“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-

Protecting Your Software Supply Chain: Assessing the Risks Before Deployment [email protected] (The Hacker News)
Imagine you’re considering a new car for your family. Before making a purchase, you evaluate its safety ratings, fuel efficiency, and reliability. You might even take it for a test drive to ensure it meets your needs. The same approach should be applied to software and hardware products before integrating them into an organization’s environment.…
-

Threat Actors Exploit ClickFix to Deploy NetSupport RAT in Latest Cyber Attacks [email protected] (The Hacker News)
Threat actors have observed the increasingly common ClickFix technique to deliver a remote access trojan named NetSupport RAT since early January 2025. NetSupport RAT, typically propagated via bogus websites and fake browser updates, grants attackers full control over the victim’s host, allowing them to monitor the device’s screen in real-time, control the keyboard and mouse,…
-
What is Blowfish?
Post ContentRead More
-
How to use pfSense: Use cases and initial configurations
Post ContentRead More
-

8Base Ransomware Data Leak Sites Seized in International Law Enforcement Operation [email protected] (The Hacker News)
Source: The Nation A coordinated law enforcement operation has taken down the dark web data leak and negotiation sites associated with the 8Base ransomware gang. Visitors to the data leak site are now greeted with a seizure banner that says: “This hidden site and the criminal content have been seized by the Bavarian State Criminal…
-

Apple Patches Actively Exploited iOS Zero-Day CVE-2025-24200 in Emergency Update [email protected] (The Hacker News)
Apple on Monday released out-of-band security updates to address a security flaw in iOS and iPadOS that it said has been exploited in the wild. Assigned the CVE identifier CVE-2025-24200, the vulnerability has been described as an authorization issue that could make it possible for a malicious actor to disable USB Restricted Mode on a…
-
DevSecOps platform tucks in API security as AI apps heat up
Post ContentRead More
-
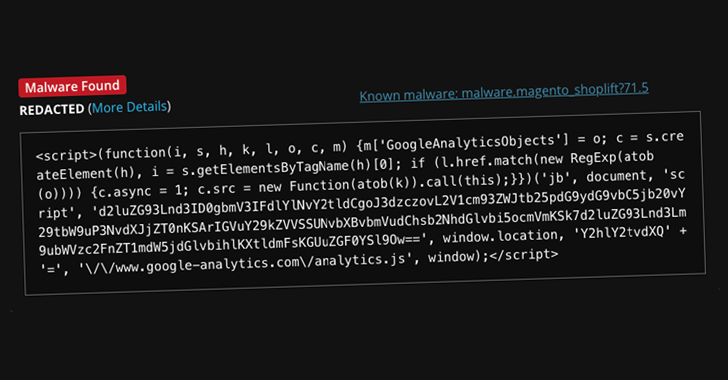
Hackers Exploit Google Tag Manager to Deploy Credit Card Skimmers on Magento Stores [email protected] (The Hacker News)
Threat actors have been observed leveraging Google Tag Manager (GTM) to deliver credit card skimmer malware targeting Magento-based e-commerce websites. Website security company Sucuri said the code, while appearing to be a typical GTM and Google Analytics script used for website analytics and advertising purposes, contains an obfuscated backdoor capable of providing attackers with persistentRead…
-
Trimble Cityworks zero-day flaw under attack, patch now
Post ContentRead More
-
![⚡ THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [10 February] info@thehackernews.com (The Hacker News)](https://sekuritasit.com/wp-content/uploads/2025/02/recap-1fTuLG.png)
⚡ THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [10 February] [email protected] (The Hacker News)
In cybersecurity, the smallest crack can lead to the biggest breaches. A leaked encryption key, an unpatched software bug, or an abandoned cloud storage bucket—each one seems minor until it becomes the entry point for an attack. This week, we’ve seen cybercriminals turn overlooked weaknesses into major security threats, proving once again that no system…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
