“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
Erlang/OTP RCE (CVE-2025-32433)
What is the Vulnerability? A critical SSH vulnerability has recently been identified in the Erlang/Open Telecom Platform (OTP). The vulnerability, tracked as CVE-2025-32433, has been assigned a CVSS score of 10.0. It is unauthenticated, remotely exploitable, and requires low complexity to execute.Erlang/OTP is commonly found in IoT devices and telecommunications platforms, and is prominently used…
-

Kimsuky Exploits BlueKeep RDP Vulnerability to Breach Systems in South Korea and Japan [email protected] (The Hacker News)
Cybersecurity researchers have flagged a new malicious campaign related to the North Korean state-sponsored threat actor known as Kimsuky that exploits a now-patched vulnerability impacting Microsoft Remote Desktop Services to gain initial access. The activity has been named Larva-24005 by the AhnLab Security Intelligence Center (ASEC). “In some systems, initial access was gained throughRead More
-
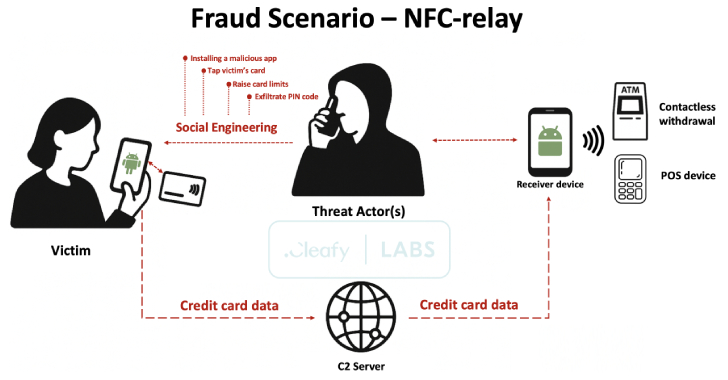
SuperCard X Android Malware Enables Contactless ATM and PoS Fraud via NFC Relay Attacks [email protected] (The Hacker News)
A new Android malware-as-a-service (MaaS) platform named SuperCard X can facilitate near-field communication (NFC) relay attacks, enabling cybercriminals to conduct fraudulent cashouts. The active campaign is targeting customers of banking institutions and card issuers in Italy with an aim to compromise payment card data, fraud prevention firm Cleafy said in an analysis. There is evidence…
-
What is a mobile VPN?
A mobile virtual private network (mobile VPN) is a type of VPN specifically designed to maintain a stable and secure connection while a user moves across different networks.Read More
-

5 Reasons Device Management Isn’t Device Trust [email protected] (The Hacker News)
The problem is simple: all breaches start with initial access, and initial access comes down to two primary attack vectors – credentials and devices. This is not news; every report you can find on the threat landscape depicts the same picture. The solution is more complex. For this article, we’ll focus on the device threat…
-

⚡ THN Weekly Recap: iOS Zero-Days, 4Chan Breach, NTLM Exploits, WhatsApp Spyware & More [email protected] (The Hacker News)
Can a harmless click really lead to a full-blown cyberattack? Surprisingly, yes — and that’s exactly what we saw in last week’s activity. Hackers are getting better at hiding inside everyday actions: opening a file, running a project, or logging in like normal. No loud alerts. No obvious red flags. Just quiet entry through small…
-
What is a brute-force attack?
A brute-force attack is a trial-and-error hacking method cybercriminals use to decode login information and encryption keys to gain unauthorized access to systems.Read More
-
How to create a CBOM for quantum readiness
Quantum is on the horizon — is your organization ready to migrate to post-quantum cryptographic algorithms? Make a CBOM to understand where risky encryption algorithms are used.Read More
-

Hackers Abuse Russian Bulletproof Host Proton66 for Global Attacks and Malware Delivery [email protected] (The Hacker News)
Cybersecurity researchers have disclosed a surge in “mass scanning, credential brute-forcing, and exploitation attempts” originating from IP addresses associated with a Russian bulletproof hosting service provider named Proton66. The activity, detected since January 8, 2025, targeted organizations worldwide, according to a two-part analysis published by Trustwave SpiderLabs last week. “NetRead More
-
Top 5 ransomware attack vectors and how to avoid them
Protecting your organization against ransomware attack entryways could mean the difference between staying safe or falling victim to a devastating breach.Read More
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
