“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
What is crypto ransomware? How cryptocurrency aids attackers
Crypto ransomware is a form of ransomware that uses cryptography to encrypt computer files so that the victim cannot access them. In exchange for the demanded ransom, the attacker claims it will tell the victimized business how to regain access to the stolen data.Read More
-
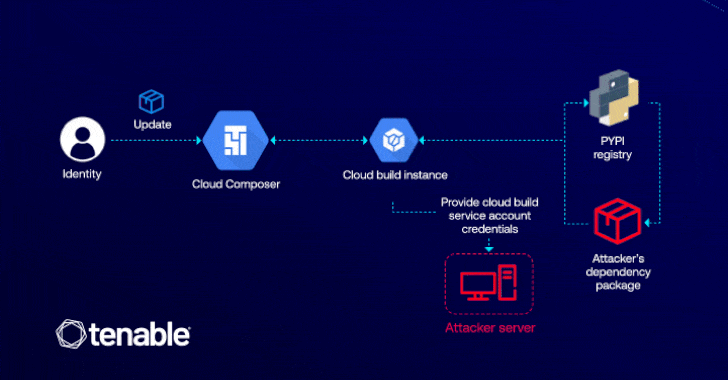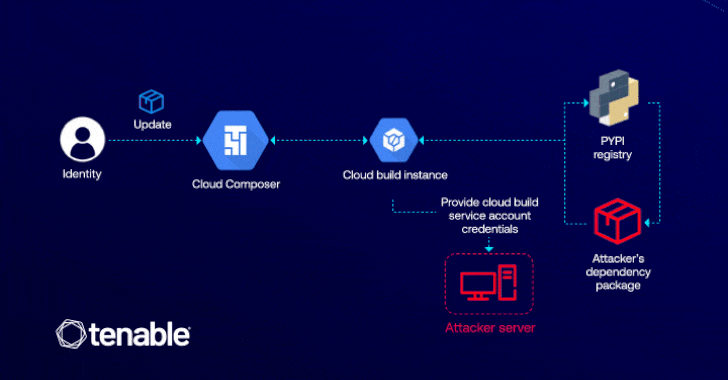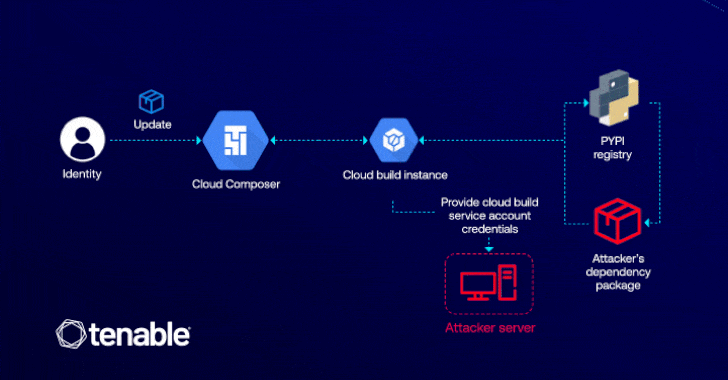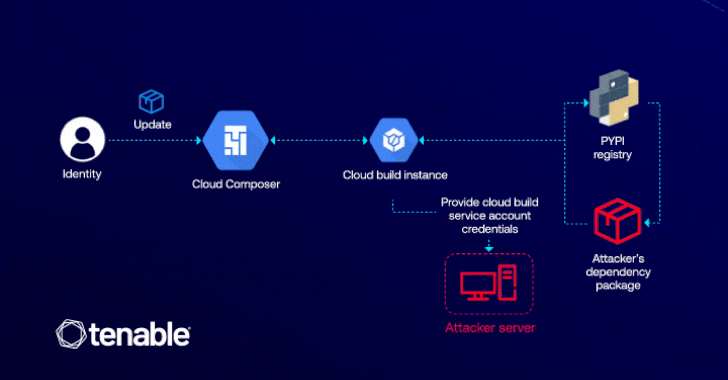
GCP Cloud Composer Bug Let Attackers Elevate Access via Malicious PyPI Packages [email protected] (The Hacker News)
Cybersecurity researchers have detailed a now-patched vulnerability in Google Cloud Platform (GCP) that could have enabled an attacker to elevate their privileges in the Cloud Composer workflow orchestration service that’s based on Apache Airflow. “This vulnerability lets attackers with edit permissions in Cloud Composer to escalate their access to the default Cloud Build service account,…
-
Docker plans Model Context Protocol security boost
Docker said it plans new tools integrating the emerging agentic AI standard protocol into existing workflows, including security controls.Read More
-
Top 10 document management software in 2025
Many organizations require document management software that can automate workflows, support remote access and maintain compliance. Top systems include Box and SharePoint Online.Read More
-

5 Major Concerns With Employees Using The Browser [email protected] (The Hacker News)
As SaaS and cloud-native work reshape the enterprise, the web browser has emerged as the new endpoint. However, unlike endpoints, browsers remain mostly unmonitored, despite being responsible for more than 70% of modern malware attacks. Keep Aware’s recent State of Browser Security report highlights major concerns security leaders face with employees using the web browser…
-

Phishers Exploit Google Sites and DKIM Replay to Send Signed Emails, Steal Credentials [email protected] (The Hacker News)
In what has been described as an “extremely sophisticated phishing attack,” threat actors have leveraged an uncommon approach that allowed bogus emails to be sent via Google’s infrastructure and redirect message recipients to fraudulent sites that harvest their credentials. “The first thing to note is that this is a valid, signed email – it really…
-
The AI market does not understand AI safety
Responsible AI is often misunderstood as a way to make sure that a model is safe. However, AI safety examines whether harmful content is being produced or not.Read More
-

Microsoft Secures MSA Signing with Azure Confidential VMs Following Storm-0558 Breach [email protected] (The Hacker News)
Microsoft on Monday announced that it has moved the Microsoft Account (MSA) signing service to Azure confidential virtual machines (VMs) and that it’s also in the process of migrating the Entra ID signing service as well. The disclosure comes about seven months after the tech giant said it completed updates to Microsoft Entra ID and…
-

Lotus Panda Hacks SE Asian Governments With Browser Stealers and Sideloaded Malware [email protected] (The Hacker News)
The China-linked cyber espionage group tracked as Lotus Panda has been attributed to a campaign that compromised multiple organizations in an unnamed Southeast Asian country between August 2024 and February 2025. “Targets included a government ministry, an air traffic control organization, a telecoms operator, and a construction company,” the Symantec Threat Hunter Team said in…
-
Erlang/OTP RCE (CVE-2025-32433)
What is the Vulnerability? A critical SSH vulnerability has recently been identified in the Erlang/Open Telecom Platform (OTP). The vulnerability, tracked as CVE-2025-32433, has been assigned a CVSS score of 10.0. It is unauthenticated, remotely exploitable, and requires low complexity to execute.Erlang/OTP is commonly found in IoT devices and telecommunications platforms, and is prominently used…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
