“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
How to create a data breach response plan, with free template
A data breach response plan outlines how a business reacts to a breach. Follow these six steps, and use our free template to develop your organization’s plan.Read More
-
Data security and identity security themes at RSAC 2025
Check out what Enterprise Strategy Group analyst Todd Thiemann has on his agenda for RSA Conference 2025.Read More
-

PipeMagic Trojan Exploits Windows Zero-Day Vulnerability to Deploy Ransomware [email protected] (The Hacker News)
Microsoft has revealed that a now-patched security flaw impacting the Windows Common Log File System (CLFS) was exploited as a zero-day in ransomware attacks aimed at a small number of targets. “The targets include organizations in the information technology (IT) and real estate sectors of the United States, the financial sector in Venezuela, a Spanish…
-

CISA Warns of CentreStack’s Hard-Coded MachineKey Vulnerability Enabling RCE Attacks [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical security flaw impacting Gladinet CentreStack to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. The vulnerability, tracked as CVE-2025-30406 (CVSS score: 9.0), concerns a case of a hard-coded cryptographic key that could be abused to achieve…
-

Microsoft Patches 126 Flaws Including Actively Exploited Windows CLFS Vulnerability [email protected] (The Hacker News)
Microsoft has released security fixes to address a massive set of 126 flaws affecting its software products, including one vulnerability that it said has been actively exploited in the wild. Of the 126 vulnerabilities, 11 are rated Critical, 112 are rated Important, and two are rated Low in severity. Forty-nine of these vulnerabilities are classified…
-
CrushFTP Authentication Bypass
What is the Vulnerability?FortiGuard Labs has observed in-the-wild attack attempts targeting CVE-2025-31161, an authentication bypass vulnerability in CrushFTP managed file transfer (MFT) software. Successful exploitation may grant attackers administrative access to the application, posing a serious threat to enterprise environments.The vulnerability is remotely exploitable, and a proof-of-concept (PoC) exploit is now publicly available. This increases…
-

Adobe Patches 11 Critical ColdFusion Flaws Amid 30 Total Vulnerabilities Discovered [email protected] (The Hacker News)
Adobe has released security updates to fix a fresh set of security flaws, including multiple critical-severity bugs in ColdFusion versions 2025, 2023 and 2021 that could result in arbitrary file read and code execution. Of the 30 flaws in the product, 11 are rated Critical in severity – CVE-2025-24446 (CVSS score: 9.1) – An improper input…
-
Quantum-resistant algorithms: Why they matter
Quantum-resistant algorithms play a crucial role in post-quantum cryptography, which protects against threats on digital signatures and current encryption methods.Read More
-

Fortinet Urges FortiSwitch Upgrades to Patch Critical Admin Password Change Flaw [email protected] (The Hacker News)
Fortinet has released security updates to address a critical security flaw impacting FortiSwitch that could permit an attacker to make unauthorized password changes. The vulnerability, tracked as CVE-2024-48887, carries a CVSS score of 9.3 out of a maximum of 10.0. “An unverified password change vulnerability [CWE-620] in FortiSwitch GUI may allow a remote unauthenticated attacker…
-
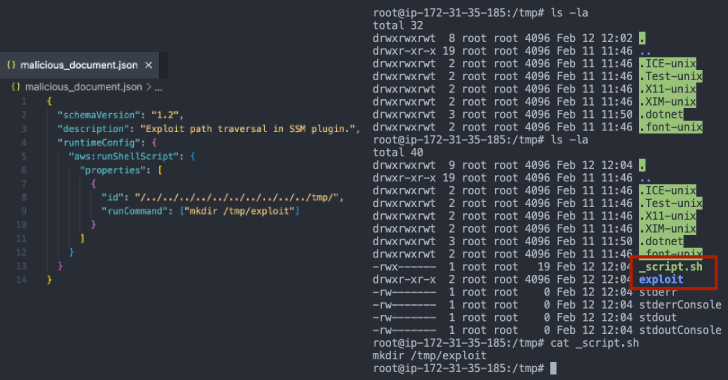
Amazon EC2 SSM Agent Flaw Patched After Privilege Escalation via Path Traversal [email protected] (The Hacker News)
Cybersecurity researchers have disclosed details of a now-patched security flaw in the Amazon EC2 Simple Systems Manager (SSM) Agent that, if successfully exploited, could permit an attacker to achieve privilege escalation and code execution. The vulnerability could permit an attacker to create directories in unintended locations on the filesystem, execute arbitrary scripts with root privileges,Read…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
