Category: Uncategorized
-
Tor Responds to Reports of German Police Deanonymizing Users Eduard Kovacs
The Tor Project has responded to claims that German law enforcement has found a way to deanonymize users. The post Tor Responds to Reports of German Police Deanonymizing Users appeared first on SecurityWeek. Read More
-

Iranian APT UNC1860 Linked to MOIS Facilitates Cyber Intrusions in Middle East [email protected] (The Hacker News)
An Iranian advanced persistent threat (APT) threat actor likely affiliated with the Ministry of Intelligence and Security (MOIS) is now acting as an initial access facilitator that provides remote access to target networks. Google-owned Mandiant is tracking the activity cluster under the moniker UNC1860, which it said shares similarities with intrusion sets tracked by Microsoft,…
-
Ivanti Warns of Second CSA Vulnerability Exploited in Attacks Eduard Kovacs
In addition to the Ivanti CSA flaw CVE-2024-8190, another vulnerability affecting the same product, tracked as CVE-2024-8963, has been exploited. The post Ivanti Warns of Second CSA Vulnerability Exploited in Attacks appeared first on SecurityWeek. Read More
-
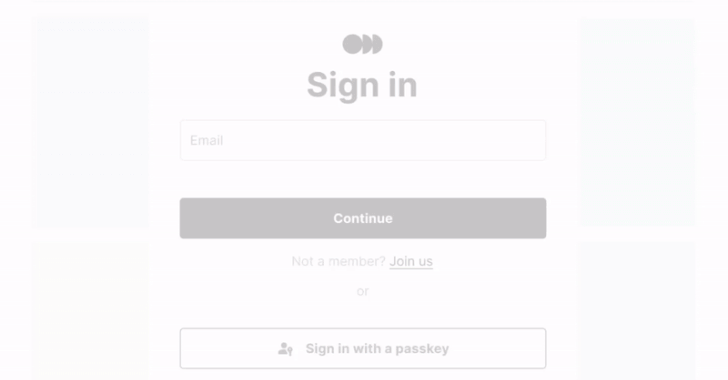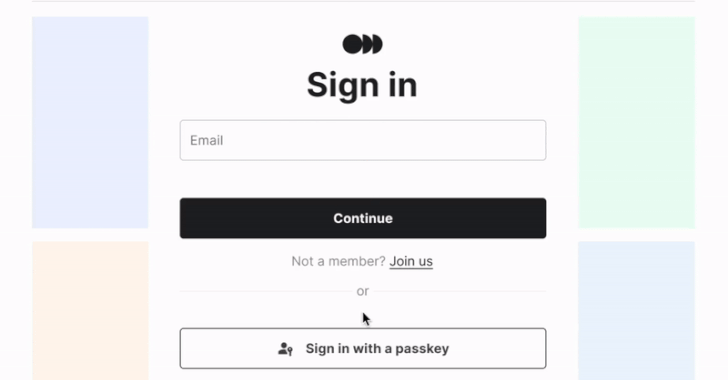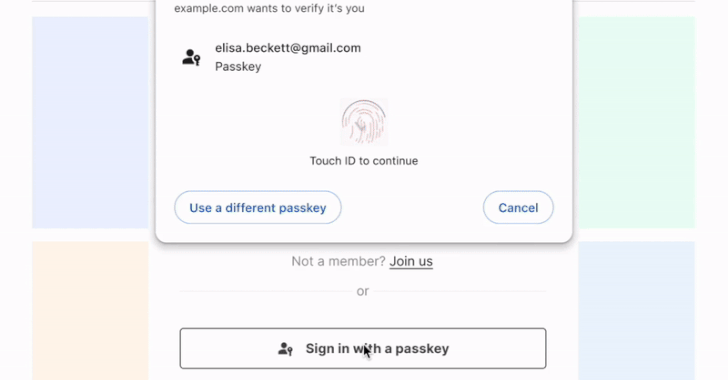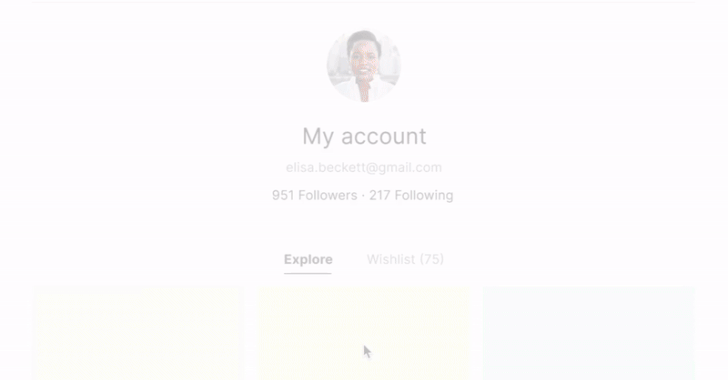
Chrome Users Can Now Sync Passkeys Across Devices with New Google PIN Feature [email protected] (The Hacker News)
Google on Thursday unveiled a Password Manager PIN to let Chrome web users sync their passkeys across Windows, macOS, Linux, ChromeOS, and Android devices. “This PIN adds an additional layer of security to ensure your passkeys are end-to-end encrypted and can’t be accessed by anyone, not even Google,” Chrome product manager Chirag Desai said. The…
-

Critical Ivanti Cloud Appliance Vulnerability Exploited in Active Cyberattacks [email protected] (The Hacker News)
Ivanti has revealed that a critical security flaw impacting Cloud Service Appliance (CSA) has come under active exploitation in the wild. The new vulnerability, assigned the CVE identifier CVE-2024-8963, carries a CVSS score of 9.4 out of a maximum of 10.0. It was “incidentally addressed” by the company as part of CSA 4.6 Patch 519…
-

Wherever There’s Ransomware, There’s Service Account Compromise. Are You Protected? [email protected] (The Hacker News)
Until just a couple of years ago, only a handful of IAM pros knew what service accounts are. In the last years, these silent Non-Human-Identities (NHI) accounts have become one of the most targeted and compromised attack surfaces. Assessments report that compromised service accounts play a key role in lateral movement in over 70% of…
-

Hackers Exploit Default Credentials in FOUNDATION Software to Breach Construction Firms [email protected] (The Hacker News)
Threat actors have been observed targeting the construction sector by infiltrating the FOUNDATION Accounting Software, according to new findings from Huntress. “Attackers have been observed brute-forcing the software at scale, and gaining access simply by using the product’s default credentials,” the cybersecurity company said. Targets of the emerging threat include plumbing, HVAC (heating,Read More
-
DNS security best practices to implement now
Post ContentRead More
-
CISA Releases Cyber Defense Alignment Plan for Federal Agencies Ionut Arghire
CISA has laid out the FOCAL plan, which aligns the collective operational defense capabilities across federal agencies. The post CISA Releases Cyber Defense Alignment Plan for Federal Agencies appeared first on SecurityWeek. Read More
-

New Brazilian-Linked SambaSpy Malware Targets Italian Users via Phishing Emails [email protected] (The Hacker News)
A previously undocumented malware called SambaSpy is exclusively targeting users in Italy via a phishing campaign orchestrated by a suspected Brazilian Portuguese-speaking threat actor. “Threat actors usually try to cast a wide net to maximize their profits, but these attackers are focused on just one country,” Kaspersky said in a new analysis. “It’s likely that…
