“Cyber warfare is as much about psychological strategy as technical prowess.”
― James Scott
-
Red vs. blue vs. purple team: What are the differences?
Red teams attack, blue teams defend and purple teams facilitate collaboration. Together, they strengthen cybersecurity through simulated exercises and knowledge sharing.Read More
-
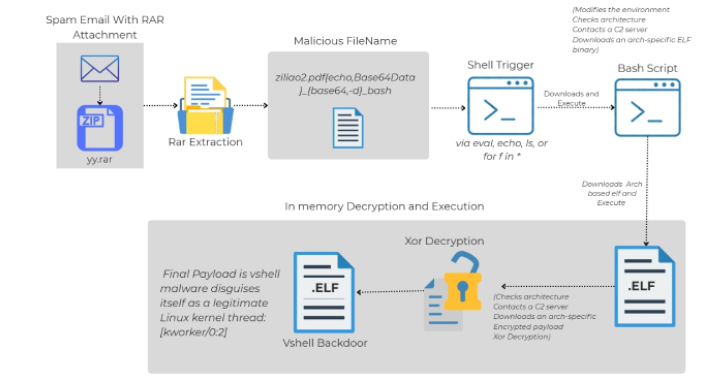
Linux Malware Delivered via Malicious RAR Filenames Evades Antivirus Detection [email protected] (The Hacker News)
Cybersecurity researchers have shed light on a novel attack chain that employs phishing emails to deliver an open-source backdoor called VShell. The “Linux-specific malware infection chain that starts with a spam email with a malicious RAR archive file,” Trellix researcher Sagar Bade said in a technical write-up. “The payload isn’t hidden inside the file content…
-
News brief: Safeguards emerge to address security for AI
Check out the latest security news from the Informa TechTarget team.Read More
-
10 common file-sharing security risks and how to prevent them
IT administrators must understand the top file-sharing security risks and how to ensure they don’t create vulnerabilities for the broader organization.Read More
-

Chinese Hackers Murky, Genesis, and Glacial Panda Escalate Cloud and Telecom Espionage [email protected] (The Hacker News)
Cybersecurity researchers are calling attention to malicious activity orchestrated by a China-nexus cyber espionage group known as Murky Panda that involves abusing trusted relationships in the cloud to breach enterprise networks. “The adversary has also shown considerable ability to quickly weaponize N-day and zero-day vulnerabilities and frequently achieves initial access to their targets byRead More
-
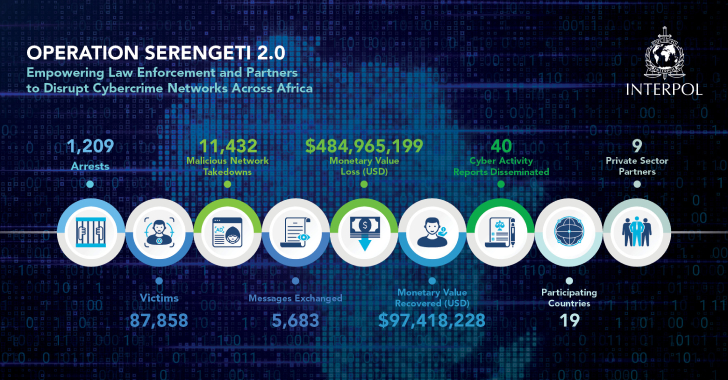
INTERPOL Arrests 1,209 Cybercriminals Across 18 African Nations in Global Crackdown [email protected] (The Hacker News)
INTERPOL on Friday announced that authorities from 18 countries across Africa have arrested 1,209 cybercriminals who targeted 88,000 victims. “The crackdown recovered $97.4 million and dismantled 11,432 malicious infrastructures, underscoring the global reach of cybercrime and the urgent need for cross-border cooperation,” the agency said. The effort is the second phase of an ongoing lawRead…
-

Automation Is Redefining Pentest Delivery [email protected] (The Hacker News)
Pentesting remains one of the most effective ways to identify real-world security weaknesses before adversaries do. But as the threat landscape has evolved, the way we deliver pentest results hasn’t kept pace. Most organizations still rely on traditional reporting methods—static PDFs, emailed documents, and spreadsheet-based tracking. The problem? These outdated workflows introduce delays,Read More
-
What is a SIM swap attack (SIM intercept attack)?
A SIM swap attack (SIM intercept attack) is a form of identity fraud in which the attacker transfers a user’s phone number to a different SIM card to gain access to the user’s phone calls, text messages, bank accounts, credit card numbers and other sensitive information.Read More
-

Ex-Developer Jailed Four Years for Sabotaging Ohio Employer with Kill-Switch Malware [email protected] (The Hacker News)
A 55-year-old Chinese national has been sentenced to four years in prison and three years of supervised release for sabotaging his former employer’s network with custom malware and deploying a kill switch that locked out employees when his account was disabled. Davis Lu, 55, of Houston, Texas, was convicted of causing intentional damage to protected…
-
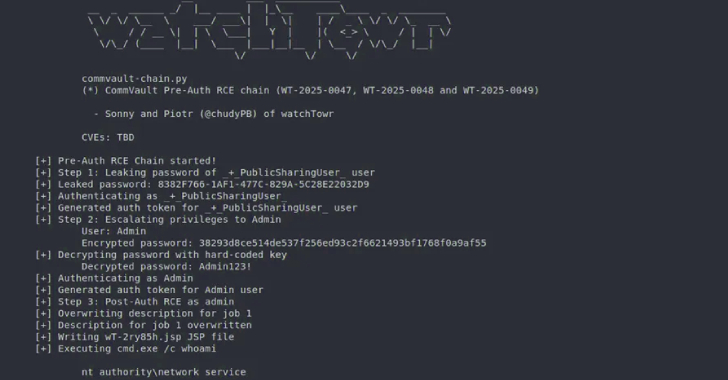
Pre-Auth Exploit Chains Found in Commvault Could Enable Remote Code Execution Attacks [email protected] (The Hacker News)
Commvault has released updates to address four security gaps that could be exploited to achieve remote code execution on susceptible instances. The list of vulnerabilities, identified in Commvault versions before 11.36.60, is as follows – CVE-2025-57788 (CVSS score: 6.9) – A vulnerability in a known login mechanism allows unauthenticated attackers to execute API calls without…
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
― Martina Navratilova
