rule. However, many SMBs struggle to maintain compliance due to limited IT resources, evolving regulatory requirements, and complex security…
-
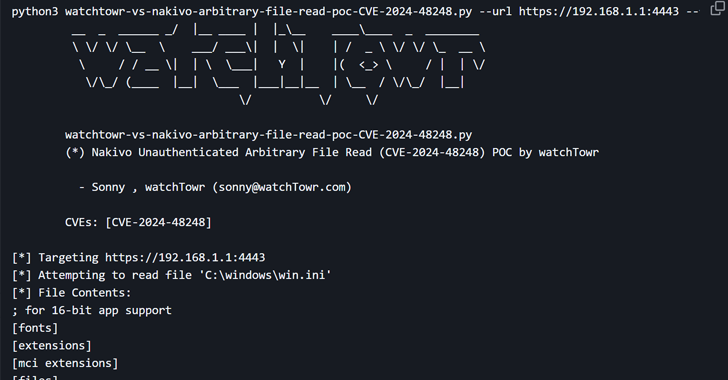
CISA Adds NAKIVO Vulnerability to KEV Catalog Amid Active Exploitation [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a high-severity security flaw impacting NAKIVO Backup & Replication software to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability in question is CVE-2024-48248 (CVSS score: 8.6), an absolute path traversal bug that could allow an unauthenticated attacker toRead More
-
IT risk assessment template (with free download)
Post ContentRead More
-
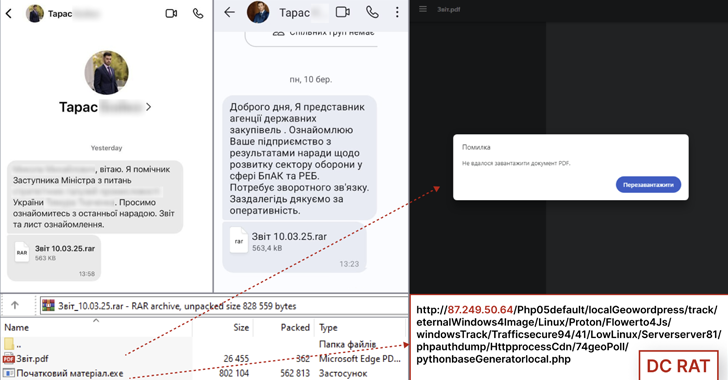
CERT-UA Warns: Dark Crystal RAT Targets Ukrainian Defense via Malicious Signal Messages [email protected] (The Hacker News)
The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of a new campaign that targets the defense sectors with Dark Crystal RAT (aka DCRat). The campaign, detected earlier this month, has been found to target both employees of enterprises of the defense-industrial complex and individual representatives of the Defense Forces of Ukraine. The activity…
-
How to sideload iOS apps and why it’s dangerous
Post ContentRead More
-

Hackers Exploit Severe PHP Flaw to Deploy Quasar RAT and XMRig Miners [email protected] (The Hacker News)
Threat actors are exploiting a severe security flaw in PHP to deliver cryptocurrency miners and remote access trojans (RATs) like Quasar RAT. The vulnerability, assigned the CVE identifier CVE-2024-4577, refers to an argument injection vulnerability in PHP affecting Windows-based systems running in CGI mode that could allow remote attackers to run arbitrary code. Cybersecurity companyRead…
