“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
eSIM Vulnerability in Kigen’s eUICC Cards Exposes Billions of IoT Devices to Malicious Attacks [email protected] (The Hacker News)
Cybersecurity researchers have discovered a new hacking technique that exploits weaknesses in the eSIM technology used in modern smartphones, exposing users to severe risks. The issues impact the Kigen eUICC card. According to the Irish company’s website, more than two billion SIMs in IoT devices have been enabled as of December 2020. The findings come…
-

GPUHammer: New RowHammer Attack Variant Degrades AI Models on NVIDIA GPUs [email protected] (The Hacker News)
NVIDIA is urging customers to enable System-level Error Correction Codes (ECC) as a defense against a variant of a RowHammer attack demonstrated against its graphics processing units (GPUs). “Risk of successful exploitation from RowHammer attacks varies based on DRAM device, platform, design specification, and system settings,” the GPU maker said in an advisory released this…
-
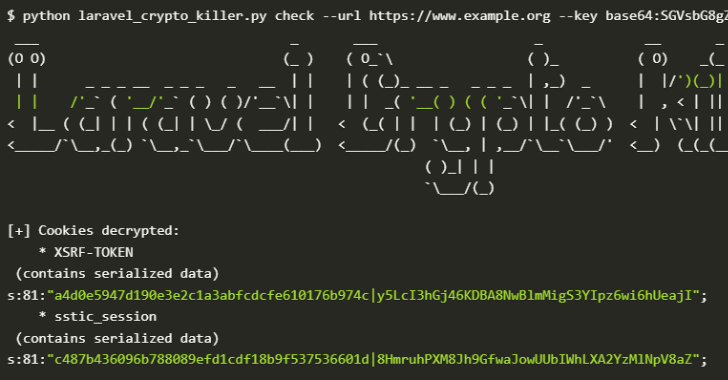
Over 600 Laravel Apps Exposed to Remote Code Execution Due to Leaked APP_KEYs on GitHub [email protected] (The Hacker News)
Cybersecurity researchers have discovered a serious security issue that allows leaked Laravel APP_KEYs to be weaponized to gain remote code execution capabilities on hundreds of applications. “Laravel’s APP_KEY, essential for encrypting sensitive data, is often leaked publicly (e.g., on GitHub),” GitGuardian said. “If attackers get access to this key, they can exploit a deserialization flaw…
-
Next.js Middleware Auth.Bypass Vulnerability
What is the Vulnerability?FortiGuard Labs has identified ongoing attack attempts targeting a critical authorization bypass vulnerability (CVE-2025-29927) in the middleware system of the Next.js framework, a popular React-based framework for building full-stack web applications.The issue arises from improper handling of an internal HTTP header: x-middleware-subrequest. This header, when manipulated, can bypass middleware execution, allowing attackers…
-

Fortinet Releases Patch for Critical SQL Injection Flaw in FortiWeb (CVE-2025-25257) [email protected] (The Hacker News)
Fortinet has released fixes for a critical security flaw impacting FortiWeb that could enable an unauthenticated attacker to run arbitrary database commands on susceptible instances. Tracked as CVE-2025-25257, the vulnerability carries a CVSS score of 9.6 out of a maximum of 10.0. “An improper neutralization of special elements used in an SQL command (‘SQL Injection’)…
-
PerfektBlue Bluetooth Vulnerabilities Expose Millions of Vehicles to Remote Code Execution [email protected] (The Hacker News)
Cybersecurity researchers have discovered a set of four security flaws in OpenSynergy’s BlueSDK Bluetooth stack that, if successfully exploited, could allow remote code execution on millions of transport vehicles from different vendors. The vulnerabilities, dubbed PerfektBlue, can be fashioned together as an exploit chain to run arbitrary code on cars from at least three major…
-
News brief: Hafnium, Scattered Spider hackers arrested
Check out the latest security news from the Informa TechTarget team.Read More
-

Securing Data in the AI Era [email protected] (The Hacker News)
The 2025 Data Risk Report: Enterprises face potentially serious data loss risks from AI-fueled tools. Adopting a unified, AI-driven approach to data security can help. As businesses increasingly rely on cloud-driven platforms and AI-powered tools to accelerate digital transformation, the stakes for safeguarding sensitive enterprise data have reached unprecedented levels. The Zscaler ThreatLabzRead More
-

Critical Wing FTP Server Vulnerability (CVE-2025-47812) Actively Being Exploited in the Wild [email protected] (The Hacker News)
A recently disclosed maximum-severity security flaw impacting the Wing FTP Server has come under active exploitation in the wild, according to Huntress. The vulnerability, tracked as CVE-2025-47812 (CVSS score: 10.0), is a case of improper handling of null (”) bytes in the server’s web interface, which allows for remote code execution. It has been addressed…
-

Iranian-Backed Pay2Key Ransomware Resurfaces with 80% Profit Share for Cybercriminals [email protected] (The Hacker News)
An Iranian-backed ransomware-as-a-service (RaaS) named Pay2Key has resurfaced in the wake of the Israel-Iran-U.S. conflict last month, offering bigger payouts to cybercriminals who launch attacks against Israel and the U.S. The financially motivated scheme, now operating under the moniker Pay2Key.I2P, is assessed to be linked to a hacking group tracked as Fox Kitten (aka Lemon…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
