Category: Uncategorized
-
What is cyber resilience?
Cyber resilience is the ability of a computing system to identify, respond to and recover quickly from a security incident.Read More
-

The Hidden Risks of SaaS: Why Built-In Protections Aren’t Enough for Modern Data Resilience [email protected] (The Hacker News)
SaaS Adoption is Skyrocketing, Resilience Hasn’t Kept Pace SaaS platforms have revolutionized how businesses operate. They simplify collaboration, accelerate deployment, and reduce the overhead of managing infrastructure. But with their rise comes a subtle, dangerous assumption: that the convenience of SaaS extends to resilience. It doesn’t. These platforms weren’t built with full-scale dataRead More
-
Top identity security themes at Identiverse 2025
Identiverse 2025 found security pros tackling nonhuman identity risks, preparing for agentic AI challenges and shifting from homegrown to commercial CIAM tools.Read More
-
10 key cybersecurity metrics and KPIs your board wants tracked
Security leaders need cybersecurity metrics to track their programs and inform decision-makers. These 10 metrics and KPIs provide a good foundation for tracking essential activity.Read More
-
Iranian APT35 Hackers Targeting Israeli Tech Experts with AI-Powered Phishing Attacks [email protected] (The Hacker News)
An Iranian state-sponsored hacking group associated with the Islamic Revolutionary Guard Corps (IRGC) has been linked to a spear-phishing campaign targeting journalists, high-profile cyber security experts, and computer science professors in Israel. “In some of those campaigns, Israeli technology and cyber security professionals were approached by attackers who posed as fictitious assistants toRead More
-
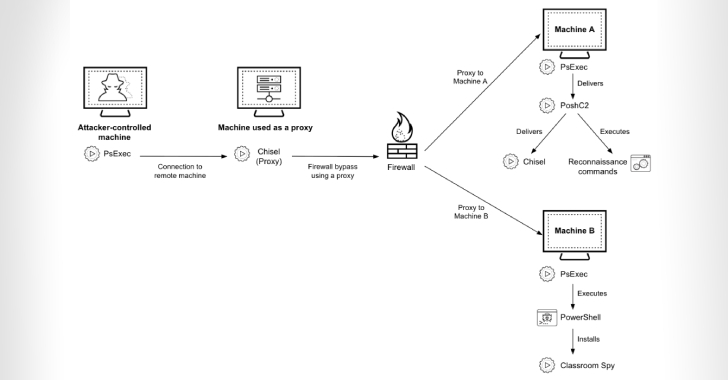
Cyber Criminals Exploit Open-Source Tools to Compromise Financial Institutions Across Africa [email protected] (The Hacker News)
Cybersecurity researchers are calling attention to a series of cyber attacks targeting financial organizations across Africa since at least July 2023 using a mix of open-source and publicly available tools to maintain access. Palo Alto Networks Unit 42 is tracking the activity under the moniker CL-CRI-1014, where “CL” refers to “cluster” and “CRI” stands for…
-

CISA Adds 3 Flaws to KEV Catalog, Impacting AMI MegaRAC, D-Link, Fortinet [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added three security flaws, each impacting AMI MegaRAC, D-Link DIR-859 router, and Fortinet FortiOS, to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The list of vulnerabilities is as follows – CVE-2024-54085 (CVSS score: 10.0) – An authentication bypass by spoofingRead…
-
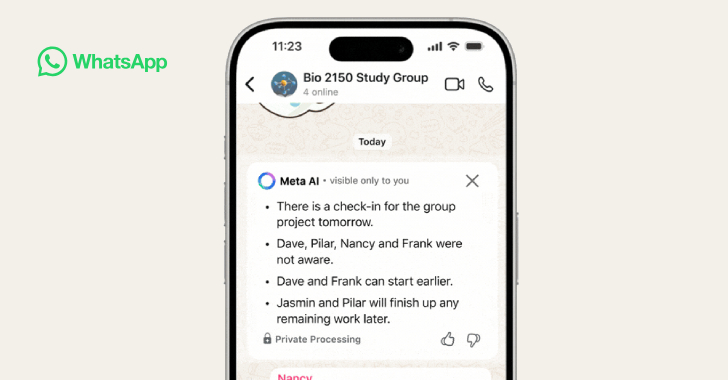
WhatsApp Adds AI-Powered Message Summaries for Faster Chat Previews [email protected] (The Hacker News)
Popular messaging platform WhatsApp has added a new artificial intelligence (AI)-powered feature that leverages its in-house solution Meta AI to summarize unread messages in chats. The feature, called Message Summaries, is currently rolling out in the English language to users in the United States, with plans to bring it to other regions and languages later…
-

nOAuth Vulnerability Still Affects 9% of Microsoft Entra SaaS Apps Two Years After Discovery [email protected] (The Hacker News)
New research has uncovered continued risk from a known security weakness in Microsoft’s Entra ID, potentially enabling malicious actors to achieve account takeovers in susceptible software-as-a-service (SaaS) applications. Identity security company Semperis, in an analysis of 104 SaaS applications, found nine of them to be vulnerable to Entra ID cross-tenant nOAuth abuse. First disclosed byRead…
-

Citrix Releases Emergency Patches for Actively Exploited CVE-2025-6543 in NetScaler ADC [email protected] (The Hacker News)
Citrix has released security updates to address a critical flaw affecting NetScaler ADC that it said has been exploited in the wild. The vulnerability, tracked as CVE-2025-6543, carries a CVSS score of 9.2 out of a maximum of 10.0. It has been described as a case of memory overflow that could result in unintended control…
