“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-

The Ultimate MSP Guide to Structuring and Selling vCISO Services [email protected] (The Hacker News)
The growing demand for cybersecurity and compliance services presents a great opportunity for Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs) to offer virtual Chief Information Security Officer (vCISO) services—delivering high-level cybersecurity leadership without the cost of a full-time hire. However, transitioning to vCISO services is not without its challengesRead More
-

Trojanized Game Installers Deploy Cryptocurrency Miner in Large-Scale StaryDobry Attack [email protected] (The Hacker News)
Users who are on the lookout for popular games were lured into downloading trojanized installers that led to the deployment of a cryptocurrency miner on compromised Windows hosts. The large-scale activity has been codenamed StaryDobry by Russian cybersecurity company Kaspersky, which first detected it on December 31, 2024. It lasted for a month. Targets of…
-
What is email spoofing?
Post ContentRead More
-

CISA Adds Palo Alto Networks and SonicWall Flaws to Exploited Vulnerabilities List [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added two security flaws impacting Palo Alto Networks PAN-OS and SonicWall SonicOS SSLVPN to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The flaws are listed below – CVE-2025-0108 (CVSS score: 7.8) – An authentication bypass vulnerability in the Palo Alto…
-

New OpenSSH Flaws Enable Man-in-the-Middle and DoS Attacks — Patch Now [email protected] (The Hacker News)
Two security vulnerabilities have been discovered in the OpenSSH secure networking utility suite that, if successfully exploited, could result in an active machine-in-the-middle (MitM) and a denial-of-service (DoS) attack, respectively, under certain conditions. The vulnerabilities, detailed by the Qualys Threat Research Unit (TRU), are listed below – CVE-2025-26465 – The OpenSSH clientRead More
-

Chinese Hackers Exploit MAVInject.exe to Evade Detection in Targeted Cyber Attacks [email protected] (The Hacker News)
The Chinese state-sponsored threat actor known as Mustang Panda has been observed employing a novel technique to evade detection and maintain control over infected systems. This involves the use of a legitimate Microsoft Windows utility called Microsoft Application Virtualization Injector (MAVInject.exe) to inject the threat actor’s malicious payload into an external process, waitfor.exe,Read More
-
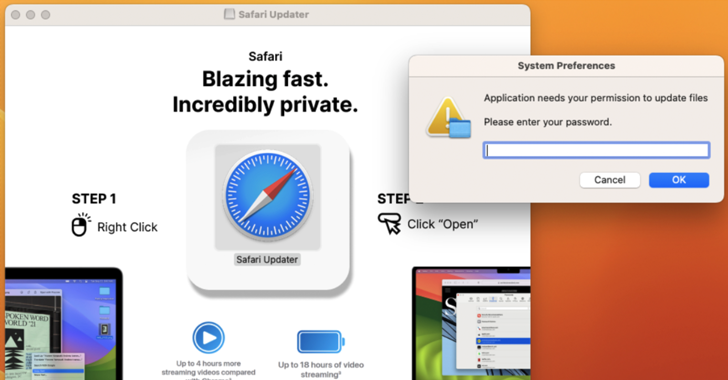
New FrigidStealer Malware Targets macOS Users via Fake Browser Updates [email protected] (The Hacker News)
Cybersecurity researchers are alerting to a new campaign that leverages web injects to deliver a new Apple macOS malware known as FrigidStealer. The activity has been attributed to a previously undocumented threat actor known as TA2727, with the information stealers for other platforms such as Windows (Lumma Stealer or DeerStealer) and Android (Marcher). TA2727 is…
-
What is defense in depth?
Post ContentRead More
-

Juniper Session Smart Routers Vulnerability Could Let Attackers Bypass Authentication [email protected] (The Hacker News)
Juniper Networks has released security updates to address a critical security flaw impacting Session Smart Router, Session Smart Conductor, and WAN Assurance Router products that could be exploited to hijack control of susceptible devices. Tracked as CVE-2025-21589, the vulnerability carries a CVSS v3.1 score of 9.8 and a CVS v4 score of 9.3. “An Authentication…
-
Palo Alto Networks PAN-OS vulnerability exploited in the wild
Post ContentRead More
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
