“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
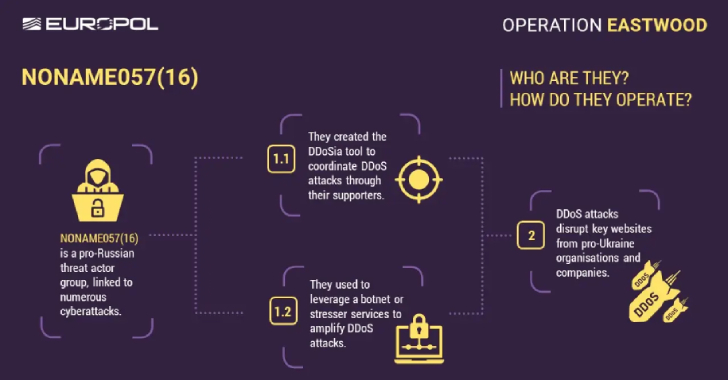
Europol Disrupts NoName057(16) Hacktivist Group Linked to DDoS Attacks Against Ukraine [email protected] (The Hacker News)
An international operation coordinated by Europol has disrupted the infrastructure of a pro-Russian hacktivist group known as NoName057(16) that has been linked to a string of distributed denial-of-service (DDoS) attacks against Ukraine and its allies. The actions have led to the dismantling of a major part of the group’s central server infrastructure and more than…
-

CTEM vs ASM vs Vulnerability Management: What Security Leaders Need to Know in 2025 [email protected] (The Hacker News)
The modern-day threat landscape requires enterprise security teams to think and act beyond traditional cybersecurity measures that are purely passive and reactive, and in most cases, ineffective against emerging threats and sophisticated threat actors. Prioritizing cybersecurity means implementing more proactive, adaptive, and actionable measures that can work together to effectively address theRead More
-
The latest from Black Hat USA 2025
This is your guide to the breaking news, trending topics and more from Black Hat USA 2025, one of the world’s top cybersecurity conferences.Read More
-
Chinese Hackers Target Taiwan’s Semiconductor Sector with Cobalt Strike, Custom Backdoors [email protected] (The Hacker News)
The Taiwanese semiconductor industry has become the target of spear-phishing campaigns undertaken by three Chinese state-sponsored threat actors. “Targets of these campaigns ranged from organizations involved in the manufacturing, design, and testing of semiconductors and integrated circuits, wider equipment and services supply chain entities within this sector, as well as financial investmentRead More
-

Cisco Warns of Critical ISE Flaw Allowing Unauthenticated Attackers to Execute Root Code [email protected] (The Hacker News)
Cisco has disclosed a new maximum-severity security vulnerability impacting Identity Services Engine (ISE) and Cisco ISE Passive Identity Connector (ISE-PIC) that could permit an attacker to execute arbitrary code on the underlying operating system with elevated privileges. Tracked as CVE-2025-20337, the shortcoming carries a CVSS score of 10.0 and is similar to CVE-2025-20281, which was…
-

Hackers Leverage Microsoft Teams to Spread Matanbuchus 3.0 Malware to Targeted Firms [email protected] (The Hacker News)
Cybersecurity researchers have flagged a new variant of a known malware loader called Matanbuchus that packs in significant features to enhance its stealth and evade detection. Matanbuchus is the name given to a malware-as-a-service (MaaS) offering that can act as a conduit for next-stage payloads, including Cobalt Strike beacons and ransomware. First advertised in February…
-

UNC6148 Backdoors Fully-Patched SonicWall SMA 100 Series Devices with OVERSTEP Rootkit [email protected] (The Hacker News)
A threat activity cluster has been observed targeting fully-patched end-of-life SonicWall Secure Mobile Access (SMA) 100 series appliances as part of a campaign designed to drop a backdoor called OVERSTEP. The malicious activity, dating back to at least October 2024, has been attributed by the Google Threat Intelligence Group (GTIG) to a group it tracks…
-
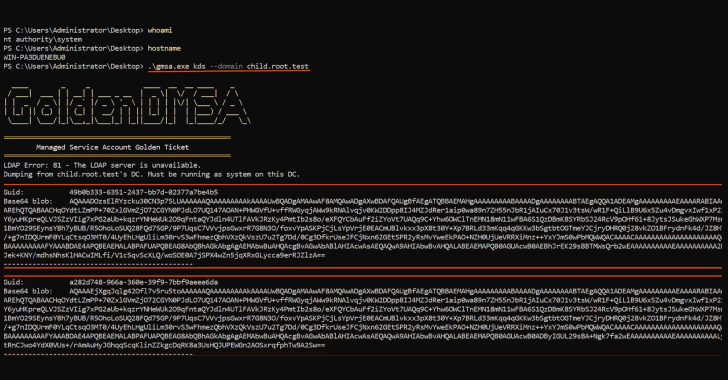
Critical Golden dMSA Attack in Windows Server 2025 Enables Cross-Domain Attacks and Persistent Access [email protected] (The Hacker News)
Cybersecurity researchers have disclosed what they say is a “critical design flaw” in delegated Managed Service Accounts (dMSAs) introduced in Windows Server 2025. “The flaw can result in high-impact attacks, enabling cross-domain lateral movement and persistent access to all managed service accounts and their resources across Active Directory indefinitely,” Semperis said in a report shared…
-

AI Agents Act Like Employees With Root Access—Here’s How to Regain Control [email protected] (The Hacker News)
The AI gold rush is on. But without identity-first security, every deployment becomes an open door. Most organizations secure native AI like a web app, but it behaves more like a junior employee with root access and no manager. From Hype to High Stakes Generative AI has moved beyond the hype cycle. Enterprises are: Deploying…
-
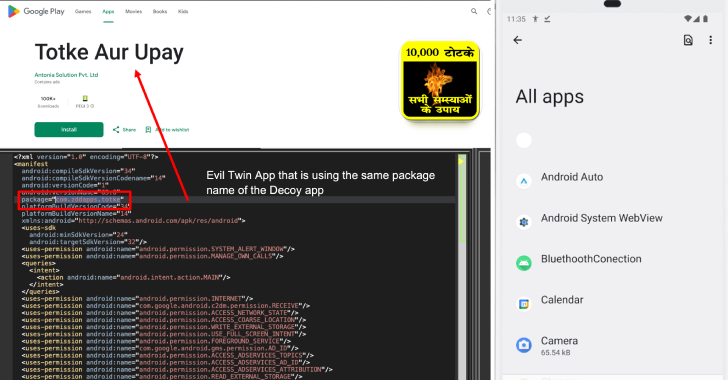
New Konfety Malware Variant Evades Detection by Manipulating APKs and Dynamic Code [email protected] (The Hacker News)
Cybersecurity researchers have discovered a new, sophisticated variant of a known Android malware referred to as Konfety that leverages the evil twin technique to enable ad fraud. The sneaky approach essentially involves a scenario wherein two variants of an application share the same package name: A benign “decoy” app that’s hosted on the Google Play…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
