“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-

U.K. Government Drops Apple Encryption Backdoor Order After U.S. Civil Liberties Pushback [email protected] (The Hacker News)
The U.K. government has apparently abandoned its plans to force Apple to weaken encryption protections and include a backdoor that would have enabled access to the protected data of U.S. citizens. U.S. Director of National Intelligence (DNI) Tulsi Gabbard, in a statement posted on X, said the U.S. government had been working with its partners…
-

Why Your Security Culture is Critical to Mitigating Cyber Risk [email protected] (The Hacker News)
After two decades of developing increasingly mature security architectures, organizations are running up against a hard truth: tools and technologies alone are not enough to mitigate cyber risk. As tech stacks have grown more sophisticated and capable, attackers have shifted their focus. They are no longer focusing on infrastructure vulnerabilities alone. Instead, they are increasinglyRead…
-

PyPI Blocks 1,800 Expired-Domain Emails to Prevent Account Takeovers and Supply Chain Attacks [email protected] (The Hacker News)
The maintainers of the Python Package Index (PyPI) repository have announced that the package manager now checks for expired domains to prevent supply chain attacks. “These changes improve PyPI’s overall account security posture, making it harder for attackers to exploit expired domain names to gain unauthorized access to accounts,” Mike Fiedler, PyPI safety and security…
-
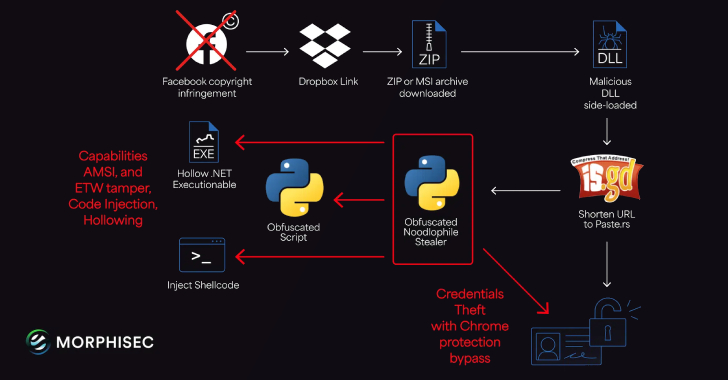
Noodlophile Malware Campaign Expands Global Reach with Copyright Phishing Lures [email protected] (The Hacker News)
The threat actors behind the Noodlophile malware are leveraging spear-phishing emails and updated delivery mechanisms to deploy the information stealer in attacks aimed at enterprises located in the U.S., Europe, Baltic countries, and the Asia-Pacific (APAC) region. “The Noodlophile campaign, active for over a year, now leverages advanced spear-phishing emails posing as copyright infringementRead More
-

Microsoft Windows Vulnerability Exploited to Deploy PipeMagic RansomExx Malware [email protected] (The Hacker News)
Cybersecurity researchers have lifted the lid on the threat actors’ exploitation of a now-patched security flaw in Microsoft Windows to deploy the PipeMagic malware in RansomExx ransomware attacks. The attacks involve the exploitation of CVE-2025-29824, a privilege escalation vulnerability impacting the Windows Common Log File System (CLFS) that was addressed by Microsoft in April 2025,Read…
-

⚡ Weekly Recap: NFC Fraud, Curly COMrades, N-able Exploits, Docker Backdoors & More [email protected] (The Hacker News)
Power doesn’t just disappear in one big breach. It slips away in the small stuff—a patch that’s missed, a setting that’s wrong, a system no one is watching. Security usually doesn’t fail all at once; it breaks slowly, then suddenly. Staying safe isn’t about knowing everything—it’s about acting fast and clear before problems pile up.…
-
An explanation of quantum key distribution
Quantum key distribution uses physics to create secure encryption keys that detect eavesdropping instantly, offering a quantum-safe solution for future cybersecurity challenges.Read More
-

Malicious PyPI and npm Packages Discovered Exploiting Dependencies in Supply Chain Attacks [email protected] (The Hacker News)
Cybersecurity researchers have discovered a malicious package in the Python Package Index (PyPI) repository that introduces malicious behavior through a dependency that allows it to establish persistence and achieve code execution. The package, named termncolor, realizes its nefarious functionality through a dependency package called colorinal by means of a multi-stage malware operation, ZscalerRead More
-

Wazuh for Regulatory Compliance [email protected] (The Hacker News)
Organizations handling various forms of sensitive data or personally identifiable information (PII) require adherence to regulatory compliance standards and frameworks. These compliance standards also apply to organizations operating in regulated sectors such as healthcare, finance, government contracting, or education. Some of these standards and frameworks include, but are not limited to:Read More
-
Shift left with these 11 DevSecOps best practices
By starting small, automating selectively and making security the easiest path forward, organizations can improve DevOps security without sacrificing development speed.Read More
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
