“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-

CERT-UA Discovers LAMEHUG Malware Linked to APT28, Using LLM for Phishing Campaign [email protected] (The Hacker News)
The Computer Emergency Response Team of Ukraine (CERT-UA) has disclosed details of a phishing campaign that’s designed to deliver a malware codenamed LAMEHUG. “An obvious feature of LAMEHUG is the use of LLM (large language model), used to generate commands based on their textual representation (description),” CERT-UA said in a Thursday advisory. The activity has…
-
Google Sues 25 Chinese Entities Over BADBOX 2.0 Botnet Affecting 10M Android Devices [email protected] (The Hacker News)
Google on Thursday revealed it’s pursuing legal action in New York federal court against 25 unnamed individuals or entities in China for allegedly operating BADBOX 2.0 botnet and residential proxy infrastructure. “The BADBOX 2.0 botnet compromised over 10 million uncertified devices running Android’s open-source software (Android Open Source Project), which lacks Google’s security protections,”Read More
-
Critical NVIDIA Container Toolkit Flaw Allows Privilege Escalation on AI Cloud Services [email protected] (The Hacker News)
Cybersecurity researchers have disclosed a critical container escape vulnerability in the NVIDIA Container Toolkit that could pose a severe threat to managed AI cloud services. The vulnerability, tracked as CVE-2025-23266, carries a CVSS score of 9.0 out of 10.0. It has been codenamed NVIDIAScape by Google-owned cloud security company Wiz. “NVIDIA Container Toolkit for all…
-

From Backup to Cyber Resilience: Why IT Leaders Must Rethink Backup in the Age of Ransomware [email protected] (The Hacker News)
With IT outages and disruptions escalating, IT teams are shifting their focus beyond simply backing up data to maintaining operations during an incident. One of the key drivers behind this shift is the growing threat of ransomware, which continues to evolve in both frequency and complexity. Ransomware-as-a-Service (RaaS) platforms have made it possible for even…
-
How to calculate cybersecurity ROI for CEOs and boards
Calculating and communicating cybersecurity ROI can help persuade top management to invest. Here’s how to use meaningful, concrete metrics that resonate with business leaders.Read More
-

Hackers Use GitHub Repositories to Host Amadey Malware and Data Stealers, Bypassing Filters [email protected] (The Hacker News)
Threat actors are leveraging public GitHub repositories to host malicious payloads and distribute them via Amadey as part of a campaign observed in April 2025. “The MaaS [malware-as-a-service] operators used fake GitHub accounts to host payloads, tools, and Amadey plug-ins, likely as an attempt to bypass web filtering and for ease of use,” Cisco Talos…
-

Hackers Exploit Apache HTTP Server Flaw to Deploy Linuxsys Cryptocurrency Miner [email protected] (The Hacker News)
Cybersecurity researchers have discovered a new campaign that exploits a known security flaw impacting Apache HTTP Server to deliver a cryptocurrency miner called Linuxsys. The vulnerability in question is CVE-2021-41773 (CVSS score: 7.5), a high-severity path traversal vulnerability in Apache HTTP Server version 2.4.49 that could result in remote code execution. “The attacker leveragesRead More
-
How to detect and fix a rooted Android phone
Rooting is a unique threat for enterprise mobile devices, but there are signs Android administrators and users can look for to detect it and steps they can take to fix it.Read More
-
An explanation of identity and access management
Identity and access management systems safeguard businesses by controlling digital identities, managing access rights and implementing security protocols.Read More
-
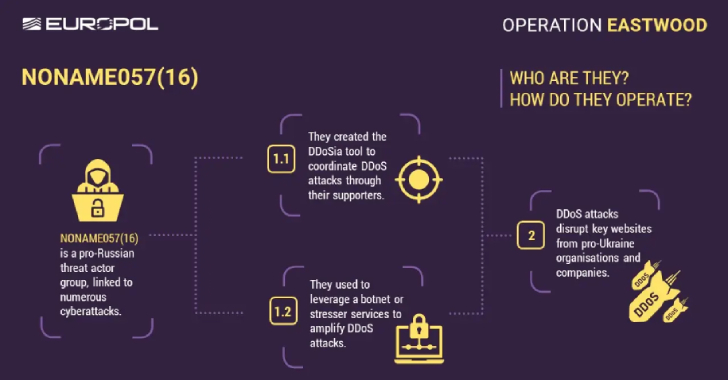
Europol Disrupts NoName057(16) Hacktivist Group Linked to DDoS Attacks Against Ukraine [email protected] (The Hacker News)
An international operation coordinated by Europol has disrupted the infrastructure of a pro-Russian hacktivist group known as NoName057(16) that has been linked to a string of distributed denial-of-service (DDoS) attacks against Ukraine and its allies. The actions have led to the dismantling of a major part of the group’s central server infrastructure and more than…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
