Category: Uncategorized
-
How to use Masscan for high-speed port scanning
Masscan delivers a quick assessment of open ports and listening services, but it helps to pair the utility with other scanning tools, such as Nmap.Read More
-
How AI malware works and how to defend against it
AI malware is evolving faster than traditional defenses. Learn how attackers weaponize AI and how organizations can implement effective countermeasures.Read More
-

The 5 Golden Rules of Safe AI Adoption [email protected] (The Hacker News)
Employees are experimenting with AI at record speed. They are drafting emails, analyzing data, and transforming the workplace. The problem is not the pace of AI adoption, but the lack of control and safeguards in place. For CISOs and security leaders like you, the challenge is clear: you don’t want to slow AI adoption down,…
-

Salesloft OAuth Breach via Drift AI Chat Agent Exposes Salesforce Customer Data [email protected] (The Hacker News)
A widespread data theft campaign has allowed hackers to breach sales automation platform Salesloft to steal OAuth and refresh tokens associated with the Drift artificial intelligence (AI) chat agent. The activity, assessed to be opportunistic in nature, has been attributed to a threat actor tracked by Google Threat Intelligence Group and Mandiant, tracked as UNC6395.…
-
Blind Eagle’s Five Clusters Target Colombia Using RATs, Phishing Lures, and Dynamic DNS Infra [email protected] (The Hacker News)
Cybersecurity researchers have discovered five distinct activity clusters linked to a persistent threat actor known as Blind Eagle between May 2024 and July 2025. These attacks, observed by Recorded Future Insikt Group, targeted various victims, but primarily within the Colombian government across local, municipal, and federal levels. The threat intelligence firm is tracking the activity…
-
Compare Azure Government vs. Azure’s commercial cloud
Microsoft’s Azure Government and global cloud offerings serve different customers and have different compliance requirements. See how they compare to make the right choice.Read More
-

Citrix Patches Three NetScaler Flaws, Confirms Active Exploitation of CVE-2025-7775 [email protected] (The Hacker News)
Citrix has released fixes to address three security flaws in NetScaler ADC and NetScaler Gateway, including one that it said has been actively exploited in the wild. The vulnerabilities in question are listed below – CVE-2025-7775 (CVSS score: 9.2) – Memory overflow vulnerability leading to Remote Code Execution and/or Denial-of-Service CVE-2025-7776 (CVSS score: 8.8) –…
-
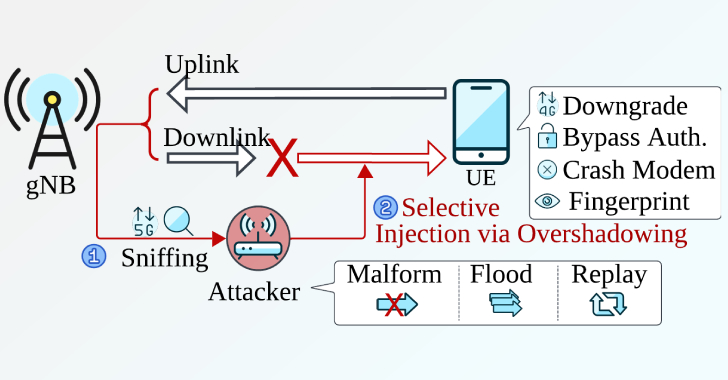
New Sni5Gect Attack Crashes Phones and Downgrades 5G to 4G without Rogue Base Station [email protected] (The Hacker News)
A team of academics has devised a novel attack that can be used to downgrade a 5G connection to a lower generation without relying on a rogue base station (gNB). The attack, per the ASSET (Automated Systems SEcuriTy) Research Group at the Singapore University of Technology and Design (SUTD), relies on a new open-source software…
-
How to use Netdiscover to map and troubleshoot networks
Read installation info, basic commands and practical applications for Netdiscover, an ARP-based tool that identifies live hosts, detects unauthorized devices and enhances security.Read More
-

MixShell Malware Delivered via Contact Forms Targets U.S. Supply Chain Manufacturers [email protected] (The Hacker News)
Cybersecurity researchers are calling attention to a sophisticated social engineering campaign that’s targeting supply chain-critical manufacturing companies with an in-memory malware dubbed MixShell. The activity has been codenamed ZipLine by Check Point Research. “Instead of sending unsolicited phishing emails, attackers initiate contact through a company’s public ‘Contact Us’ form, trickingRead More
