Category: Uncategorized
-

U.S. Treasury Lifts Tornado Cash Sanctions Amid North Korea Money Laundering Probe [email protected] (The Hacker News)
The U.S. Treasury Department has announced that it’s removing sanctions against Tornado Cash, a cryptocurrency mixer service that has been accused of aiding the North Korea-linked Lazarus Group to launder their ill-gotten proceeds. “Based on the Administration’s review of the novel legal and policy issues raised by use of financial sanctions against financial and commercial…
-
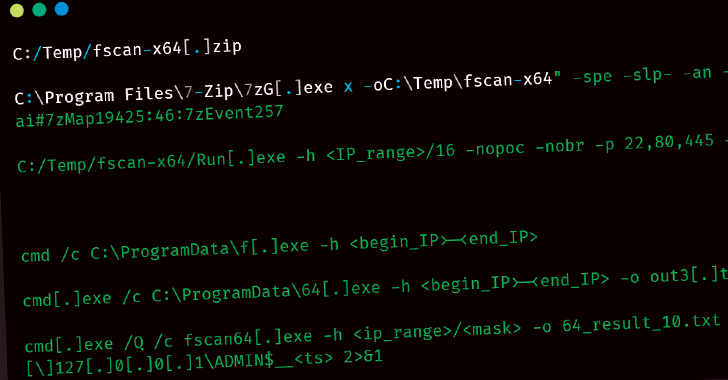
UAT-5918 Targets Taiwan’s Critical Infrastructure Using Web Shells and Open-Source Tools [email protected] (The Hacker News)
Threat hunters have uncovered a new threat actor named UAT-5918 that has been attacking critical infrastructure entities in Taiwan since at least 2023. “UAT-5918, a threat actor believed to be motivated by establishing long-term access for information theft, uses a combination of web shells and open-sourced tooling to conduct post-compromise activities to establish persistence in…
-

Medusa Ransomware Uses Malicious Driver to Disable Anti-Malware with Stolen Certificates [email protected] (The Hacker News)
The threat actors behind the Medusa ransomware-as-a-service (RaaS) operation have been observed using a malicious driver dubbed ABYSSWORKER as part of a bring your own vulnerable driver (BYOVD) attack designed to disable anti-malware tools. Elastic Security Labs said it observed a Medusa ransomware attack that delivered the encryptor by means of a loader packed using…
-

10 Critical Network Pentest Findings IT Teams Overlook [email protected] (The Hacker News)
After conducting over 10,000 automated internal network penetration tests last year, vPenTest has uncovered a troubling reality that many businesses still have critical security gaps that attackers can easily exploit. Organizations often assume that firewalls, endpoint protection, and SIEMs are enough to keep them secure. But how effective are these defenses when put to the…
-

China-Linked APT Aquatic Panda: 10-Month Campaign, 7 Global Targets, 5 Malware Families [email protected] (The Hacker News)
The China-linked advanced persistent threat (APT) group. known as Aquatic Panda has been linked to a “global espionage campaign” that took place in 2022 targeting seven organizations. These entities include governments, catholic charities, non-governmental organizations (NGOs), and think tanks across Taiwan, Hungary, Turkey, Thailand, France, and the United States. The activity, which took placeRead More
-

Kaspersky Links Head Mare to Twelve, Targeting Russian Entities via Shared C2 Servers [email protected] (The Hacker News)
Two known threat activity clusters codenamed Head Mare and Twelve have likely joined forces to target Russian entities, new findings from Kaspersky reveal. “Head Mare relied heavily on tools previously associated with Twelve. Additionally, Head Mare attacks utilized command-and-control (C2) servers exclusively linked to Twelve prior to these incidents,” the company said. “This suggestsRead More
-
Ongoing Cyber Attacks Exploit Critical Vulnerabilities in Cisco Smart Licensing Utility [email protected] (The Hacker News)
Two now-patched security flaws impacting Cisco Smart Licensing Utility are seeing active exploitation attempts, according to SANS Internet Storm Center. The two critical-rated vulnerabilities in question are listed below – CVE-2024-20439 (CVSS score: 9.8) – The presence of an undocumented static user credential for an administrative account that an attacker could exploit to log in…
-

YouTube Game Cheats Spread Arcane Stealer Malware to Russian-Speaking Users [email protected] (The Hacker News)
YouTube videos promoting game cheats are being used to deliver a previously undocumented stealer malware called Arcane likely targeting Russian-speaking users. “What’s intriguing about this malware is how much it collects,” Kaspersky said in an analysis. “It grabs account information from VPN and gaming clients, and all kinds of network utilities like ngrok, Playit, Cyberduck,…
-
13 API security best practices to protect your business
Post ContentRead More
-

Veeam and IBM Release Patches for High-Risk Flaws in Backup and AIX Systems [email protected] (The Hacker News)
Veeam has released security updates to address a critical security flaw impacting its Backup & Replication software that could lead to remote code execution. The vulnerability, tracked as CVE-2025-23120, carries a CVSS score of 9.9 out of 10.0. It affects 12.3.0.310 and all earlier version 12 builds. “A vulnerability allowing remote code execution (RCE) by…
