“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
New FrigidStealer Malware Targets macOS Users via Fake Browser Updates [email protected] (The Hacker News)
Cybersecurity researchers are alerting to a new campaign that leverages web injects to deliver a new Apple macOS malware known as FrigidStealer. The activity has been attributed to a previously undocumented threat actor known as TA2727, with the information stealers for other platforms such as Windows (Lumma Stealer or DeerStealer) and Android (Marcher). TA2727 is…
-
What is defense in depth?
Post ContentRead More
-

Juniper Session Smart Routers Vulnerability Could Let Attackers Bypass Authentication [email protected] (The Hacker News)
Juniper Networks has released security updates to address a critical security flaw impacting Session Smart Router, Session Smart Conductor, and WAN Assurance Router products that could be exploited to hijack control of susceptible devices. Tracked as CVE-2025-21589, the vulnerability carries a CVSS v3.1 score of 9.8 and a CVS v4 score of 9.3. “An Authentication…
-
Palo Alto Networks PAN-OS vulnerability exploited in the wild
Post ContentRead More
-

Debunking the AI Hype: Inside Real Hacker Tactics [email protected] (The Hacker News)
Is AI really reshaping the cyber threat landscape, or is the constant drumbeat of hype drowning out actual, more tangible, real-world dangers? According to Picus Labs’ Red Report 2025 which analyzed over one million malware samples, there’s been no significant surge, so far, in AI-driven attacks. Yes, adversaries are definitely continuing to innovate, and while…
-
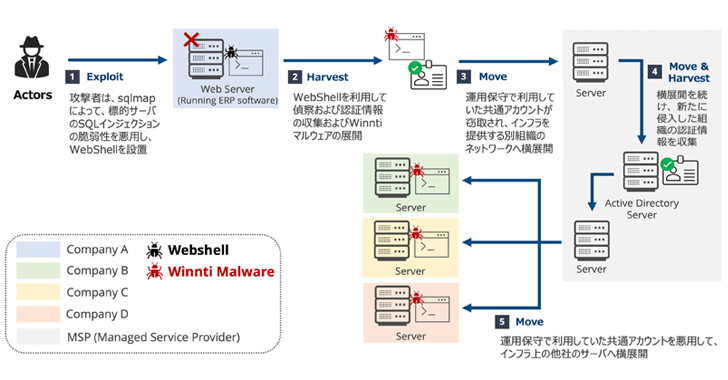
Winnti APT41 Targets Japanese Firms in RevivalStone Cyber Espionage Campaign [email protected] (The Hacker News)
The China-linked threat actor known as Winnti has been attributed to a new campaign dubbed RevivalStone that targeted Japanese companies in the manufacturing, materials, and energy sectors in March 2024. The activity, detailed by Japanese cybersecurity company LAC, overlaps with a threat cluster tracked by Trend Micro as Earth Freybug, which has been assessed to…
-
What is the Nessus vulnerability scanning platform?
Post ContentRead More
-
What are social engineering attacks?
Post ContentRead More
-

New Xerox Printer Flaws Could Let Attackers Capture Windows Active Directory Credentials [email protected] (The Hacker News)
Security vulnerabilities have been disclosed in Xerox VersaLink C7025 Multifunction printers (MFPs) that could allow attackers to capture authentication credentials via pass-back attacks via Lightweight Directory Access Protocol (LDAP) and SMB/FTP services. “This pass-back style attack leverages a vulnerability that allows a malicious actor to alter the MFP’s configuration and cause the MFPRead More
-

Cybercriminals Exploit Onerror Event in Image Tags to Deploy Payment Skimmers [email protected] (The Hacker News)
Cybersecurity researchers have flagged a credit card stealing malware campaign that has been observed targeting e-commerce sites running Magento by disguising the malicious content within image tags in HTML code in order to stay under the radar. MageCart is the name given to a malware that’s capable of stealing sensitive payment information from online shopping…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
