“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
What is AWS Certified Solutions Architect – Associate?
AWS Certified Solutions Architect – Associate is a certification for IT professionals who use Amazon Web Services to design and implement cloud solutions.Read More
-
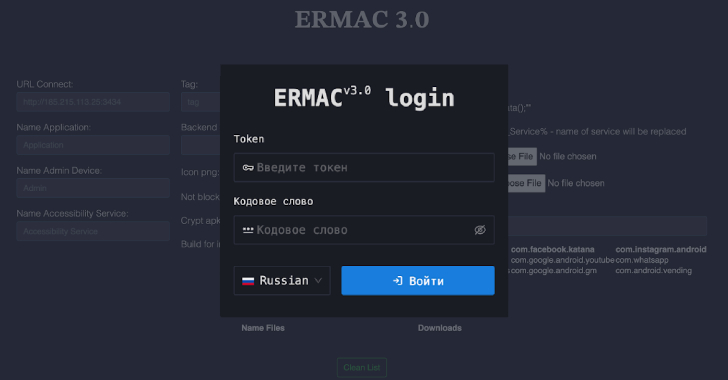
ERMAC V3.0 Banking Trojan Source Code Leak Exposes Full Malware Infrastructure [email protected] (The Hacker News)
Cybersecurity researchers have detailed the inner workings of an Android banking trojan called ERMAC 3.0, uncovering serious shortcomings in the operators’ infrastructure. “The newly uncovered version 3.0 reveals a significant evolution of the malware, expanding its form injection and data theft capabilities to target more than 700 banking, shopping, and cryptocurrency applications,”Read More
-

Russian Group EncryptHub Exploits MSC EvilTwin Vulnerability to Deploy Fickle Stealer Malware [email protected] (The Hacker News)
The threat actor known as EncryptHub is continuing to exploit a now-patched security flaw impacting Microsoft Windows to deliver malicious payloads. Trustwave SpiderLabs said it recently observed an EncryptHub campaign that brings together social engineering and the exploitation of a vulnerability in the Microsoft Management Console (MMC) framework (CVE-2025-26633, aka MSC EvilTwin) to triggerRead More
-

Taiwan Web Servers Breached by UAT-7237 Using Customized Open-Source Hacking Tools [email protected] (The Hacker News)
A Chinese-speaking advanced persistent threat (APT) actor has been observed targeting web infrastructure entities in Taiwan using customized versions of open-sourced tools with an aim to establish long-term access within high-value victim environments. The activity has been attributed by Cisco Talos to an activity cluster it tracks as UAT-7237, which is believed to be active…
-
News brief: Rising OT threats put critical infrastructure at risk
Check out the latest security news from the Informa TechTarget team.Read More
-
How to write a data classification policy, with template
Data classification policies help organizations categorize, secure and manage sensitive information while maintaining regulatory compliance and reducing breach risks.Read More
-
U.S. Sanctions Garantex and Grinex Over $100M in Ransomware-Linked Illicit Crypto Transactions [email protected] (The Hacker News)
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) on Thursday renewed sanctions against Russian cryptocurrency exchange platform Garantex for facilitating ransomware actors and other cybercriminals by processing more than $100 million in transactions linked to illicit activities since 2019. The Treasury said it’s also imposing sanctions on Garantex’s successor, GrinexRead More
-
An explanation of post-quantum cryptography
Quantum computers threaten to break today’s encryption protocols. Post-quantum cryptography aims to develop new algorithms resistant to quantum attacks before it’s too late.Read More
-
Zero Trust + AI: Privacy in the Age of Agentic AI [email protected] (The Hacker News)
We used to think of privacy as a perimeter problem: about walls and locks, permissions, and policies. But in a world where artificial agents are becoming autonomous actors — interacting with data, systems, and humans without constant oversight — privacy is no longer about control. It’s about trust. And trust, by definition, is about what…
-
SSH tunneling explained: A tutorial on SSH port forwarding
SSH tunneling creates secure encrypted connections through private and untrusted networks, enabling remote access, bypassing restrictions and protecting sensitive data transfers.Read More
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
