Category: Uncategorized
-
Webinar: Why Top Teams Are Prioritizing Code-to-Cloud Mapping in Our 2025 AppSec [email protected] (The Hacker News)
Picture this: Your team rolls out some new code, thinking everything’s fine. But hidden in there is a tiny flaw that explodes into a huge problem once it hits the cloud. Next thing you know, hackers are in, and your company is dealing with a mess that costs millions. Scary, right? In 2025, the average…
-

Hidden Vulnerabilities of Project Management Tools & How FluentPro Backup Secures Them [email protected] (The Hacker News)
Every day, businesses, teams, and project managers trust platforms like Trello, Asana, etc., to collaborate and manage tasks. But what happens when that trust is broken? According to a recent report by Statista, the average cost of a data breach worldwide was about $4.88 million. Also, in 2024, the private data of over 15 million…
-

Malicious Nx Packages in ‘s1ngularity’ Attack Leaked 2,349 GitHub, Cloud, and AI Credentials [email protected] (The Hacker News)
The maintainers of the nx build system have alerted users to a supply chain attack that allowed attackers to publish malicious versions of the popular npm package and other auxiliary plugins with data-gathering capabilities. “Malicious versions of the nx package, as well as some supporting plugin packages, were published to npm, containing code that scans…
-

U.S. Treasury Sanctions DPRK IT-Worker Scheme, Exposing $600K Crypto Transfers and $1M+ Profits [email protected] (The Hacker News)
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) announced a fresh round of sanctions against two individuals and two entities for their role in the North Korean remote information technology (IT) worker scheme to generate illicit revenue for the regime’s weapons of mass destruction and ballistic missile programs. “The North Korean…
-
What is network security? Definition and best practices
Network security encompasses all the steps taken to protect the integrity of a computer network and the data within it.Read More
-
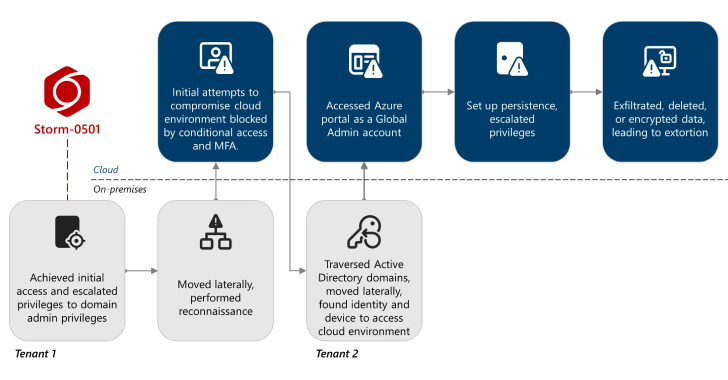
Storm-0501 Exploits Entra ID to Exfiltrate and Delete Azure Data in Hybrid Cloud Attacks [email protected] (The Hacker News)
The financially motivated threat actor known as Storm-0501 has been observed refining its tactics to conduct data exfiltration and extortion attacks targeting cloud environments. “Unlike traditional on-premises ransomware, where the threat actor typically deploys malware to encrypt critical files across endpoints within the compromised network and then negotiates for a decryption key,Read More
-

Someone Created First AI-Powered Ransomware Using OpenAI’s gpt-oss:20b Model [email protected] (The Hacker News)
Cybersecurity company ESET has disclosed that it discovered an artificial intelligence (AI)-powered ransomware variant codenamed PromptLock. Written in Golang, the newly identified strain uses the gpt-oss:20b model from OpenAI locally via the Ollama API to generate malicious Lua scripts in real-time. The open-weight language model was released by OpenAI earlier this month. “PromptLockRead More
-

Anthropic Disrupts AI-Powered Cyberattacks Automating Theft and Extortion Across Critical Sectors [email protected] (The Hacker News)
Anthropic on Wednesday revealed that it disrupted a sophisticated operation that weaponized its artificial intelligence (AI)-powered chatbot Claude to conduct large-scale theft and extortion of personal data in July 2025. “The actor targeted at least 17 distinct organizations, including in healthcare, the emergency services, and government, and religious institutions,” the company said. “Read More
-
ShadowSilk Hits 36 Government Targets in Central Asia and APAC Using Telegram Bots [email protected] (The Hacker News)
A threat activity cluster known as ShadowSilk has been attributed to a fresh set of attacks targeting government entities within Central Asia and Asia-Pacific (APAC). According to Group-IB, nearly three dozen victims have been identified, with the intrusions mainly geared towards data exfiltration. The hacking group shares toolset and infrastructural overlaps with campaigns undertaken by…
-
How to use Masscan for high-speed port scanning
Masscan delivers a quick assessment of open ports and listening services, but it helps to pair the utility with other scanning tools, such as Nmap.Read More
