Category: Uncategorized
-
12 common types of malware attacks and how to prevent them
More than one billion active malware programs exist worldwide. Is your organization prepared to prevent these 12 types of malware attacks?Read More
-
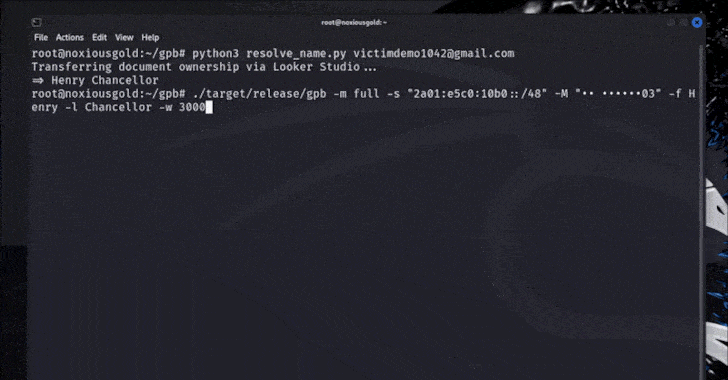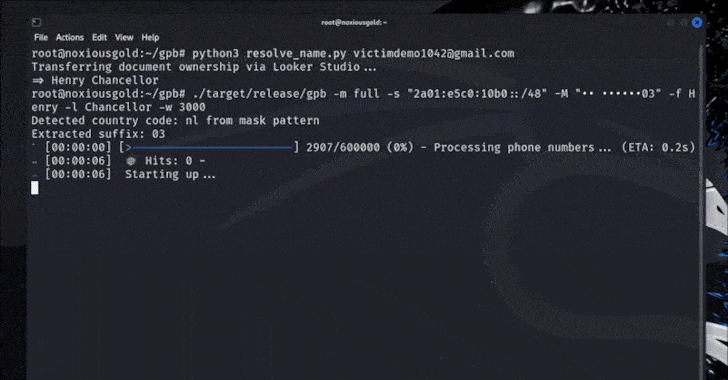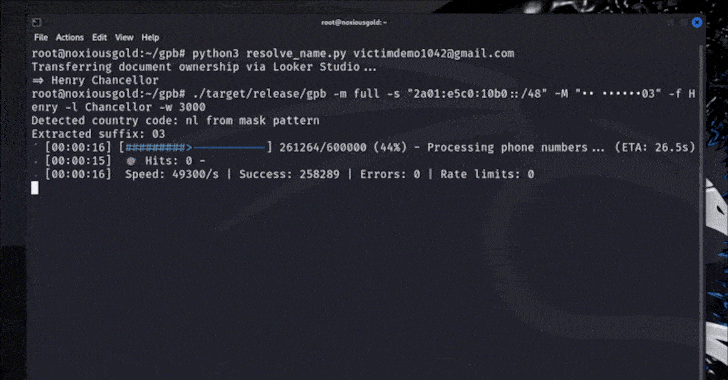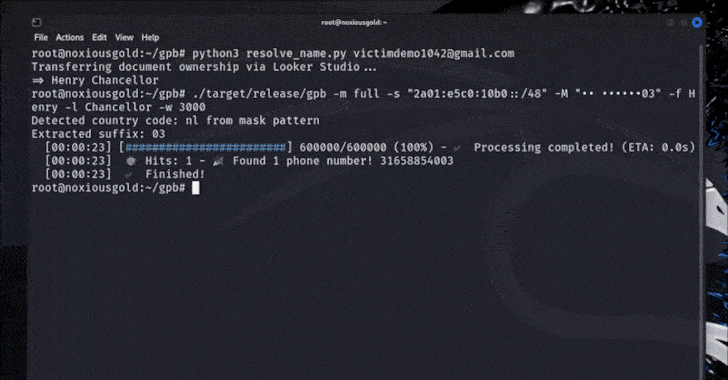
Researcher Found Flaw to Discover Phone Numbers Linked to Any Google Account [email protected] (The Hacker News)
Google has stepped in to address a security flaw that could have made it possible to brute-force an account’s recovery phone number, potentially exposing them to privacy and security risks. The issue, according to Singaporean security researcher “brutecat,” leverages an issue in the company’s account recovery feature. That said, exploiting the vulnerability hinges on several…
-
Symmetric vs. asymmetric encryption: Understand key differences
Explore the differences between symmetric vs. asymmetric encryption, including how they work and common algorithms, as well as their pros and cons.Read More
-

Rare Werewolf APT Uses Legitimate Software in Attacks on Hundreds of Russian Enterprises [email protected] (The Hacker News)
The threat actor known as Rare Werewolf (formerly Rare Wolf) has been linked to a series of cyber attacks targeting Russia and the Commonwealth of Independent States (CIS) countries. “A distinctive feature of this threat is that the attackers favor using legitimate third-party software over developing their own malicious binaries,” Kaspersky said. “The malicious functionality…
-

CISA Adds Erlang SSH and Roundcube Flaws to Known Exploited Vulnerabilities Catalog [email protected] (The Hacker News)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added two critical security flaws impacting Erlang/Open Telecom Platform (OTP) SSH and Roundcube to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerabilities in question are listed below – CVE-2025-32433 (CVSS score: 10.0) – A missing authentication for a criticalRead…
-

Over 70 Organizations Across Multiple Sectors Targeted by China-Linked Cyber Espionage Group [email protected] (The Hacker News)
The reconnaissance activity targeting American cybersecurity company SentinelOne was part of a broader set of partially-related intrusions into several targets between July 2024 and March 2025. “The victimology includes a South Asian government entity, a European media organization, and more than 70 organizations across a wide range of sectors,” security researchers Aleksandar Milenkoski and TomRead…
-
Two Distinct Botnets Exploit Wazuh Server Vulnerability to Launch Mirai-Based Attacks [email protected] (The Hacker News)
A now-patched critical security flaw in the Wazur Server is being exploited by threat actors to drop two different Mirai botnet variants and use them to conduct distributed denial-of-service (DDoS) attacks. Akamai, which first discovered the exploitation efforts in late March 2025, said the malicious campaign targets CVE-2025-24016 (CVSS score: 9.9), an unsafe deserialization vulnerability…
-

Two Distinct Botnets Exploit Wazuh Server Vulnerability to Launch Mirai-Based Attacks [email protected] (The Hacker News)
A now-patched critical security flaw in the Wazur Server is being exploited by threat actors to drop two different Mirai botnet variants and use them to conduct distributed denial-of-service (DDoS) attacks. Akamai, which first discovered the exploitation efforts in late March 2025, said the malicious campaign targets CVE-2025-24016 (CVSS score: 9.9), an unsafe deserialization vulnerability…
-

⚡ Weekly Recap: Chrome 0-Day, Data Wipers, Misused Tools and Zero-Click iPhone Attacks [email protected] (The Hacker News)
Behind every security alert is a bigger story. Sometimes it’s a system being tested. Sometimes it’s trust being lost in quiet ways—through delays, odd behavior, or subtle gaps in control. This week, we’re looking beyond the surface to spot what really matters. Whether it’s poor design, hidden access, or silent misuse, knowing where to look…
-

Think Your IdP or CASB Covers Shadow IT? These 5 Risks Prove Otherwise [email protected] (The Hacker News)
You don’t need a rogue employee to suffer a breach. All it takes is a free trial that someone forgot to cancel. An AI-powered note-taker quietly syncing with your Google Drive. A personal Gmail account tied to a business-critical tool. That’s shadow IT. And today, it’s not just about unsanctioned apps, but also dormant accounts,…
