“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
What is cybersecurity?
Cybersecurity is the practice of protecting systems, networks and data from digital threats.Read More
-
What is cybersecurity mesh? Key applications and benefits
Is it time to consider a different approach to security architecture? Cybersecurity mesh might be an effective way to address complex, distributed environments.Read More
-
What is cloud infrastructure entitlement management (CIEM)?
Cloud infrastructure entitlement management (CIEM) is a modern cloud security discipline for managing identities and privileges in cloud environments.Read More
-

North Korean Hackers Flood npm Registry with XORIndex Malware in Ongoing Attack Campaign [email protected] (The Hacker News)
The North Korean threat actors linked to the Contagious Interview campaign have been observed publishing another set of 67 malicious packages to the npm registry, underscoring ongoing attempts to poison the open-source ecosystem via software supply chain attacks. The packages, per Socket, have attracted more than 17,000 downloads, and incorporate a previously undocumented version of…
-

The Unusual Suspect: Git Repos [email protected] (The Hacker News)
While phishing and ransomware dominate headlines, another critical risk quietly persists across most enterprises: exposed Git repositories leaking sensitive data. A risk that silently creates shadow access into core systems Git is the backbone of modern software development, hosting millions of repositories and serving thousands of organizations worldwide. Yet, amid the daily hustle of shippingRead…
-
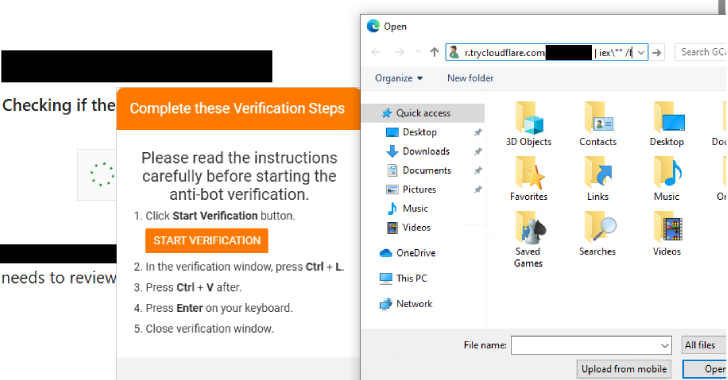
New PHP-Based Interlock RAT Variant Uses FileFix Delivery Mechanism to Target Multiple Industries [email protected] (The Hacker News)
Threat actors behind the Interlock ransomware group have unleashed a new PHP variant of its bespoke remote access trojan (RAT) as part of a widespread campaign using a variant of ClickFix called FileFix. “Since May 2025, activity related to the Interlock RAT has been observed in connection with the LandUpdate808 (aka KongTuke) web-inject threat clusters,”…
-

⚡ Weekly Recap: Scattered Spider Arrests, Car Exploits, macOS Malware, Fortinet RCE and More [email protected] (The Hacker News)
In cybersecurity, precision matters—and there’s little room for error. A small mistake, missed setting, or quiet misconfiguration can quickly lead to much bigger problems. The signs we’re seeing this week highlight deeper issues behind what might look like routine incidents: outdated tools, slow response to risks, and the ongoing gap between compliance and real security.…
-
How CISOs can prepare for the quantum cybersecurity threat
CISOs should begin preparing now for quantum computing’s impact on cybersecurity. Start with assessments and planning before migrating to post-quantum cryptography standards.Read More
-
Prompt injection attacks: From pranks to security threats
Prompt injection attacks manipulate AI systems to bypass security guardrails, enabling data theft and code execution — yet they lack comprehensive defenses and CVE tracking.Read More
-

CBI Shuts Down £390K U.K. Tech Support Scam, Arrests Key Operatives in Noida Call Center [email protected] (The Hacker News)
India’s Central Bureau of Investigation (CBI) has announced that it has taken steps to dismantle what it said was a transnational cybercrime syndicate that carried out “sophisticated” tech support scams targeting citizens of Australia and the United Kingdom. The fraudulent scheme is estimated to have led to losses worth more than £390,000 ($525,000) in the…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
