“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
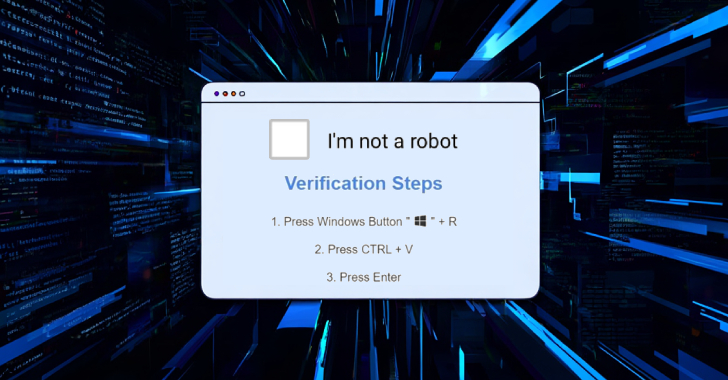
Cybercriminals Deploy CORNFLAKE.V3 Backdoor via ClickFix Tactic and Fake CAPTCHA Pages [email protected] (The Hacker News)
Threat actors have been observed leveraging the deceptive social engineering tactic known as ClickFix to deploy a versatile backdoor codenamed CORNFLAKE.V3. Google-owned Mandiant described the activity, which it tracks as UNC5518, as part of an access-as-a-service scheme that employs fake CAPTCHA pages as lures to trick users into providing initial access to their systems, which…
-
Azure Local aims to answer shifting needs of the enterprise
Microsoft looks to provide a consistent Azure-style experience with its latest infrastructure offering for organizations that face challenges with data sovereignty and compliance.Read More
-
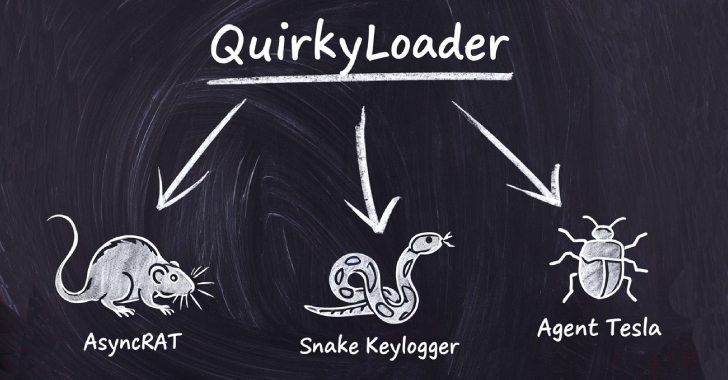
Hackers Using New QuirkyLoader Malware to Spread Agent Tesla, AsyncRAT and Snake Keylogger [email protected] (The Hacker News)
Cybersecurity researchers have disclosed details of a new malware loader called QuirkyLoader that’s being used to deliver via email spam campaigns an array of next-stage payloads ranging from information stealers to remote access trojans since November 2024. Some of the notable malware families distributed using QuirkyLoader include Agent Tesla, AsyncRAT, Formbook, Masslogger, Remcos RAT,Read More
-

Weak Passwords and Compromised Accounts: Key Findings from the Blue Report 2025 [email protected] (The Hacker News)
As security professionals, it’s easy to get caught up in a race to counter the latest advanced adversary techniques. Yet the most impactful attacks often aren’t from cutting-edge exploits, but from cracked credentials and compromised accounts. Despite widespread awareness of this threat vector, Picus Security’s Blue Report 2025 shows that organizations continue to struggle with…
-

Scattered Spider Hacker Gets 10 Years, $13M Restitution for SIM Swapping Crypto Theft [email protected] (The Hacker News)
A 20-year-old member of the notorious cybercrime gang known as Scattered Spider has been sentenced to ten years in prison in the U.S. in connection with a series of major hacks and cryptocurrency thefts. Noah Michael Urban pleaded guilty to charges related to wire fraud and aggravated identity theft back in April 2025. News of…
-

Apple Patches CVE-2025-43300 Zero-Day in iOS, iPadOS, and macOS Exploited in Targeted Attacks [email protected] (The Hacker News)
Apple has released security updates to address a security flaw impacting iOS, iPadOS, and macOS that it said has come under active exploitation in the wild. The zero-day out-of-bounds write vulnerability, tracked as CVE-2025-43300, resides in the ImageIO framework that could result in memory corruption when processing a malicious image. “Apple is aware of a…
-
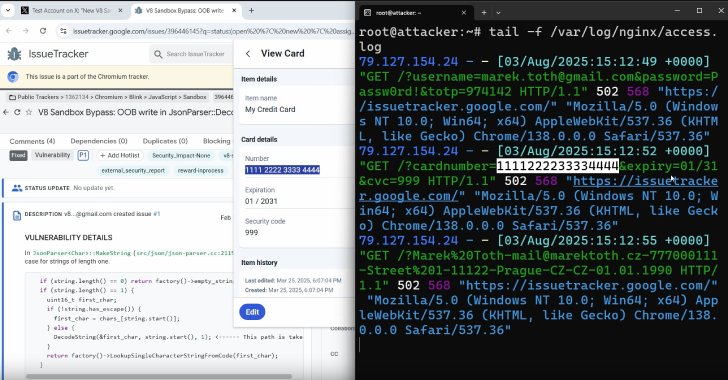
DOM-Based Extension Clickjacking Exposes Popular Password Managers to Credential and Data Theft [email protected] (The Hacker News)
Popular password manager plugins for web browsers have been found susceptible to clickjacking security vulnerabilities that could be exploited to steal account credentials, two-factor authentication (2FA) codes, and credit card details under certain conditions. The technique has been dubbed Document Object Model (DOM)-based extension clickjacking by independent security researcher Marek Tóth,Read More
-

FBI Warns FSB-Linked Hackers Exploiting Unpatched Cisco Devices for Cyber Espionage [email protected] (The Hacker News)
A Russian state-sponsored cyber espionage group known as Static Tundra has been observed actively exploiting a seven-year-old security flaw in Cisco IOS and Cisco IOS XE software as a means to establish persistent access to target networks. Cisco Talos, which disclosed details of the activity, said the attacks single out organizations in telecommunications, higher education…
-
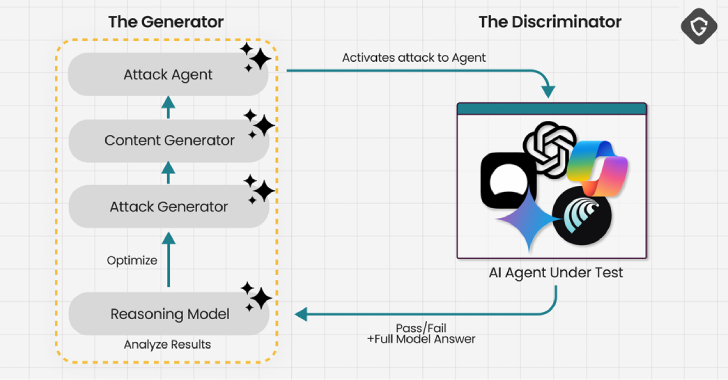
Experts Find AI Browsers Can Be Tricked by PromptFix Exploit to Run Malicious Hidden Prompts [email protected] (The Hacker News)
Cybersecurity researchers have demonstrated a new prompt injection technique called PromptFix that tricks a generative artificial intelligence (GenAI) model into carrying out intended actions by embedding the malicious instruction inside a fake CAPTCHA check on a web page. Described by Guardio Labs an “AI-era take on the ClickFix scam,” the attack technique demonstrates how AI-driven…
-

🕵️ Webinar: Discover and Control Shadow AI Agents in Your Enterprise Before Hackers Do [email protected] (The Hacker News)
Do you know how many AI agents are running inside your business right now? If the answer is “not sure,” you’re not alone—and that’s exactly the concern. Across industries, AI agents are being set up every day. Sometimes by IT, but often by business units moving fast to get results. That means agents are running…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
