“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
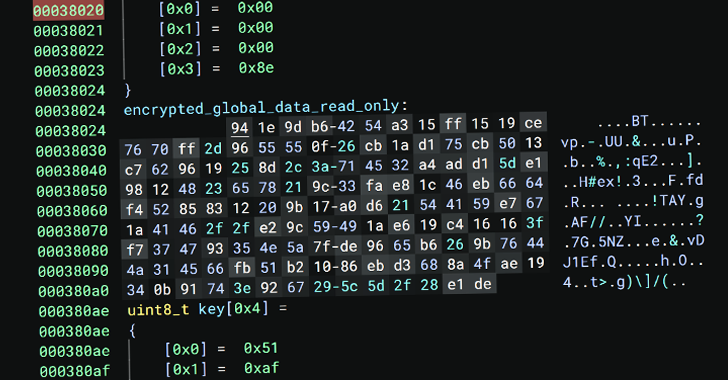
New Linux Malware ‘Auto-Color’ Grants Hackers Full Remote Access to Compromised Systems [email protected] (The Hacker News)
Universities and government organizations in North America and Asia have been targeted by a previously undocumented Linux malware called Auto-Color between November and December 2024, according to new findings from Palo Alto Networks Unit 42. “Once installed, Auto-color allows threat actors full remote access to compromised machines, making it very difficult to remove without specializedRead…
-

Three Password Cracking Techniques and How to Defend Against Them [email protected] (The Hacker News)
Passwords are rarely appreciated until a security breach occurs; suffice to say, the importance of a strong password becomes clear only when faced with the consequences of a weak one. However, most end users are unaware of just how vulnerable their passwords are to the most common password-cracking methods. The following are the three common techniques…
-
CERT-UA Warns of UAC-0173 Attacks Deploying DCRat to Compromise Ukrainian Notaries [email protected] (The Hacker News)
The Computer Emergency Response Team of Ukraine (CERT-UA) on Tuesday warned of renewed activity from an organized criminal group it tracks as UAC-0173 that involves infecting computers with a remote access trojan named DCRat (aka DarkCrystal RAT). The Ukrainian cybersecurity authority said it observed the latest attack wave starting in mid-January 2025. The activity is…
-

Malicious PyPI Package “automslc” Enables 104K+ Unauthorized Deezer Music Downloads [email protected] (The Hacker News)
Cybersecurity researchers have flagged a malicious Python library on the Python Package Index (PyPI) repository that facilitates unauthorized music downloads from music streaming service Deezer. The package in question is automslc, which has been downloaded over 104,000 times to date. First published in May 2019, it remains available on PyPI as of writing. “Although automslc,…
-

CISA Adds Microsoft and Zimbra Flaws to KEV Catalog Amid Active Exploitation [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday placed two security flaws impacting Microsoft Partner Center and Synacor Zimbra Collaboration Suite (ZCS) to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerabilities in question are as follows – CVE-2024-49035 (CVSS score: 8.7) – An improper access controlRead More
-
NCC Group tracks alarming ransomware surge in January
Post ContentRead More
-
LightSpy Expands to 100+ Commands, Increasing Control Over Windows, macOS, Linux, and Mobile [email protected] (The Hacker News)
Cybersecurity researchers have flagged an updated version of the LightSpy implant that comes equipped with an expanded set of data collection features to extract information from social media platforms like Facebook and Instagram. LightSpy is the name given to a modular spyware that’s capable of infecting both Windows and Apple systems with an aim to…
-
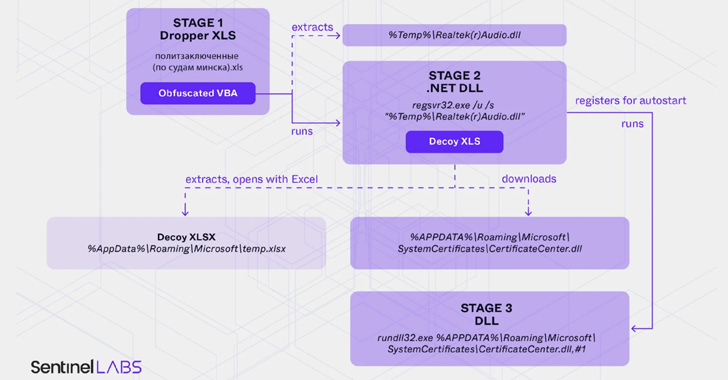
Belarus-Linked Ghostwriter Uses Macropack-Obfuscated Excel Macros to Deploy Malware [email protected] (The Hacker News)
Opposition activists in Belarus as well as Ukrainian military and government organizations are the target of a new campaign that employs malware-laced Microsoft Excel documents as lures to deliver a new variant of PicassoLoader. The threat cluster has been assessed to be an extension of a long-running campaign mounted by a Belarus-aligned threat actor dubbed…
-
Black Basta ransomware leak sheds light on targets, tactics
Post ContentRead More
-

5 Active Malware Campaigns in Q1 2025 [email protected] (The Hacker News)
The first quarter of 2025 has been a battlefield in the world of cybersecurity. Cybercriminals continued launching aggressive new campaigns and refining their attack methods. Below is an overview of five notable malware families, accompanied by analyses conducted in controlled environments. NetSupport RAT Exploiting the ClickFix Technique In early 2025, threat actors began exploiting a…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
