Category: Uncategorized
-
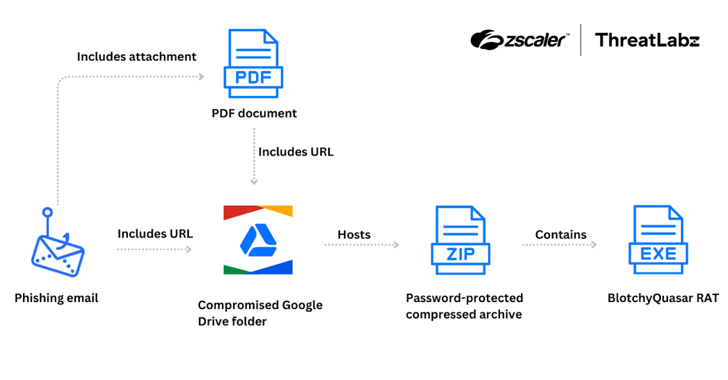
Blind Eagle Targets Colombian Insurance Sector with Customized Quasar RAT [email protected] (The Hacker News)
The Colombian insurance sector is the target of a threat actor tracked as Blind Eagle with the end goal of delivering a customized version of a known commodity remote access trojan (RAT) known as Quasar RAT since June 2024. “Attacks have originated with phishing emails impersonating the Colombian tax authority,” Zscaler ThreatLabz researcher Gaetano Pellegrino…
-
New RAMBO Attack Allows Air-Gapped Data Theft via RAM Radio Signals Ionut Arghire
An academic researcher has devised a new method of exfiltrating data from air-gapped systems using radio signals from memory buses. The post New RAMBO Attack Allows Air-Gapped Data Theft via RAM Radio Signals appeared first on SecurityWeek. Read More
-
Chinese Hackers Exploit Visual Studio Code in Southeast Asian Cyberattacks [email protected] (The Hacker News)
The China-linked advanced persistent threat (APT) group known as Mustang Panda has been observed weaponizing Visual Studio Code software as part of espionage operations targeting government entities in Southeast Asia. “This threat actor used Visual Studio Code’s embedded reverse shell feature to gain a foothold in target networks,” Palo Alto Networks Unit 42 researcher Tom…
-

Webinar: How to Protect Your Company from GenAI Data Leakage Without Losing It’s Productivity Benefits [email protected] (The Hacker News)
GenAI has become a table stakes tool for employees, due to the productivity gains and innovative capabilities it offers. Developers use it to write code, finance teams use it to analyze reports, and sales teams create customer emails and assets. Yet, these capabilities are exactly the ones that introduce serious security risks. Register to our…
-
How to create an AI acceptable use policy, plus template
Post ContentRead More
-
Critical SonicWall Vulnerability Possibly Exploited in Ransomware Attacks Eduard Kovacs
A recently patched SonicWall vulnerability tracked as CVE-2024-40766 may have been exploited in ransomware attacks. The post Critical SonicWall Vulnerability Possibly Exploited in Ransomware Attacks appeared first on SecurityWeek. Read More
-
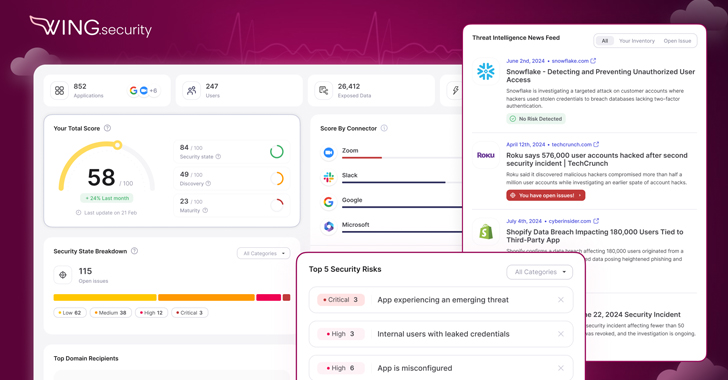
Wing Security SaaS Pulse: Continuous Security & Actionable Insights — For Free [email protected] (The Hacker News)
Designed to be more than a one-time assessment— Wing Security’s SaaS Pulse provides organizations with actionable insights and continuous oversight into their SaaS security posture—and it’s free! Introducing SaaS Pulse: Free Continuous SaaS Risk Management Just like waiting for a medical issue to become critical before seeing a doctor, organizations can’t afford to overlook the…
-
Predator Spyware Resurfaces With Fresh Infrastructure Ionut Arghire
Recorded Future observes renewed Predator spyware activity on fresh infrastructure after a drop caused by US sanctions. The post Predator Spyware Resurfaces With Fresh Infrastructure appeared first on SecurityWeek. Read More
-
One Million US Kaspersky Customers Transferred to Pango’s UltraAV Eduard Kovacs
Kaspersky’s customers in the US are being acquired by cybersecurity firm Pango and will be offered UltraAV antimalware software. The post One Million US Kaspersky Customers Transferred to Pango’s UltraAV appeared first on SecurityWeek. Read More
-

Progress Software Issues Patch for Vulnerability in LoadMaster and MT Hypervisor [email protected] (The Hacker News)
Progress Software has released security updates for a maximum-severity flaw in LoadMaster and Multi-Tenant (MT) hypervisor that could result in the execution of arbitrary operating system commands. Tracked as CVE-2024-7591 (CVSS score: 10.0), the vulnerability has been described as an improper input validation bug that results in OS command injection. “It is possible for unauthenticated,…
