“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
AI Adoption in the Enterprise: Breaking Through the Security and Compliance Gridlock [email protected] (The Hacker News)
AI holds the promise to revolutionize all sectors of enterpriseーfrom fraud detection and content personalization to customer service and security operations. Yet, despite its potential, implementation often stalls behind a wall of security, legal, and compliance hurdles. Imagine this all-too-familiar scenario: A CISO wants to deploy an AI-driven SOC to handle the overwhelming volume of…
-
4 ransomware detection techniques to catch an attack
While prevention is key, it’s not enough to protect a company’s systems from ransomware. Learn how early detection with these four methods helps reduce damage from attacks.Read More
-

Google Patches Quick Share Vulnerability Enabling Silent File Transfers Without Consent [email protected] (The Hacker News)
Cybersecurity researchers have disclosed details of a new vulnerability impacting Google’s Quick Share data transfer utility for Windows that could be exploited to achieve a denial-of-service (DoS) or send arbitrary files to a target’s device without their approval. The flaw, tracked as CVE-2024-10668 (CVSS score: 5.9), is a bypass for two of the 10 shortcomings…
-

Triada Malware Preloaded on Counterfeit Android Phones Infects 2,600+ Devices [email protected] (The Hacker News)
Counterfeit versions of popular smartphone models that are sold at reduced prices have been found to be preloaded with a modified version of an Android malware called Triada. “More than 2,600 users in different countries have encountered the new version of Triada, the majority in Russia,” Kaspersky said in a report. The infections were recorded…
-

Legacy Stripe API Exploited to Validate Stolen Payment Cards in Web Skimmer Campaign [email protected] (The Hacker News)
Threat hunters are warning of a sophisticated web skimmer campaign that leverages a legacy application programming interface (API) from payment processor Stripe to validate stolen payment information prior to exfiltration. “This tactic ensures that only valid card data is sent to the attackers, making the operation more efficient and potentially harder to detect,” Jscrambler researchers…
-

Europol Dismantles Kidflix With 72,000 CSAM Videos Seized in Major Operation [email protected] (The Hacker News)
In one of the largest coordinated law enforcement operations, authorities have dismantled Kidflix, a streaming platform that offered child sexual abuse material (CSAM). “A total of 1.8 million users worldwide logged on to the platform between April 2022 and March 2025,” Europol said in a statement. “On March 11, 2025, the server, which contained around…
-
Model Context Protocol fever spreads in cloud-native world
The Anthropic-led spec for AI agent tool connections gains further momentum this week, with support from cloud-native infrastructure vendors such as Kubiya and Solo.io.Read More
-
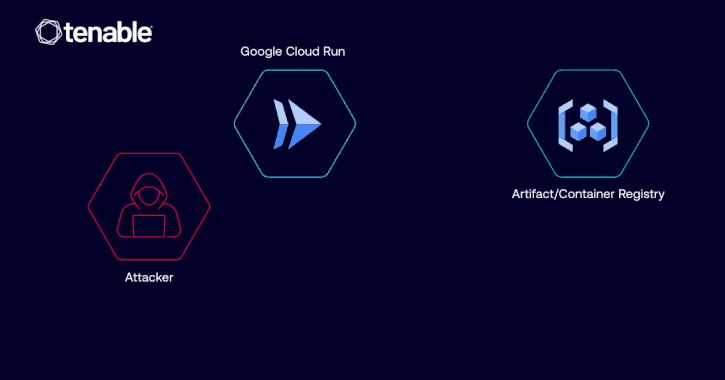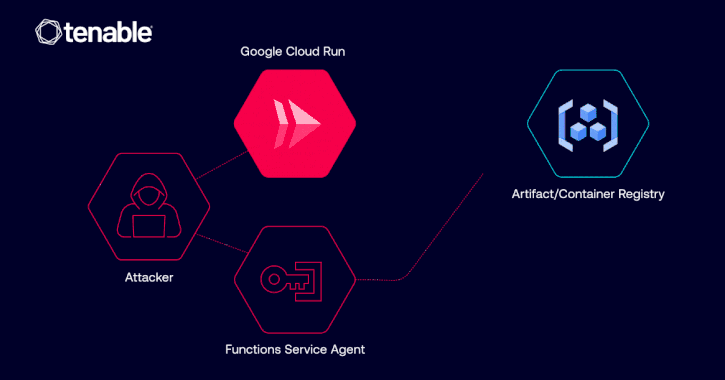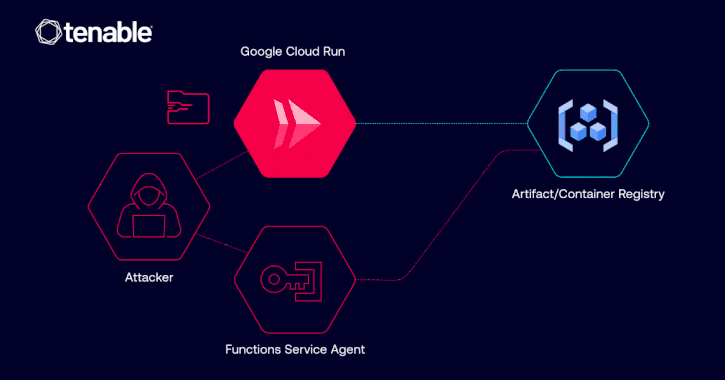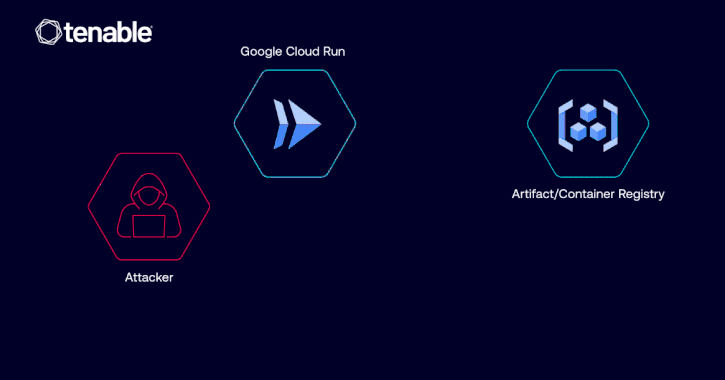
Google Fixed Cloud Run Vulnerability Allowing Unauthorized Image Access via IAM Misuse [email protected] (The Hacker News)
Cybersecurity researchers have disclosed details of a now-patched privilege escalation vulnerability in Google Cloud Platform (GCP) Cloud Run that could have allowed a malicious actor to access container images and even inject malicious code. “The vulnerability could have allowed such an identity to abuse its Google Cloud Run revision edit permissions in order to pull…
-

Helping Your Clients Achieve NIST Compliance: A Step by Step Guide for Service Providers [email protected] (The Hacker News)
Introduction As the cybersecurity landscape evolves, service providers play an increasingly vital role in safeguarding sensitive data and maintaining compliance with industry regulations. The National Institute of Standards and Technology (NIST) offers a comprehensive set of frameworks that provide a clear path to achieving robust cybersecurity practices. For service providers, adhering to NISTRead More
-

Outlaw Group Uses SSH Brute-Force to Deploy Cryptojacking Malware on Linux Servers [email protected] (The Hacker News)
Cybersecurity researchers have shed light on an “auto-propagating” cryptocurrency mining botnet called Outlaw (aka Dota) that’s known for targeting SSH servers with weak credentials. “Outlaw is a Linux malware that relies on SSH brute-force attacks, cryptocurrency mining, and worm-like propagation to infect and maintain control over systems,” Elastic Security Labs said in a new analysisRead…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
