“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-

Hackers Exploit SharePoint Zero-Day Since July 7 to Steal Keys, Maintain Persistent Access [email protected] (The Hacker News)
The recently disclosed critical Microsoft SharePoint vulnerability has been under exploitation as early as July 7, 2025, according to findings from Check Point Research. The cybersecurity company said it observed first exploitation attempts targeting an unnamed major Western government, with the activity intensifying on July 18 and 19, spanning government, telecommunications, and softwareRead More
-
Microsoft SharePoint Zero-day Attack
FortiGuard Labs has detected and successfully blocked hundreds of exploitation attempts targeting a newly discovered zero-day vulnerability chain in on-premises Microsoft SharePoint servers. This active campaign is being exploited by multiple threat actors and poses a significant risk to a wide range of sectors including including government, education, healthcare, and large enterprises.Read More
-

Iran-Linked DCHSpy Android Malware Masquerades as VPN Apps to Spy on Dissidents [email protected] (The Hacker News)
Cybersecurity researchers have unearthed new Android spyware artifacts that are likely affiliated with the Iranian Ministry of Intelligence and Security (MOIS) and have been distributed to targets by masquerading as VPN apps and Starlink, a satellite internet connection service offered by SpaceX. Mobile security vendor Lookout said it discovered four samples of a surveillanceware tool…
-

China-Linked Hackers Launch Targeted Espionage Campaign on African IT Infrastructure [email protected] (The Hacker News)
The China-linked cyber espionage group tracked as APT41 has been attributed to a new campaign targeting government IT services in the African region. “The attackers used hardcoded names of internal services, IP addresses, and proxy servers embedded within their malware,” Kaspersky researchers Denis Kulik and Daniil Pogorelov said. “One of the C2s [command-and-control servers] was…
-
Risk prediction models: How they work and their benefits
Accurate risk prediction models can aid risk management efforts in organizations. Here’s a look at how risk models work and the business benefits they provide.Read More
-

⚡ Weekly Recap: SharePoint 0-Day, Chrome Exploit, macOS Spyware, NVIDIA Toolkit RCE and More [email protected] (The Hacker News)
Even in well-secured environments, attackers are getting in—not with flashy exploits, but by quietly taking advantage of weak settings, outdated encryption, and trusted tools left unprotected. These attacks don’t depend on zero-days. They work by staying unnoticed—slipping through the cracks in what we monitor and what we assume is safe. What once looked suspicious now…
-
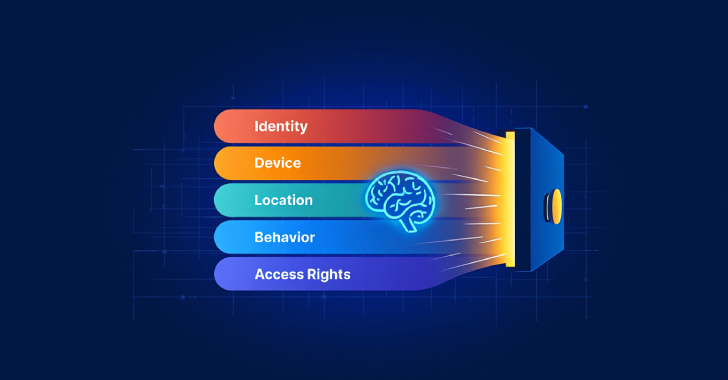
Assessing the Role of AI in Zero Trust [email protected] (The Hacker News)
By 2025, Zero Trust has evolved from a conceptual framework into an essential pillar of modern security. No longer merely theoretical, it’s now a requirement that organizations must adopt. A robust, defensible architecture built on Zero Trust principles does more than satisfy baseline regulatory mandates. It underpins cyber resilience, secures third-party partnerships, and ensures uninterruptedRead…
-
Microsoft SharePoint attacks target on-premises servers
Thousands of organizations, including government agencies, running SharePoint on-premises are vulnerable after Microsoft issued a security alert warning of active attacks.Read More
-
What is a CISO (chief information security officer)?
The CISO (chief information security officer) is a senior-level executive responsible for developing and implementing an information security program.Read More
-
An explanation of data breaches
Data breaches can be intentional or accidental and come in various forms, but all types have the potential to cause considerable harm to individuals and organizations.Read More
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
