“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-

Moxa Issues Fix for Critical Authentication Bypass Vulnerability in PT Switches [email protected] (The Hacker News)
Taiwanese company Moxa has released a security update to address a critical security flaw impacting its PT switches that could permit an attacker to bypass authentication guarantees. The vulnerability, tracked as CVE-2024-12297, has been assigned a CVSS v4 score of 9.2 out of a maximum of 10.0. “Multiple Moxa PT switches are vulnerable to an…
-

CISA Adds Five Actively Exploited Vulnerabilities in Advantive VeraCore and Ivanti EPM to KEV List [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added five security flaws impacting Advantive VeraCore and Ivanti Endpoint Manager (EPM) to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation in the wild. The list of vulnerabilities is as follows – CVE-2024-57968 – An unrestricted file upload vulnerability in Advantive…
-
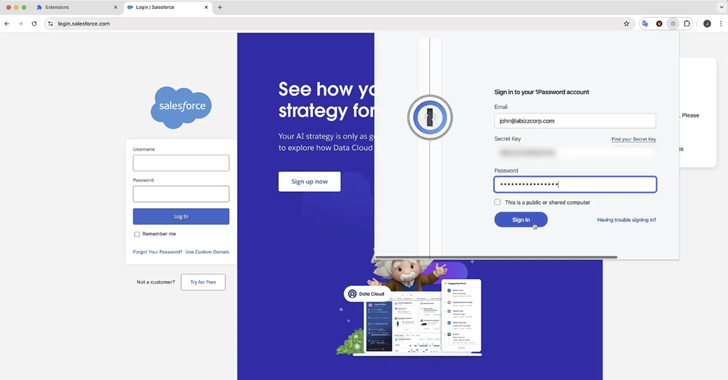
Researchers Expose New Polymorphic Attack That Clones Browser Extensions to Steal Credentials [email protected] (The Hacker News)
Cybersecurity researchers have demonstrated a novel technique that allows a malicious web browser extension to impersonate any installed add-on. “The polymorphic extensions create a pixel perfect replica of the target’s icon, HTML popup, workflows and even temporarily disables the legitimate extension, making it extremely convincing for victims to believe that they are providing credentials toRead…
-
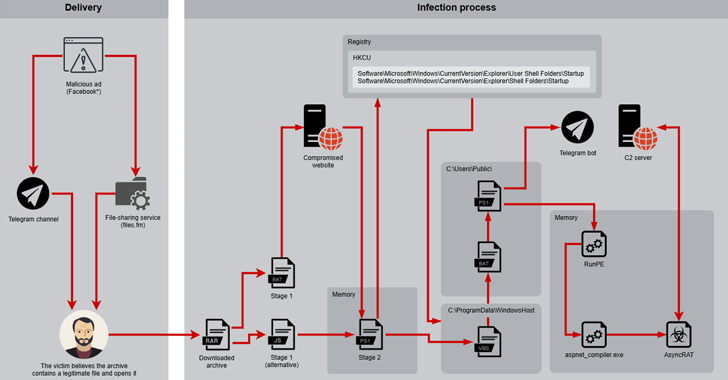
Desert Dexter Targets 900 Victims Using Facebook Ads and Telegram Malware Links [email protected] (The Hacker News)
The Middle East and North Africa have become the target of a new campaign that delivers a modified version of a known malware called AsyncRAT since September 2024. “The campaign, which leverages social media to distribute malware, is tied to the region’s current geopolitical climate,” Positive Technologies researchers Klimentiy Galkin and Stanislav Pyzhov said in…
-

Why The Modern Google Workspace Needs Unified Security [email protected] (The Hacker News)
The Need For Unified Security Google Workspace is where teams collaborate, share ideas, and get work done. But while it makes work easier, it also creates new security challenges. Cybercriminals are constantly evolving, finding ways to exploit misconfigurations, steal sensitive data, and hijack user accounts. Many organizations try to secure their environment by piecing together…
-

⚡ THN Weekly Recap: New Attacks, Old Tricks, Bigger Impact [email protected] (The Hacker News)
Cyber threats today don’t just evolve—they mutate rapidly, testing the resilience of everything from global financial systems to critical infrastructure. As cybersecurity confronts new battlegrounds—ranging from nation-state espionage and ransomware to manipulated AI chatbots—the landscape becomes increasingly complex, prompting vital questions: How secure are our cloud environments? Can ourRead More
-
What is Kerberos and how does it work?
Post ContentRead More
-

SilentCryptoMiner Infects 2,000 Russian Users via Fake VPN and DPI Bypass Tools [email protected] (The Hacker News)
A new mass malware campaign is infecting users with a cryptocurrency miner named SilentCryptoMiner by masquerading it as a tool designed to circumvent internet blocks and restrictions around online services. Russian cybersecurity company Kaspersky said the activity is part of a larger trend where cybercriminals are increasingly leveraging Windows Packet Divert (WPD) tools to distribute…
-
What are the most common digital authentication methods?
Post ContentRead More
-

FIN7, FIN8, and Others Use Ragnar Loader for Persistent Access and Ransomware Operations [email protected] (The Hacker News)
Threat hunters have shed light on a “sophisticated and evolving malware toolkit” called Ragnar Loader that’s used by various cybercrime and ransomware groups like Ragnar Locker (aka Monstrous Mantis), FIN7, FIN8, and Ruthless Mantis (ex-REvil). “Ragnar Loader plays a key role in keeping access to compromised systems, helping attackers stay in networks for long-term operations,”…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
