“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
Email Security Is Stuck in the Antivirus Era: Why It Needs a Modern Approach [email protected] (The Hacker News)
Picture this: you’ve hardened every laptop in your fleet with real‑time telemetry, rapid isolation, and automated rollback. But the corporate mailbox—the front door for most attackers—is still guarded by what is effectively a 1990s-era filter. This isn’t a balanced approach. Email remains a primary vector for breaches, yet we often treat it as a static…
-
What is a content delivery network?
A content delivery network (CDN), also called a content distribution network, is a group of geographically distributed and interconnected servers.Read More
-
DLP and DSPM: Navigate policy challenges and quiet alert noise
As practitioners battle DLP policy inconsistency and alert fatigue, a wave of complementary DSPM deployments is coming. Learn how to get the most bang for your buck.Read More
-

Scattered Spider Hijacks VMware ESXi to Deploy Ransomware on Critical U.S. Infrastructure [email protected] (The Hacker News)
The notorious cybercrime group known as Scattered Spider is targeting VMware ESXi hypervisors in attacks targeting retail, airline, and transportation sectors in North America. “The group’s core tactics have remained consistent and do not rely on software exploits. Instead, they use a proven playbook centered on phone calls to an IT help desk,” Google’s Mandiant…
-
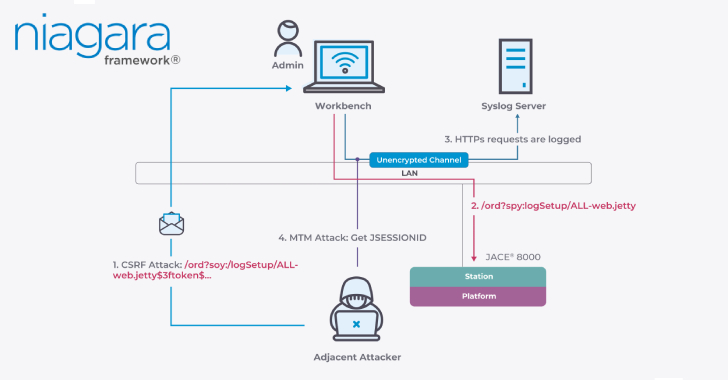
Critical Flaws in Niagara Framework Threaten Smart Buildings and Industrial Systems Worldwide [email protected] (The Hacker News)
Cybersecurity researchers have discovered over a dozen security vulnerabilities impacting Tridium’s Niagara Framework that could allow an attacker on the same network to compromise the system under certain circumstances. “These vulnerabilities are fully exploitable if a Niagara system is misconfigured, thereby disabling encryption on a specific network device,” Nozomi Networks Labs said in aRead More
-

U.S. Sanctions Firm Behind N. Korean IT Scheme; Arizona Woman Jailed for Running Laptop Farm [email protected] (The Hacker News)
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctioned a North Korean front company and three associated individuals for their involvement in the fraudulent remote information technology (IT) worker scheme designed to generate illicit revenues for Pyongyang. The sanctions target Korea Sobaeksu Trading Company (aka Sobaeksu United Corporation), and Kim Se…
-
News brief: SharePoint attacks hammer globe
Check out the latest security news from the Informa TechTarget team.Read More
-
Patchwork Targets Turkish Defense Firms with Spear-Phishing Using Malicious LNK Files [email protected] (The Hacker News)
The threat actor known as Patchwork has been attributed to a new spear-phishing campaign targeting Turkish defense contractors with the goal of gathering strategic intelligence. “The campaign employs a five-stage execution chain delivered via malicious LNK files disguised as conference invitations sent to targets interested in learning more about unmanned vehicle systems,” Arctic Wolf Labs…
-

Cyber Espionage Campaign Hits Russian Aerospace Sector Using EAGLET Backdoor [email protected] (The Hacker News)
Russian aerospace and defense industries have become the target of a cyber espionage campaign that delivers a backdoor called EAGLET to facilitate data exfiltration. The activity, dubbed Operation CargoTalon, has been assigned to a threat cluster tracked as UNG0901 (short for Unknown Group 901). “The campaign is aimed at targeting employees of Voronezh Aircraft Production…
-
How to discover and manage shadow APIs
Connecting applications, especially if external-facing, with unapproved APIs is a recipe for disaster. Detecting and managing shadow APIs is vital to keeping the company secure.Read More
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
