“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-

URGENT: Microsoft Patches 57 Security Flaws, Including 6 Actively Exploited Zero-Days [email protected] (The Hacker News)
Microsoft on Tuesday released security updates to address 57 security vulnerabilities in its software, including a whopping six zero-days that it said have been actively exploited in the wild. Of the 56 flaws, six are rated Critical, 50 are rated Important, and one is rated Low in severity. Twenty-three of the addressed vulnerabilities are remote…
-

Apple Releases Patch for WebKit Zero-Day Vulnerability Exploited in Targeted Attacks [email protected] (The Hacker News)
Apple on Tuesday released a security update to address a zero-day flaw that it said has been exploited in “extremely sophisticated” attacks. The vulnerability has been assigned the CVE identifier CVE-2025-24201 and is rooted in the WebKit web browser engine component. It has been described as an out-of-bounds write issue that could allow an attacker…
-
Incident response for web application attacks
Post ContentRead More
-
Blind Eagle Hacks Colombian Institutions Using NTLM Flaw, RATs and GitHub-Based Attacks [email protected] (The Hacker News)
The threat actor known as Blind Eagle has been linked to a series of ongoing campaigns targeting Colombian institutions and government entities since November 2024. “The monitored campaigns targeted Colombian judicial institutions and other government or private organizations, with high infection rates,” Check Point said in a new analysis. “More than 1,600 victims were affected…
-

Ballista Botnet Exploits Unpatched TP-Link Vulnerability, Infects Over 6,000 Devices [email protected] (The Hacker News)
Unpatched TP-Link Archer routers have become the target of a new botnet campaign dubbed Ballista, according to new findings from the Cato CTRL team. “The botnet exploits a remote code execution (RCE) vulnerability in TP-Link Archer routers (CVE-2023-1389) to spread itself automatically over the Internet,” security researchers Ofek Vardi and Matan Mittelman said in a…
-

Your Risk Scores Are Lying: Adversarial Exposure Validation Exposes Real Threats [email protected] (The Hacker News)
In cybersecurity, confidence is a double-edged sword. Organizations often operate under a false sense of security, believing that patched vulnerabilities, up-to-date tools, polished dashboards, and glowing risk scores guarantee safety. The reality is a bit of a different story. In the real world, checking the right boxes doesn’t equal being secure. As Sun Tzu warned,…
-

Steganography Explained: How XWorm Hides Inside Images [email protected] (The Hacker News)
Inside the most innocent-looking image, a breathtaking landscape, or a funny meme, something dangerous could be hiding, waiting for its moment to strike. No strange file names. No antivirus warnings. Just a harmless picture, secretly concealing a payload that can steal data, execute malware, and take over your system without a trace. This is steganography,…
-
What is a copyright?
Post ContentRead More
-
What is a rootkit?
Post ContentRead More
-
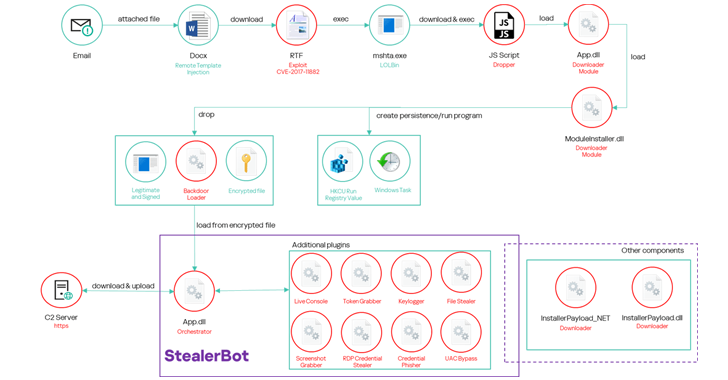
SideWinder APT Targets Maritime, Nuclear, and IT Sectors Across Asia, Middle East, and Africa [email protected] (The Hacker News)
Maritime and logistics companies in South and Southeast Asia, the Middle East, and Africa have become the target of an advanced persistent threat (APT) group dubbed SideWinder. The attacks, observed by Kaspersky in 2024, spread across Bangladesh, Cambodia, Djibouti, Egypt, the United Arab Emirates, and Vietnam. Other targets of interest include nuclear power plants and…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
