“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
How to implement security control rationalization
Security control rationalization helps CISOs reduce cybersecurity tool sprawl, cut spending and improve efficiency — all without compromising protection.Read More
-
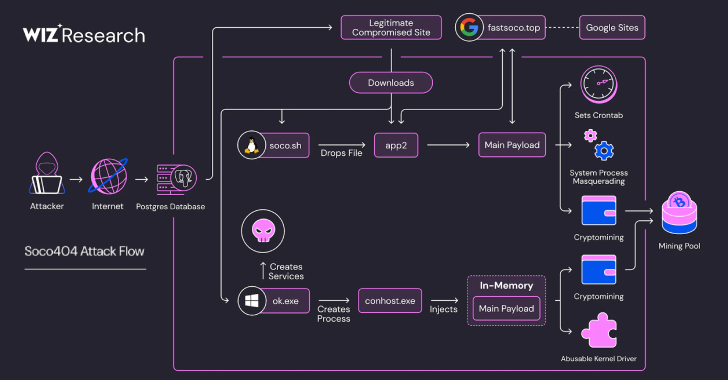
Soco404 and Koske Malware Target Cloud Services with Cross-Platform Cryptomining Attacks [email protected] (The Hacker News)
Threat hunters have disclosed two different malware campaigns that have targeted vulnerabilities and misconfigurations across cloud environments to deliver cryptocurrency miners. The threat activity clusters have been codenamed Soco404 and Koske by cloud security firms Wiz and Aqua, respectively. Soco404 “targets both Linux and Windows systems, deploying platform-specific malware,” WizRead More
-

Overcoming Risks from Chinese GenAI Tool Usage [email protected] (The Hacker News)
A recent analysis of enterprise data suggests that generative AI tools developed in China are being used extensively by employees in the US and UK, often without oversight or approval from security teams. The study, conducted by Harmonic Security, also identifies hundreds of instances in which sensitive data was uploaded to platforms hosted in China,…
-
Proof-of-Concept Code Now Available for an Exploited Windows Local Privilege Escalation Vulnerability
FortiGuard Labs is aware that a Proof-of-Concept (POC) code for a newly patched Windows vulnerability (CVE-2022-21882) that is reported to have been exploited in the wild was released to a publicly available online repository. CVE-2022-21882 is a local privilege (LPE) escalation vulnerability which allows a local, authenticated attacker to gain elevated local system or administrator…
-
Joint CyberSecurity Advisory Alert on PrintNightmare Vulnerability and Default MFA Protocols Exploited by Russian State-Sponsored Cyber Actors (AA22-074A)
FortiGuard Labs is aware of a recent report issued by the U.S. Federal Bureau of Investigation (FBI) and Cybersecurity and Infrastructure Security Agency (CISA) that Russian state-sponsored cyber actors have gained network access to a non-governmental organization (NGO) through exploitation of default Multi-Factor Authentication (MFA) protocols and the “PrintNightmare” vulnerability (CVE-2021-34527). The attack resulted in…
-

Critical Mitel Flaw Lets Hackers Bypass Login, Gain Full Access to MiVoice MX-ONE Systems [email protected] (The Hacker News)
Mitel has released security updates to address a critical security flaw in MiVoice MX-ONE that could allow an attacker to bypass authentication protections. “An authentication bypass vulnerability has been identified in the Provisioning Manager component of Mitel MiVoice MX-ONE, which, if successfully exploited, could allow an unauthenticated attacker to conduct an authentication bypass attackRead More
-

Fire Ant Exploits VMware Flaws to Compromise ESXi Hosts and vCenter Environments [email protected] (The Hacker News)
Virtualization and networking infrastructure have been targeted by a threat actor codenamed Fire Ant as part of a prolonged cyber espionage campaign. The activity, observed this year, is primarily designed Now to infiltrate organizations’ VMware ESXi and vCenter environments as well as network appliances, Sygnia said in a new report published today. “The threat actor…
-
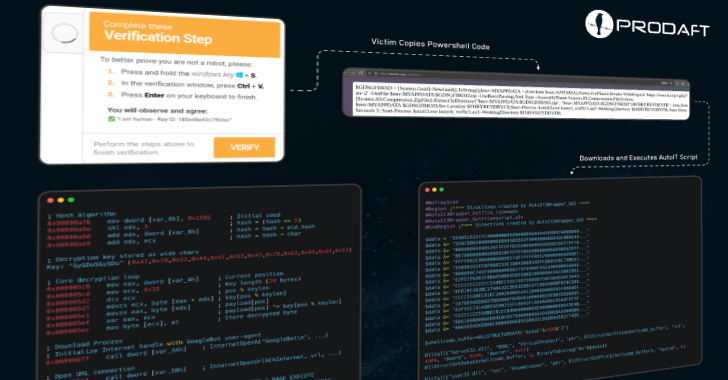
CastleLoader Malware Infects 469 Devices Using Fake GitHub Repos and ClickFix Phishing [email protected] (The Hacker News)
Cybersecurity researchers have shed light on a new versatile malware loader called CastleLoader that has been put to use in campaigns distributing various information stealers and remote access trojans (RATs). The activity employs Cloudflare-themed ClickFix phishing attacks and fake GitHub repositories opened under the names of legitimate applications, Swiss cybersecurity company PRODAFT said inRead More
-

Sophos and SonicWall Patch Critical RCE Flaws Affecting Firewalls and SMA 100 Devices [email protected] (The Hacker News)
Sophos and SonicWall have alerted users of critical security flaws in Sophos Firewall and Secure Mobile Access (SMA) 100 Series appliances that could be exploited to achieve remote code execution. The two vulnerabilities impacting Sophos Firewall are listed below – CVE-2025-6704 (CVSS score: 9.8) – An arbitrary file writing vulnerability in the Secure PDF eXchange…
-
Watch This Webinar to Uncover Hidden Flaws in Login, AI, and Digital Trust — and Fix Them [email protected] (The Hacker News)
Is Managing Customer Logins and Data Giving You Headaches? You’re Not Alone! Today, we all expect super-fast, secure, and personalized online experiences. But let’s be honest, we’re also more careful about how our data is used. If something feels off, trust can vanish in an instant. Add to that the lightning-fast changes AI is bringing…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
