“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
IPsec vs. SSL VPNs: What are the differences?
New technologies get all the headlines, but VPNs aren’t going away anytime soon. Speed and security are among the factors to consider when determining what type of VPN to use.Read More
-

Critical Ivanti Flaw Actively Exploited to Deploy TRAILBLAZE and BRUSHFIRE Malware [email protected] (The Hacker News)
Ivanti has disclosed details of a now-patched critical security vulnerability impacting its Connect Secure that has come under active exploitation in the wild. The vulnerability, tracked as CVE-2025-22457 (CVSS score: 9.0), concerns a case of a stack-based buffer overflow that could be exploited to execute arbitrary code on affected systems. “A stack-based buffer overflow in…
-

OPSEC Failure Exposes Coquettte’s Malware Campaigns on Bulletproof Hosting Servers [email protected] (The Hacker News)
A novice cybercrime actor has been observed leveraging the services of a Russian bulletproof hosting (BPH) provider called Proton66 to facilitate their operations. The findings come from DomainTools, which detected the activity after it discovered a phony website named cybersecureprotect[.]com hosted on Proton66 that masqueraded as an antivirus service. The threat intelligence firm said itRead…
-
CERT-UA Reports Cyberattacks Targeting Ukrainian State Systems with WRECKSTEEL Malware [email protected] (The Hacker News)
The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed that no less than three cyber attacks were recorded against state administration bodies and critical infrastructure facilities in the country with an aim to steal sensitive data. The campaign, the agency said, involved the use of compromised email accounts to send phishing messages containing links…
-

Critical Flaw in Apache Parquet Allows Remote Attackers to Execute Arbitrary Code [email protected] (The Hacker News)
A maximum severity security vulnerability has been disclosed in Apache Parquet’s Java Library that, if successfully exploited, could allow a remote attacker to execute arbitrary code on susceptible instances. Apache Parquet is a free and open-source columnar data file format that’s designed for efficient data processing and retrieval, providing support for complex data, high-performanceRead More
-
Kubernetes Ingress-nginx Controller RCE
What is the Vulnerability?On March 24, researchers disclosed a set of five vulnerabilities, collectively known as “IngressNightmare,” affecting Ingress-nginx, one of the popular ingress controllers available for Kubernetes. Using Ingress-NGINX is one of the most common methods for exposing Kubernetes applications externally.CVE-2025-1974 is considered the most serious of the five and has been assigned a…
-
How to detect and remove malware from an Android device
Mobile malware can come in many forms, but users might not know how to identify it. Understand the signs to be wary of on Android devices, as well as what to do to remove malware.Read More
-

Microsoft Warns of Tax-Themed Email Attacks Using PDFs and QR Codes to Deliver Malware [email protected] (The Hacker News)
Microsoft is warning of several phishing campaigns that are leveraging tax-related themes to deploy malware and steal credentials. “These campaigns notably use redirection methods such as URL shorteners and QR codes contained in malicious attachments and abuse legitimate services like file-hosting services and business profile pages to avoid detection,” Microsoft said in a report shared…
-
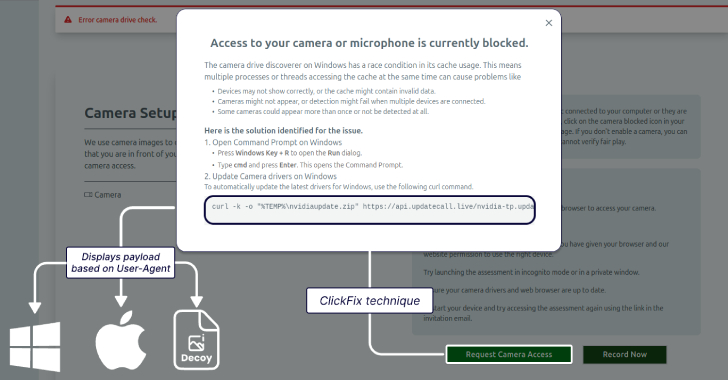
Lazarus Group Targets Job Seekers With ClickFix Tactic to Deploy GolangGhost Malware [email protected] (The Hacker News)
The North Korean threat actors behind Contagious Interview have adopted the increasingly popular ClickFix social engineering tactic to lure job seekers in the cryptocurrency sector to deliver a previously undocumented Go-based backdoor called GolangGhost on Windows and macOS systems. The new activity, assessed to be a continuation of the campaign, has been codenamed ClickFake Interview…
-

AI Threats Are Evolving Fast — Learn Practical Defense Tactics in this Expert Webinar [email protected] (The Hacker News)
The rules have changed. Again. Artificial intelligence is bringing powerful new tools to businesses. But it’s also giving cybercriminals smarter ways to attack. They’re moving quicker, targeting more precisely, and slipping past old defenses without being noticed. And here’s the harsh truth: If your security strategy hasn’t evolved with AI in mind, you’re already behind.…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
