“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
Malware Injected into 6 npm Packages After Maintainer Tokens Stolen in Phishing Attack [email protected] (The Hacker News)
Cybersecurity researchers have alerted to a supply chain attack that has targeted popular npm packages via a phishing campaign designed to steal the project maintainers’ npm tokens. The captured tokens were then used to publish malicious versions of the packages directly to the registry without any source code commits or pull requests on their respective…
-

Hackers Exploit Critical CrushFTP Flaw to Gain Admin Access on Unpatched Servers [email protected] (The Hacker News)
A newly disclosed critical security flaw in CrushFTP has come under active exploitation in the wild. Assigned the CVE identifier CVE-2025-54309, the vulnerability carries a CVSS score of 9.0. “CrushFTP 10 before 10.8.5 and 11 before 11.3.4_23, when the DMZ proxy feature is not used, mishandles AS2 validation and consequently allows remote attackers to obtain…
-

China’s Massistant Tool Secretly Extracts SMS, GPS Data, and Images From Confiscated Phones [email protected] (The Hacker News)
Cybersecurity researchers have shed light on a mobile forensics tool called Massistant that’s used by law enforcement authorities in China to gather information from seized mobile devices. The hacking tool, believed to be a successor of MFSocket, is developed by a Chinese company named SDIC Intelligence Xiamen Information Co., Ltd., which was formerly known as…
-

UNG0002 Group Hits China, Hong Kong, Pakistan Using LNK Files and RATs in Twin Campaigns [email protected] (The Hacker News)
Multiple sectors in China, Hong Kong, and Pakistan have become the target of a threat activity cluster tracked as UNG0002 (aka Unknown Group 0002) as part of a broader cyber espionage campaign. “This threat entity demonstrates a strong preference for using shortcut files (LNK), VBScript, and post-exploitation tools such as Cobalt Strike and Metasploit, while…
-
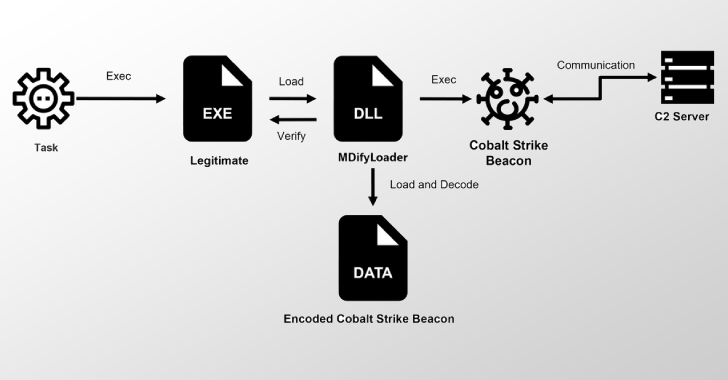
Ivanti Zero-Days Exploited to Drop MDifyLoader and Launch In-Memory Cobalt Strike Attacks [email protected] (The Hacker News)
Cybersecurity researchers have disclosed details of a new malware called MDifyLoader that has been observed in conjunction with cyber attacks exploiting security flaws in Ivanti Connect Secure (ICS) appliances. According to a report published by JPCERT/CC today, the threat actors behind the exploitation of CVE-2025-0282 and CVE-2025-22457 in intrusions observed between December 2024 and JulyRead…
-
How to create a risk management plan: Template, key steps
A risk management plan provides a framework for managing business risks. Here’s what it includes and how to develop one, plus a downloadable plan template.Read More
-
CISO role in ASM could add runtime security, tokenization
Runtime security and tokenization stand to play a bigger role in attack surface management, a development that could influence security leaders’ responsibilities.Read More
-
News brief: Cyberattack trends signal security arms race
Check out the latest security news from the Informa TechTarget team.Read More
-
How to build a cybersecurity team to maximize business impact
How CISOs design and build their security teams is as important as the technology they select to safeguard their organizations’ digital assets.Read More
-

CERT-UA Discovers LAMEHUG Malware Linked to APT28, Using LLM for Phishing Campaign [email protected] (The Hacker News)
The Computer Emergency Response Team of Ukraine (CERT-UA) has disclosed details of a phishing campaign that’s designed to deliver a malware codenamed LAMEHUG. “An obvious feature of LAMEHUG is the use of LLM (large language model), used to generate commands based on their textual representation (description),” CERT-UA said in a Thursday advisory. The activity has…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
