“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
How do cybercriminals steal credit card information?
Cybercriminals have various methods at their disposal to hack and exploit credit card information. Learn what they are, how to prevent them and what to do when hacked.Read More
-

Multi-Stage Malware Attack Uses .JSE and PowerShell to Deploy Agent Tesla and XLoader [email protected] (The Hacker News)
A new multi-stage attack has been observed delivering malware families like Agent Tesla variants, Remcos RAT, and XLoader. “Attackers increasingly rely on such complex delivery mechanisms to evade detection, bypass traditional sandboxes, and ensure successful payload delivery and execution,” Palo Alto Networks Unit 42 researcher Saqib Khanzada said in a technical write-up of the campaign.…
-
Try these strategies to modernize Windows workloads
Legacy applications create tough choices for admins who must balance business needs and security. This article covers these challenges and modernization strategies.Read More
-
![[Webinar] AI Is Already Inside Your SaaS Stack — Learn How to Prevent the Next Silent Breach info@thehackernews.com (The Hacker News)](https://sekuritasit.com/wp-content/uploads/2025/04/ai-cyber-ShIgfI.jpeg)
[Webinar] AI Is Already Inside Your SaaS Stack — Learn How to Prevent the Next Silent Breach [email protected] (The Hacker News)
Your employees didn’t mean to expose sensitive data. They just wanted to move faster. So they used ChatGPT to summarize a deal. Uploaded a spreadsheet to an AI-enhanced tool. Integrated a chatbot into Salesforce. No big deal—until it is. If this sounds familiar, you’re not alone. Most security teams are already behind in detecting how…
-
Availity eyes GitLab Duo with Amazon Q for code refactoring
The healthcare network’s release engineering team is testing the new AI agent pairing to help with code consolidation, modernization and risk mitigation.Read More
-
The history and evolution of ransomware attacks
Ransomware creators have become more innovative and savvier as organizations up their defenses.Read More
-
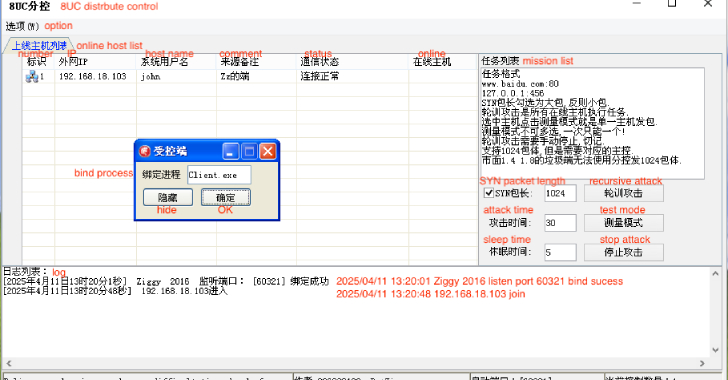
Experts Uncover New XorDDoS Controller, Infrastructure as Malware Expands to Docker, Linux, IoT [email protected] (The Hacker News)
Cybersecurity researchers are warning of continued risks posed by a distributed denial-of-service (DDoS) malware known as XorDDoS, with 71.3 percent of the attacks between November 2023 and February 2025 targeting the United States. “From 2020 to 2023, the XorDDoS trojan has increased significantly in prevalence,” Cisco Talos researcher Joey Chen said in a Thursday analysis. Read…
-
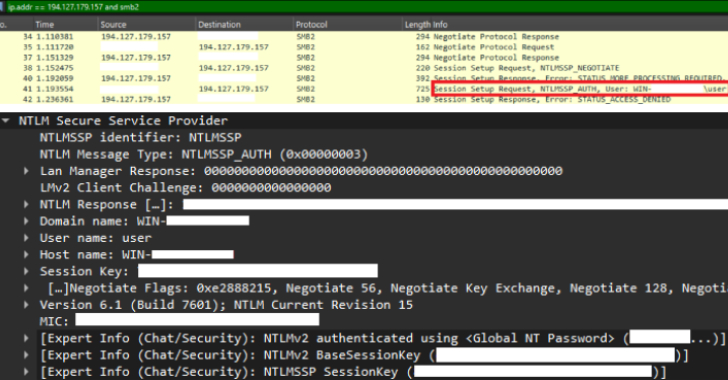
CVE-2025-24054 Under Active Attack—Steals NTLM Credentials on File Download [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a medium-severity security flaw impacting Microsoft Windows to its Known Exploited Vulnerabilities (KEV) catalog, following reports of active exploitation in the wild. The vulnerability, assigned the CVE identifier CVE-2025-24054 (CVSS score: 6.5), is a Windows New Technology LAN Manager (NTLM) hash disclosureRead More
-
Building mobile security awareness training for end users
Do concerns of malware, social engineering and unpatched software on employee mobile devices have you up at night? One good place to start is mobile security awareness training.Read More
-

Mustang Panda Targets Myanmar With StarProxy, EDR Bypass, and TONESHELL Updates [email protected] (The Hacker News)
The China-linked threat actor known as Mustang Panda has been attributed to a cyber attack targeting an unspecified organization in Myanmar with previously unreported tooling, highlighting continued effort by the threat actors to increase the sophistication and effectiveness of their malware. This includes updated versions of a known backdoor called TONESHELL, as well as a…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
