“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-

Sticky Werewolf Uses Undocumented Implant to Deploy Lumma Stealer in Russia and Belarus [email protected] (The Hacker News)
The threat actor known as Sticky Werewolf has been linked to targeted attacks primarily in Russia and Belarus with the aim of delivering the Lumma Stealer malware by means of a previously undocumented implant. Cybersecurity company Kaspersky is tracking the activity under the name Angry Likho, which it said bears a “strong resemblance” to Awaken…
-
What is the NSA and how does it work?
Post ContentRead More
-
Why and how to create Azure service principals
Post ContentRead More
-
What is a watering hole attack?
Post ContentRead More
-
What is multifactor authentication?
Post ContentRead More
-
What is FCAPS (fault, configuration, accounting, performance and security)?
Post ContentRead More
-
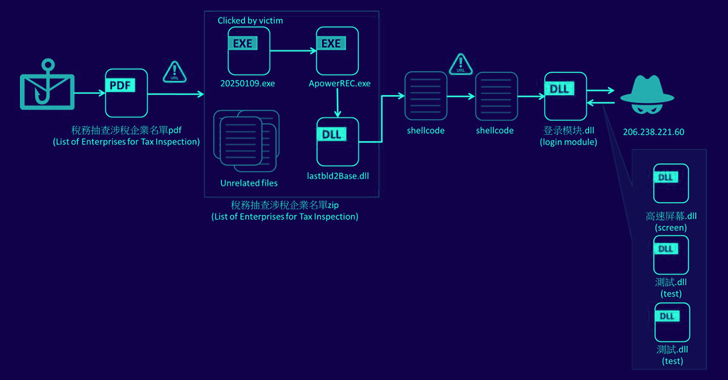
Silver Fox APT Uses Winos 4.0 Malware in Cyber Attacks Against Taiwanese Organizations [email protected] (The Hacker News)
A new campaign is targeting companies in Taiwan with malware known as Winos 4.0 as part of phishing emails masquerading as the country’s National Taxation Bureau. The campaign, detected last month by Fortinet FortiGuard Labs, marks a departure from previous attack chains that have leveraged malicious game-related applications. “The sender claimed that the malicious file…
-

Space Pirates Targets Russian IT Firms With New LuckyStrike Agent Malware [email protected] (The Hacker News)
The threat actor known as Space Pirates has been linked to a malicious campaign targeting Russian information technology (IT) organizations with a previously undocumented malware called LuckyStrike Agent. The activity was detected in November 2024 by Solar, the cybersecurity arm of Russian state-owned telecom company Rostelecom. It’s tracking the activity under the name Erudite Mogwai.…
-
FBI: Lazarus Group behind $1.5 billion Bybit heist
Post ContentRead More
-

89% of Enterprise GenAI Usage Is Invisible to Organizations Exposing Critical Security Risks, New Report Reveals [email protected] (The Hacker News)
Organizations are either already adopting GenAI solutions, evaluating strategies for integrating these tools into their business plans, or both. To drive informed decision-making and effective planning, the availability of hard data is essential—yet such data remains surprisingly scarce. The “Enterprise GenAI Data Security Report 2025” by LayerX delivers unprecedented insightsRead More
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
