“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
12 top enterprise risk management trends in 2025
Trends reshaping risk management include use of GRC platforms, risk maturity models, risk appetite statements and AI tools, plus the need to manage AI risks.Read More
-

Taiwan NSB Alerts Public on Data Risks from TikTok, Weibo, and RedNote Over China Ties [email protected] (The Hacker News)
Taiwan’s National Security Bureau (NSB) has warned that China-developed applications like RedNote (aka Xiaohongshu), Weibo, TikTok, WeChat, and Baidu Cloud pose security risks due to excessive data collection and data transfer to China. The alert comes following an inspection of these apps carried out in coordination with the Ministry of Justice Investigation Bureau (MJIB) and…
-

Alert: Exposed JDWP Interfaces Lead to Crypto Mining, Hpingbot Targets SSH for DDoS [email protected] (The Hacker News)
Threat actors are weaponizing exposed Java Debug Wire Protocol (JDWP) interfaces to obtain code execution capabilities and deploy cryptocurrency miners on compromised hosts. “The attacker used a modified version of XMRig with a hard-“coded configuration, allowing them to avoid suspicious command-line arguments that are often flagged by defenders,” Wiz researchers Yaara Shriki and GiliRead More
-
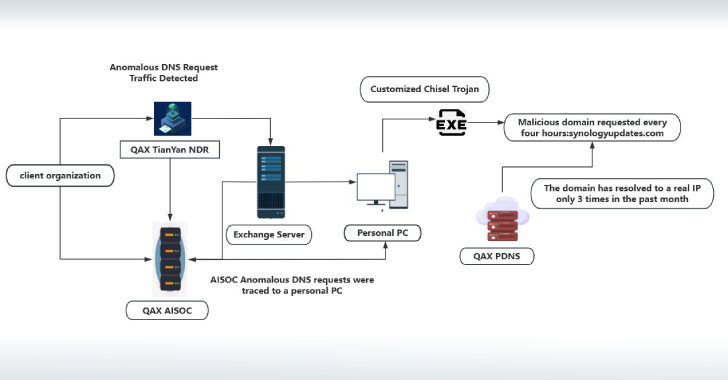
NightEagle APT Exploits Microsoft Exchange Flaw to Target China’s Military and Tech Sectors [email protected] (The Hacker News)
Cybersecurity researchers have shed light on a previously undocumented threat actor called NightEagle (aka APT-Q-95) that has been observed targeting Microsoft Exchange servers as a part of a zero-day exploit chain designed to target government, defense, and technology sectors in China. According to QiAnXin’s RedDrip Team, the threat actor has been active since 2023 and…
-

Your AI Agents Might Be Leaking Data — Watch this Webinar to Learn How to Stop It [email protected] (The Hacker News)
Generative AI is changing how businesses work, learn, and innovate. But beneath the surface, something dangerous is happening. AI agents and custom GenAI workflows are creating new, hidden ways for sensitive enterprise data to leak—and most teams don’t even realize it. If you’re building, deploying, or managing AI systems, now is the time to ask:…
-
Critical Sudo Vulnerabilities Let Local Users Gain Root Access on Linux, Impacting Major Distros [email protected] (The Hacker News)
Cybersecurity researchers have disclosed two security flaws in the Sudo command-line utility for Linux and Unix-like operating systems that could enable local attackers to escalate their privileges to root on susceptible machines. A brief description of the vulnerabilities is below – CVE-2025-32462 (CVSS score: 2.8) – Sudo before 1.9.17p1, when used with a sudoers file…
-

Google Ordered to Pay $314M for Misusing Android Users’ Cellular Data Without Permission [email protected] (The Hacker News)
Google has been ordered by a court in the U.S. state of California to pay $314 million over charges that it misused Android device users’ cellular data when they were idle to passively send information to the company. The verdict marks an end to a legal class-action complaint that was originally filed in August 2019.…
-

Massive Android Fraud Operations Uncovered: IconAds, Kaleidoscope, SMS Malware, NFC Scams [email protected] (The Hacker News)
A mobile ad fraud operation dubbed IconAds that consisted of 352 Android apps has been disrupted, according to a new report from HUMAN. The identified apps were designed to load out-of-context ads on a user’s screen and hide their icons from the device home screen launcher, making it harder for victims to remove them, per…
-

Over 40 Malicious Firefox Extensions Target Cryptocurrency Wallets, Stealing User Assets [email protected] (The Hacker News)
Cybersecurity researchers have uncovered over 40 malicious browser extensions for Mozilla Firefox that are designed to steal cryptocurrency wallet secrets, putting users’ digital assets at risk. “These extensions impersonate legitimate wallet tools from widely-used platforms such as Coinbase, MetaMask, Trust Wallet, Phantom, Exodus, OKX, Keplr, MyMonero, Bitget, Leap, Ethereum Wallet, and FilfoxRead More
-

The Hidden Weaknesses in AI SOC Tools that No One Talks About [email protected] (The Hacker News)
If you’re evaluating AI-powered SOC platforms, you’ve likely seen bold claims: faster triage, smarter remediation, and less noise. But under the hood, not all AI is created equal. Many solutions rely on pre-trained AI models that are hardwired for a handful of specific use cases. While that might work for yesterday’s SOC, today’s reality is…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
